Hackers Exploit Godot Game Engine with New Malware, Infecting 17,000 Systems in 3 Months

Hackers have weaponized the widely-used Godot game engine to launch the GodLoader malware, infecting over 17,000 devices in just three months. This malware exploits Godot’s scripting capabilities to evade detection and execute malicious code, impacting users on major platforms, including Windows, macOS, Linux, Android, and iOS.
Attack Overview
Check Point Research uncovered that GodLoader leverages Godot’s GDScript scripting language and .pck files (used to package game assets) to embed malicious scripts. Once executed, these files unleash malware that can:
- Steal credentials.
- Deploy additional payloads like the XMRig crypto miner, which generated over 200,000 visits to its Pastebin configuration file.
“Cybercriminals have exploited the Godot Engine since June 2024 to execute crafted GDScript code, delivering malware in a way that bypasses most antivirus tools,” says Check Point, highlighting the malware’s stealth capabilities.
Offensive Security, Bug Bounty Courses
Attack Chain
The malware is distributed via the Stargazers Ghost Network, a Malware Distribution-as-a-Service (DaaS) platform, using seemingly legitimate GitHub repositories. Key details of the campaign include:
- 200+ malicious GitHub repositories managed by over 225 Stargazer Ghost accounts.
- Four distinct attack waves between September 12 and October 3, 2024 targeting developers and gamers.
- GitHub repositories forked and starred to appear on the trending section, increasing their perceived legitimacy.
Stargazer Goblin, the threat actor behind Stargazers Ghost Network, has operated this DaaS since at least August 2022, earning more than $100,000 by distributing malware like RedLine, Lumma Stealer, and Atlantida Stealer.
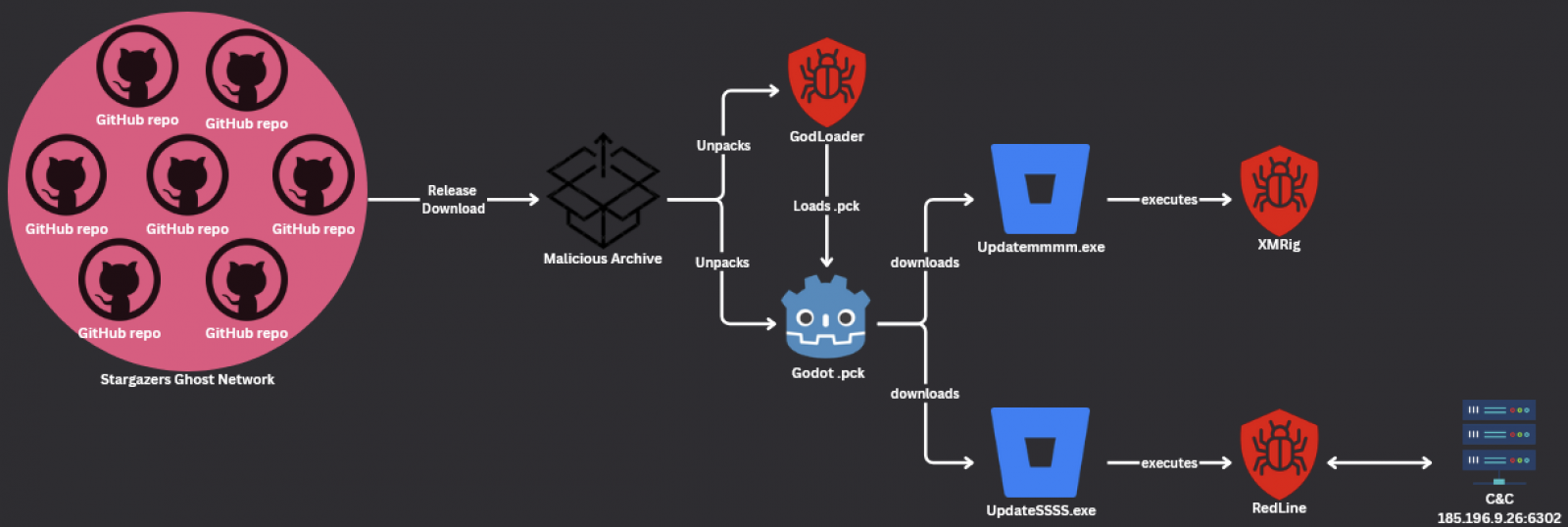 Attack chain (Check Point)
Attack chain (Check Point)
Exploiting Godot Engine
While GodLoader primarily targets Windows systems, Check Point developed a proof-of-concept exploit to demonstrate its adaptability for Linux and macOS. However, Rémi Verschelde, a Godot Engine maintainer, clarified that the vulnerability is not inherent to Godot:
“The Godot Engine is a programming system with a scripting language, similar to Python or Ruby. Users must explicitly execute malicious files with the Godot runtime for an attack to occur.”
Godot does not automatically handle .pck files, meaning attackers must bundle their malicious payload with the runtime. As a result, these attacks require victims to manually unpack and run the files, making widespread exploitation more challenging than one-click malware.
Trending: Recon Tool: emailFinder
Protecting Against GodLoader
To safeguard against this campaign:
- Download software only from trusted sources and verify the origin of game assets or tools.
- Avoid running unverified
.pckfiles or unpacking bundles without understanding their contents. - Developers should review GitHub repositories for suspicious activity or inconsistent commit histories.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













