Google PPC Ads Used to Deliver Infostealers

Reading Time: 2 Minutes
On Wednesday, breach prevention firm Morphisec posted an advisory in which it said that over the past month, it’s investigated the origins of paid ads that appear on the first page of search results and that lead to downloads of malicious AnyDesk, Dropbox and Telegram packages wrapped as ISO images.
This isn’t the first time we’ve seen a fake version of AnyDesk, the popular remote desktop application, pushed via ads appearing in Google search results. Just a week ago, we saw rigged AnyDesk ads serving up a trojanized version of the program. That earlier campaign even bested AnyDesk’s own ad campaign on Google, ranking higher in its paid results.
This time around, the Google PPC ads targeted specific IP ranges in the U.S. and “probably some other countries,” researchers wrote. Non-targeted IPs are redirected to legitimate pages that download the correct applications.
How These Attack Chains Work
The researchers investigated three attack chains that lead to Redline, Taurus and a new mini-Redline infostealer compromise. Two of the adversaries – the ones leveraging Taurus and mini-Redlineare – are using similar patterns, certificates, and command-and-control centers (C2s). The third uses Redline, while Morphisec plans to write up the Amadey campaign in a separate post.
See Also: Researchers Uncover Hacking Operations Targeting Government Entities in South Korea
Why Doesn’t Google Scanning Catch These?
Google says that it uses proprietary technology and malware detection tools to “regularly scan all creatives”, that it forbids ads when they try to call fourth parties or sub-syndication to uncertified advertisers, that it pulls ads distributing malware, and that authorized buyers whose ads are found to contain malware are placed on a minimum three-month suspension.
So how do these bad ads, funded through crooks spending real money on paid advertising, keep popping up at the top of search results? Threatpost reached out to Google to ask. In the meantime, Morphisec’s investigation revealed that the unpacked Redline malware “will confuse even the biggest security vendors,” using obfuscation techniques described below. In a nutshell, these attacks have succeeded because crooks spend real money on Google AdWords, having figured out how to evade Google’s malvertising screening and having set up a website with a signed, legitimate certificate – as in, a maximum of two weeks old – designed to mislead website visitors.
Obfuscation Galore
As researchers described it, all of the attacks start with one of a dozen paid Google ads that lead to a website with an ISO image download – one that’s big enough to slip past scanning. “The ISO image size is larger than 100MB, which allows the image to evade some scanning solutions that are optimized on throughput and size,” they explained. “Mounting the ISO image leads to executables that are usually, but not always, digitally signed and legitimately verified.”
Adversary One dumps the Redline infostealer. It obfuscates .Net executables with known obfuscators, including DeepSea. That leads to a custom obfuscated .Net DLL loader that eventually leads to a custom obfuscated Redline stealer .Net executable, they continued.
For its part, Adversary Two delivers Taurus and a mini-Redline infostealer that has some common functionality for stealing browser data and that wraps four layers of obfuscation around its configuration and communication patterns. As for the Taurus AutoIt infostealer, its executables recreate and execute a legitimate AutoIt compiler with a malicious AutoIt script and a malicious encrypted Taurus executable that will be hollowed into the AutoIt process, the researchers wrote.
See Also: OSINT Tool: LinkedIn Scraper
Bad Ads Pop Up in Tip-Top Search Results
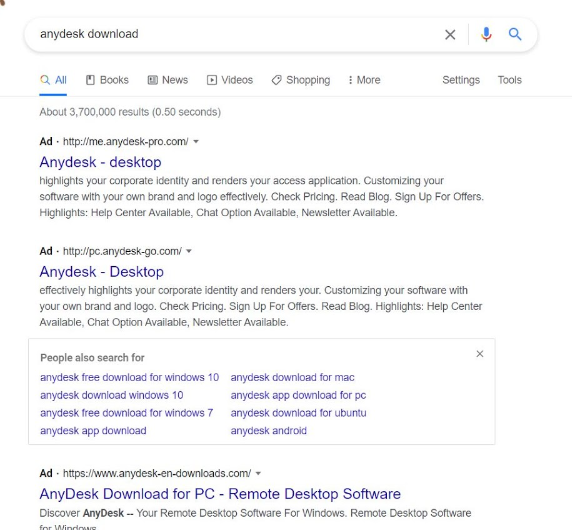
Morphisec researchers found that a simple search for “anydesk download” led them to three pay-per-click Google ads, all of which led to malicious infostealers, as shown in the image below. The first two ads lead to a Redline stealer, while the third leads to the Taurus infostealer.
Three pay-per-click Google ads returned as top results in a search for “anydesk download”. All three lead to malicious infostealers. Source: Morphisec
Redline Infostealer
The Redline infostealer websites are signed by a Sectigo certificate. Clicking on the download button on any of the websites leads to a script execution that verifies the IP and delivers the artifacts from the remote website hxxps://desklop.pc-whatisapp[.]com/. Those artifacts – a zip file and three ISO files – get updated and re-uploaded to the site every few days. The researchers explained that each ISO file includes a very small .Net executable that, in some cases, is also digitally signed.
The executable’s first layer is obfuscated with DeepSea, the second layer is a custom obfuscated .Net DLL that executes in memory, while the third layer is the well-known Redline infostealer, which communicates back with jasafodidei[.]xyz:80.
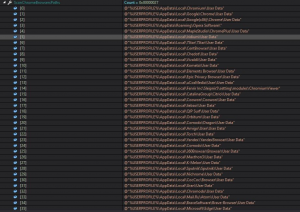
Morphisec provided a snapshot showing all of the databases that Redline targets – a collection that shows that the infostealer, surprisingly, targets browsers that are also used in Russian-speaking countries. Many malware strains spare such countries.
