Hackers Exploit Zero-Day in Cleo MFT Software, Enabling RCE and Data Theft

Hackers are exploiting a zero-day vulnerability in Cleo’s managed file transfer (MFT) software to breach corporate networks and conduct data theft attacks.
The Vulnerability
The flaw affects Cleo’s widely-used secure file transfer products, including LexiCom, VLTrader, and Harmony, and enables unrestricted file upload and downloads, leading to remote code execution (RCE).
The vulnerability, a bypass of a previous fix for CVE-2024-50623, impacts versions 5.8.0.21 and earlier. Cleo initially patched CVE-2024-50623 in October 2024, but the fix was incomplete, leaving systems open to exploitation.
Attack Scope
Cleo’s software is used by 4,000 companies worldwide, including prominent names like Target, Walmart, CVS, FedEx, and The Home Depot, among others. Security researchers have identified Termite ransomware gang as a possible actor leveraging this zero-day, reminiscent of previous exploits by the Clop ransomware group targeting MFT tools like MOVEit Transfer and Accellion FTA servers.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Exploitation in the Wild
The active exploitation was first identified by Huntress researchers, who observed attackers writing files such as healthchecktemplate.txt into the autorun directory of Cleo endpoints. These files exploit built-in import functionalities to:
- Deploy XML payloads containing PowerShell commands.
- Make remote callbacks to attacker-controlled IPs.
- Download additional payloads (e.g., JAR files).
- Clean up traces to hinder forensic investigation.
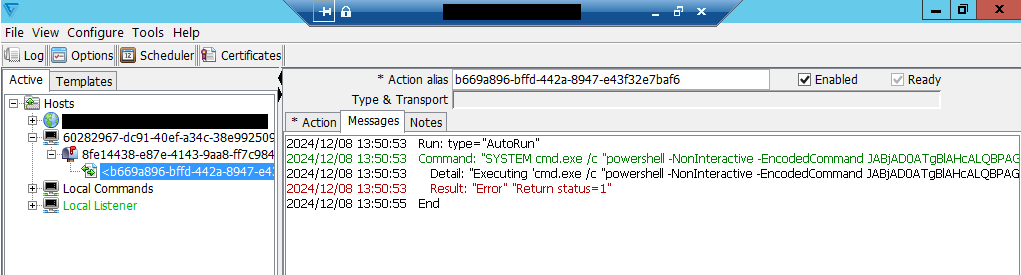 Exploit executing PowerShell commands on vulnerable devices
Exploit executing PowerShell commands on vulnerable devices
Source: Huntress
IP Addresses Associated with the Attacks:
- 176.123.5.126 – Moldova
- 5.149.249.226 – Netherlands
- 185.181.230.103 – Moldova
- 209.127.12.38 – Canada
- 181.214.147.164 – Lithuania
- 192.119.99.42 – United States
Huntress telemetry reveals that at least 10 organizations across industries like consumer goods, food, and shipping have been impacted, with the majority of vulnerable servers located in the United States.
Trending: Recon Tool: Argus
Mitigation and Recommendations
As the current patch (version 5.8.0.21) is ineffective, users must take immediate steps:
Restrict Access:
- Move Cleo systems behind a firewall and limit internet exposure.
- Review system logs for suspicious PowerShell execution and unknown XML files.
Check for Malicious Artifacts:
- Inspect directories (
C:\LexiCom,C:\VLTrader,C:\Harmony) for files likehealthcheck.txtormain.xml. - Remove suspicious JAR files (e.g.,
cleo.####.jar).
- Inspect directories (
Disable Autorun:
- Open Cleo application (LexiCom, VLTrader, or Harmony).
- Navigate to Configure > Options > Other Pane.
- Clear the Autorun Directory field and save changes.
Prepare for Updates:
- Monitor Cleo’s security bulletin page for the release of the forthcoming patch
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













