Hackers steal Microsoft Exchange credentials using IIS module

Reading Time: 1 Minute
Threat actors are installing a malicious IIS web server module named ‘Owowa’ on Microsoft Exchange Outlook Web Access servers to steal credentials and execute commands on the server remotely.
The development of Owowa likely started in late 2020 based on compilation data and when it was uploaded to the VirtusTotal malware scanning service.
Based on Kaspersky’s telemetry data, the most recent sample in circulation is from April 2021, targeting servers in Malaysia, Mongolia, Indonesia, and the Philippines.
These systems belong to government organizations, public transportation companies, and other crucial entities.
Kaspersky underlines that the ‘Owowa’ targets aren’t limited to Southeast Asia, and they have also seen signs of infections in Europe.
.png)
Source: Kaspersky
An uncommon backdoor
Microsoft Exchange servers are commonly targeted with web shells that allow threat actors to remotely execute commands on a server and are usually the focus of defenders.
As such, using an IIS module as a backdoor is an excellent way to stay hidden. The actors can send seemingly innocuous authentication requests to OWA, evading standard network monitoring rules as well.
“IIS modules are not a common format for backdoors, especially when compared to typical web application threats like web shells and can therefore easily be missed during standard file monitoring efforts.” explains the report by Kaspersky.
Additionally, the implant persists even after the Exchange software is updated, so the infection needs to take place only once.
Kaspersky comments that the actor may rely on ProxyLogon flaws to compromise the server, which remains a problem even after being patched nine months ago.
However, the actors didn’t do a perfect job with Owowa’s development, failing to hide PDB paths in the malware executable and causing server crashes in some cases.
Powerful capabilities
Owowa specifically targets OWA applications of Exchange servers and is designed to log the credentials of users that successfully authenticate on the OWA login web page.
The login success is automatically validated by monitoring the OWA application to generate an authentication token.
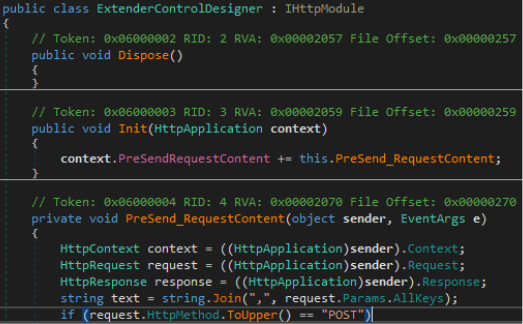
Source: Kaspersky
If that happens, Owowa stores the username, password, user IP address, and the current timestamp and encrypts the data using RSA.
The actor can then collect the stolen data by manually sending a command to the malicious module.
Remote commands may also be used for executing PowerShell on the compromised endpoint, opening the way to a range of attack possibilities.
“The cyber criminals only need to access the OWA login page of a compromised server to enter specially crafted commands into the username and password fields,” – explains Kaspersky.
“This is an efficient option for attackers to gain a strong foothold in targeted networks by persisting inside an Exchange server.”
See Also: Offensive Security Tool: Cobalt Strike
Detect and remove the IIS module
Admins can use the command ‘appcmd.exe’ or the IIS configuration tool to get a list of all loaded modules on an IIS server.
In the cases seen by the researchers, the malicious module uses the name “ExtenderControlDesigner,” as shown below.
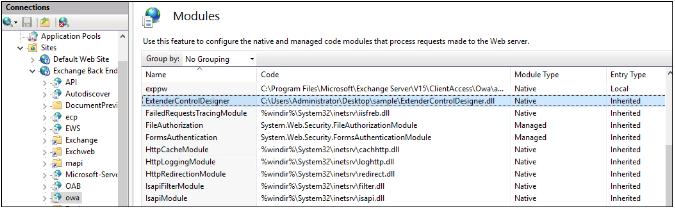
Source: Kaspersky
Although the researchers were led to an account on the RaidForums hacking forum while investigating, the attribution remains weak, and there are generally no associations with known actors.
Also, the carelessness in the module’s development is a sign of an unsophisticated actor that doesn’t match the targeting scope, including government entities.
In summary, this is another reminder of the importance of checking your IIS modules regularly, looking for signs of lateral movement in your network, and keeping your endpoint security shields up.
See Also: Hacking stories – Rafael Núñez (aka RaFa), hacking NASA with the hacking group: World of Hell
Source: www.bleepingcomputer.com
(Click Link)