Taurus Infostealer
The Taurus infostealer is delivered similarly, appearing as the third paid ad in a search for the popular AnyDesk, Dropbox and Telegram applications. This time, the website for the Taurus infostealer is signed with a legitimate, fresh Cloudflare certificate, but again, it’s no older than two weeks.
There were no redirects to websites in the Taurus case. Instead, the download results from a submitted form that’s handled by “get.php” and which then delivers the ISO image directly from the website.
If the target isn’t within the range of the IP addresses that the infostealer is after, users will instead see a normal redirect to the legitimate application website, similar to what happens with the Redline infostealer. If the target’s IP is in a sweet spot, it will download an ISO image with a self-extracting archive (SFX).
This one’s a 7-Zip SFX (7z) archive: a stand-alone Windows .exe program file that can unpack an archive that’s been created with the open-source 7-Zip software without actually needing 7-Zip or any other tools. It starts the execution from the first batch file, masquerading as either .flv, .bmp or any other unique extension. The batch script is then redirected as input into cmd.exe.
Those 7z SFX archives get around: Researchers said that a VirusTotal search for such archives that have similar evasion techniques leads to more than 400 uploaded in the past month. It won’t execute it if it detects a known sandbox provider.
Morphisec researchers said that it also implements persistence through a URL link directly in the startup folder. “The link executes Javascript from a hidden folder under roaming (use attrib -H to unhide),” they wrote. The Javascript file executes the AutoIt compiler with the copied Taurus AutoIt script.
See Also: Jeff Moss, aka Dark Tangent, the person who founded DEF CON and Black Hat
Mini-Redline Infostealer
Similar to the Taurus campaign, the ad websites that lead to the mini-Redline infostealer are also signed with Cloudflare certificates. In this case, for evasion purposes, the threat actors padded the ISO file with zeros to increase the file size.
The executable this time is a .Net assembly with an unknown obfuscation pattern that’s hidden by four layers of obfuscation and hollowing. The fourth layer leads to known stealing functionalities that, in an initial static look, is reminiscent of Redline. “Not surprisingly a VT scan for the unpacked file shows that it will confuse even the biggest security vendors,” researchers observed. “The method and strings implemented as part of the Chrome credential theft are almost identical. In both cases, the databases are copied to a temporary location before being decrypted, using similar methods and class names to do so even though the number of targeted browsers is minimal.”
It uses a different communication channel, though: Mini-Redline uses a direct TCP socket connection. Researchers found that the anti-debugging functionalities include “DebuggerHidden” attributes and virtualization detection.
Mini-Redline also uses Windows Management Instrumentation (WMI) to run Virtual Environment evasion checks.
Threat Actors Don’t Mind Ponying Up the Cash
Morphisec’s Michael Gorelik wrapped up the advisory by noting that “Adversaries will use any method possible to gather targets, even paying Google top dollar for their paid search results to surface a malicious website as a top search result.”
Threat actors’ resourcefulness means that “organizations need to be constantly vigilant in all aspects of their operations. There’s no telling when an adversary will set up a website with a signed, legitimate certificate designed to mislead website visitors,” he wrote.
“Threat actors are even clearly willing to pay substantial sums of money to target possible victims,” he continued. He pointed to Google Adwords data between May 2020 and April 2021 showing a bid price of between $0.42 and $3.97 for the two keywords “anydesk” and “anydesk download.”
“Assuming a click-through rate of 1,000 people, this could result in fees anywhere from $420 to $3,970 for even a small campaign that targets the U.S., for example” he observed.
Blame the Ad Behemoth?
Dirk Schrader, global vice president of security research at cybersecurity and compliance software company New Net Technologies (NNT), said that as long as they aren’t managed well, systems with as broad a reach as Google’s advertising infrastructure – or, for that matter, Apple’s App Store – will keep putting end users in danger. In April, a kids’ game called “Jungle Run” that was available in the Apple App store in reality turned out to be a cryptocurrency-funded casino set up to scam people out of money.
Is having a big enough ISO file really all that’s needed to evade detection? If so, that’s a bad look for Google, Schrader said. “In this case, if the simple evasion technique was to have a large enough ISO file and to pay more for the ad than the actual manufacturer to get a higher rank, that management was negligent,” he told Threatpost via email on Thursday. “Whenever something is optimized (for speed in this case), there is a need to define what should be done with some outlier corner cases. It seems that the optimization decisions made by Google opened an attack vector based on such an outlier.”
Schrader suggested that those businesses that have downloaded and installed a malicious package should do a sweep on their infrastructure to identify any additional backdoor established. They should also monitor any malicious changes that would indicate that an attacker still has access, he advised.
Malvertisements Are Way Too Easy
Joseph Neumann, a cyber executive advisor at Coalfire, said that these malvertisements aren’t sophisticated attacks. “It is fairly simple to take a legitimate program and pack it with malicious payloads, pay an ad hosting provider and post the content,” he told Threatpost via email on Thursday.
Even if they were tough to pull off, paying high enough wages gets you the talent you need to pull off these attacks, he said: “Like any cybersecurity talent, enough money is going to lure away the best talent, and sophistication is only going to increase.”
Should we even be reporting on these attacks? “Adversaries are getting more successful every day and continue to have payouts,” Neumann mulled. “With this media fame it is only going to fuel the flames for more brazen and sophisticated attacks.”
Source: threatpost.com