GoldPickaxe: New Face-Scanning Trojan Threatens iOS and Android Users

Cybersecurity firm Group-IB has uncovered a new threat to mobile users dubbed ‘GoldPickaxe,’ a trojan employed by the Chinese threat group ‘GoldFactory’ to orchestrate social engineering attacks and potentially perpetrate banking fraud using deepfake technology.
GoldPickaxe, part of the broader GoldFactory malware suite that includes strains like ‘GoldDigger’ and ‘GoldKefu,’ targets both iOS and Android devices and has been observed primarily in phishing campaigns directed at users in the Asia-Pacific region, particularly Thailand and Vietnam.
The modus operandi of GoldPickaxe involves initiating phishing or smishing attacks via messaging platforms like LINE, with messages often masquerading as communications from local government authorities or services. Victims are enticed into downloading fraudulent apps, such as a counterfeit ‘Digital Pension’ app hosted on fake Google Play websites.
 Malicious app hosted on a fake Google Play website
Malicious app hosted on a fake Google Play website
Source: Group-IB
For iOS users, the attackers initially leveraged TestFlight URLs to distribute the malicious app, circumventing normal security reviews. Following Apple’s removal of the TestFlight app, they pivoted to distributing malicious Mobile Device Management (MDM) profiles, granting them control over compromised devices.
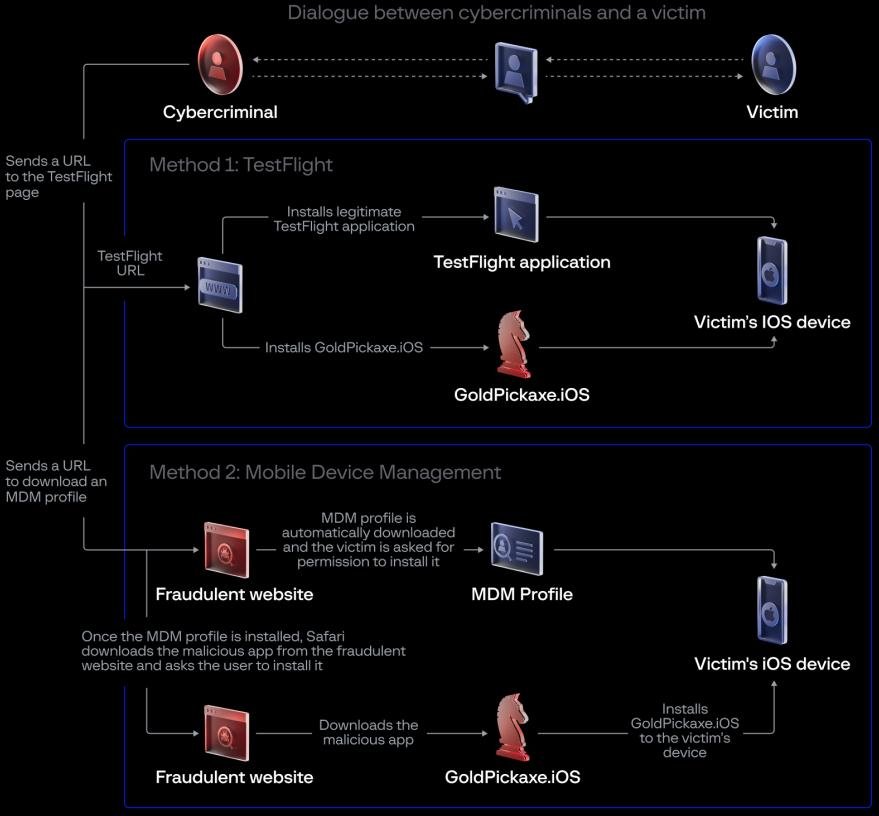 iOS infection chain
iOS infection chain
Source: Group-IB
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
GoldPickaxe’s Capabilities:
Once installed, GoldPickaxe operates surreptitiously, executing various functions in the background, including capturing the victim’s face, intercepting SMS messages, and proxying network traffic.
Notable capabilities include:
- Capturing face and ID document images
- Intercepting SMS messages
- Proxying network traffic using ‘MicroSocks’
- Uploading victim’s data to a cloud bucket
- Performing commands received from the command and control (C2) server
Android vs. iOS:
While GoldPickaxe exhibits more malicious behavior on Android due to Apple’s stricter security measures, both versions are concerning. On Android, the trojan utilizes over 20 different bogus apps for cover and can perform additional actions like accessing SMS, navigating the filesystem, and serving fake notifications.
 Face capturing interface
Face capturing interface
Source: Group-IB
Trending: Jeff Foley – OWASP Amass Founder
Trending: Recon Tool: go-dork


