GTPDOOR: The Stealthy Linux Backdoor Targeting Telecom Networks

In a recent revelation, security researcher HaxRob has uncovered a previously unknown Linux backdoor named GTPDOOR, meticulously crafted for clandestine operations within mobile carrier networks.
Believed to be orchestrated by threat actors targeting systems adjacent to the GPRS Roaming Exchange (GRX), such as SGSN, GGSN, and P-GW, GTPDOOR provides direct access to a telecom’s core network, posing a significant threat to telecommunications infrastructure.
GRX, an integral component facilitating data roaming services across diverse networks and geographical areas, hosts these crucial systems, each playing distinct roles in mobile communications.
With the SGSN, GGSN, and P-GW networks more exposed to the public eye, with IP addresses readily available in public documents, they become prime targets for initial access into a mobile operator’s network, as explained in HaxRob’s detailed analysis.
I recently found two very interesting Linux binaries uploaded to Virustotal.
I call this malware 'GTPDOOR'.
GTPDOOR is a 'magic/wakeup' packet backdoor that uses a novel C2 transport protocol: GTP (GPRS Tunnelling Protocol), silently listening on the GRX network (1/n) 🧵 pic.twitter.com/IwuEcL14lx
— HaxRob (@haxrob) February 28, 2024
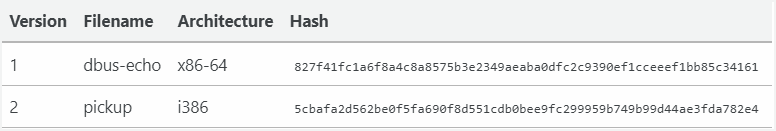
Attributed to the ‘LightBasin’ threat group (UNC1945), known for its intelligence-collection operations targeting telcos worldwide, GTPDOOR was discovered in two versions uploaded to VirusTotal in late 2023, evading detection by antivirus engines. The backdoor specifically targeted an outdated version of Red Hat Linux, hinting at its intended vulnerabilities.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
GTPDOOR: A Stealthy Threat
GTPDOOR, a sophisticated backdoor malware, capitalizes on the GPRS Tunnelling Protocol Control Plane (GTP-C) for covert command and control (C2) communications. Specifically designed for deployment in Linux-based systems neighboring the GRX, GTPDOOR seamlessly integrates with legitimate network traffic, utilizing unmonitored ports for stealthy operations.
The malware’s ability to modify its process name to mimic legitimate system processes further enhances its covert nature. It awaits specific GTP-C echo request messages, known as “magic packets,” to activate and execute commands, subsequently relaying outputs to its operators.
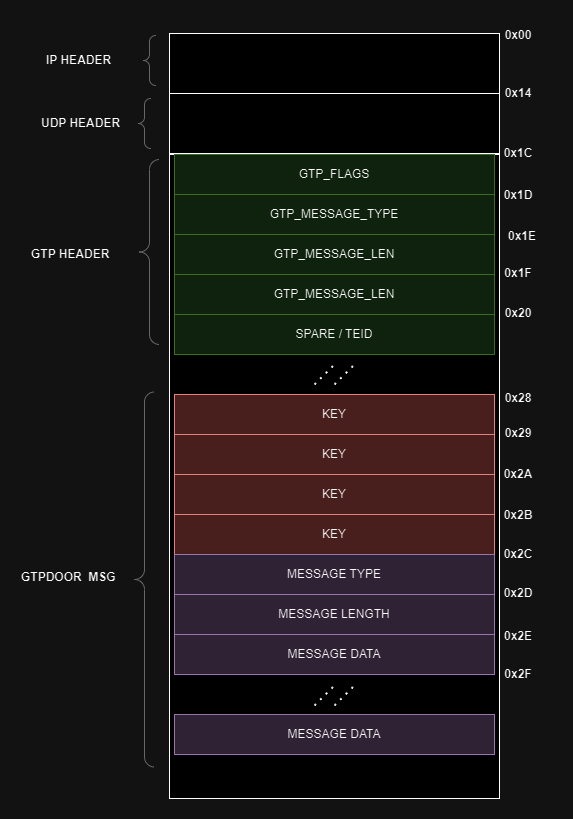 Malicious packet structure (doubleagent.net)
Malicious packet structure (doubleagent.net)
Malicious Packet Structure
The content within the magic GTP packets is both authenticated and encrypted using a simple XOR cipher, ensuring only authorized operators can control the malware.
GTPDOOR’s functionalities include setting new encryption keys, writing arbitrary data to local files, executing shell commands, and sending back results. Version 2 introduces additional capabilities, such as specifying allowed IP addresses or subnets and dynamically adjusting network permissions.
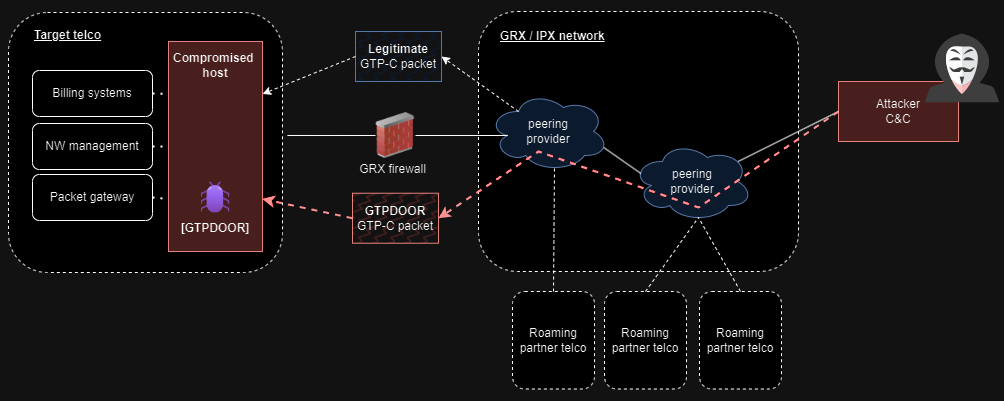 GTPDOOR attack overview (doubleagent.net)
GTPDOOR attack overview (doubleagent.net)
Trending: Offensive Security Tool: Upload_Bypass


