Hackers Employ ZeroFont Trick in Phishing Emails to Bypass Security Checks

Cybercriminals have begun employing a novel phishing technique known as “ZeroFont” to deceive users and evade email security measures, specifically in Microsoft Outlook.While the ZeroFont method itself is not new, this marks the first documented instance of its use in this manner, potentially enhancing the effectiveness of phishing attacks. Users are urged to stay informed about this technique and exercise caution when encountering suspicious emails.
ZeroFont attacks
The ZeroFont attack technique exploits vulnerabilities in how email security platforms analyze text, particularly through artificial intelligence (AI) and natural language processing (NLP) systems. It involves inserting hidden words or characters within emails by setting the font size to zero. While these characters remain invisible to human recipients, they remain legible to NLP algorithms.
The primary objective of this attack is to bypass security filters by inserting concealed benign terms within emails. These hidden terms blend with potentially suspicious visible content, causing confusion in AI’s interpretation of the message and the outcomes of security checks.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The technique initially came to light in 2018 when Avanan documented its usage. At that time, Avanan warned that ZeroFont was capable of bypassing Microsoft’s Office 365 Advanced Threat Protection (ATP), even when emails contained known malicious keywords.
In a recent phishing email analyzed by ISC Sans analyst Jan Kopriva, threat actors leveraged the ZeroFont technique to manipulate email previews in popular email clients like Microsoft Outlook. In this instance, the email displayed different content in Outlook’s email listing compared to the preview pane.
For example, the email listing in Outlook read, “Scanned and secured by Isc®Advanced Threat protection (APT): 9/22/2023T6:42 AM,” while the beginning of the email displayed “Job Offer | Employment Opportunity” in the preview/reading pane.
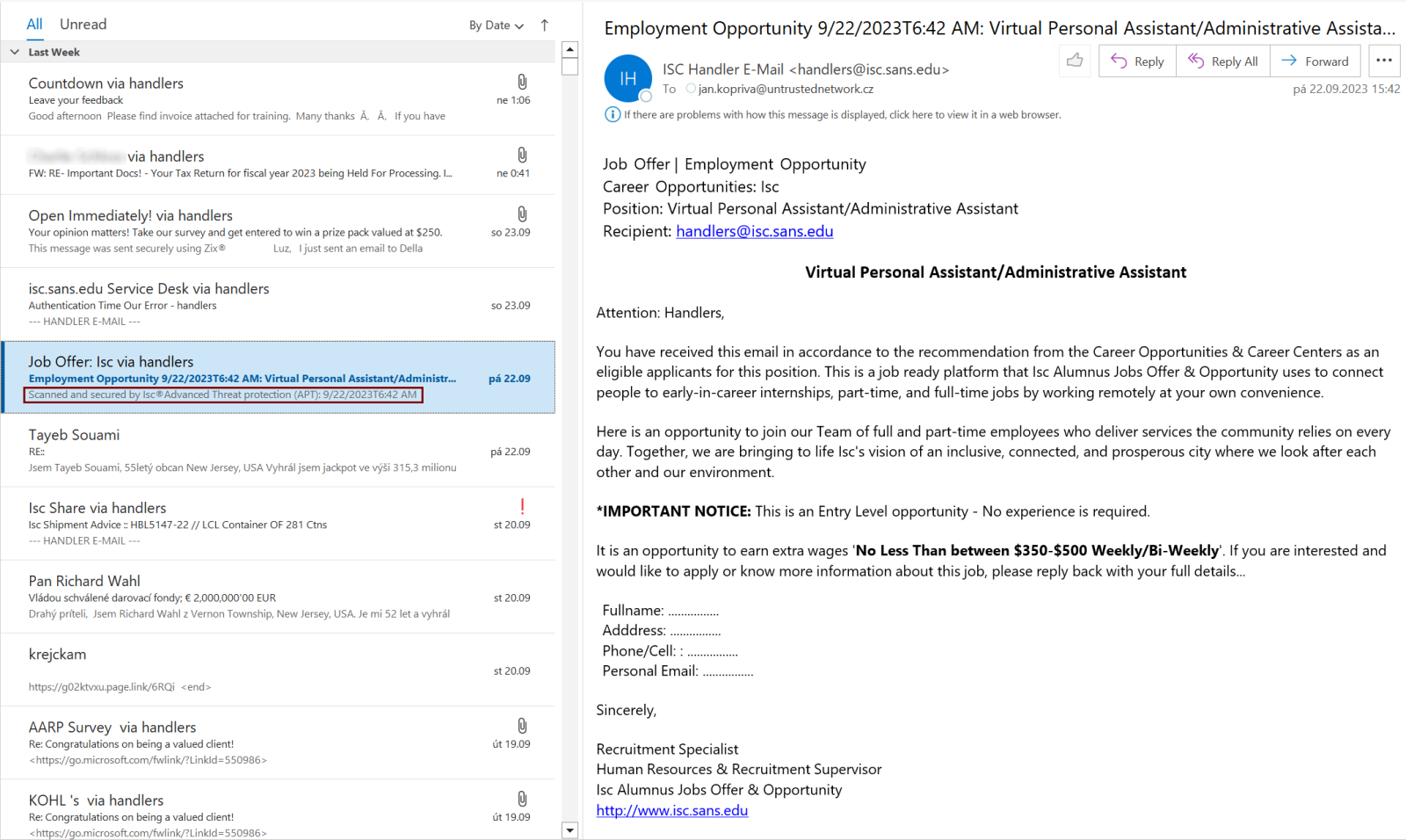 Malicious phishing message (isc.sans.edu)
Malicious phishing message (isc.sans.edu)
This discrepancy was achieved by using ZeroFont to conceal the fabricated security scan message at the start of the phishing email. While invisible to the recipient, Outlook still captured this text and displayed it as a preview in the email listing pane.
Trending: Recon Tool: Goblyn
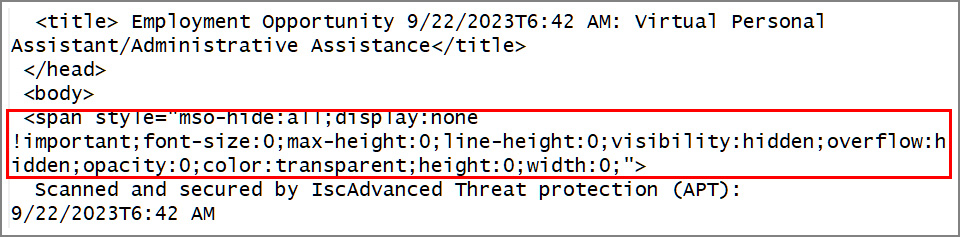
Zero-font attack hiding antivirus scan message
Source: ISC Sans
The objective behind this deceptive tactic is to create a false sense of legitimacy and security for the recipient. By presenting a fictitious security scan message, cybercriminals increase the likelihood of the target opening the email and engaging with its content.
It is worth noting that Outlook may not be the only email client susceptible to this manipulation. Other email software may also retrieve the initial portion of an email for preview without verifying the font size, emphasizing the importance of user vigilance across various platforms.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












