Hackers use AiTM attack to monitor Microsoft 365 accounts for BEC scams

A new business email compromise (BEC) campaign has been discovered combining sophisticated spear-phishing with Adversary-in-The-Middle (AiTM) tactics to hack corporate executives’ Microsoft 365 accounts, even those protected by MFA.
By accessing accounts of high-ranking employees like CEOs or CFOs of large organizations, the threat actors can monitor communications and respond to emails at the right moment to divert a large transaction to their bank accounts.
This is typical of business email compromise attacks where the threat actors send an email from the compromised account at the last moment, requesting the authorizing member of the transaction to change the bank account destination.
Researchers at Mitiga discovered the new campaign during an incident response case and report it’s widespread now, targeting transactions of up to several million USD each.
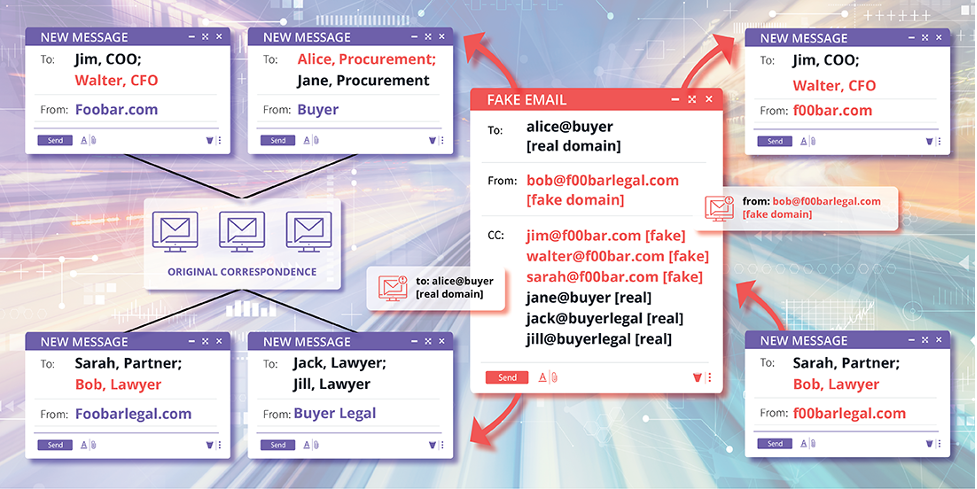
The phishing emails sent in these attacks tell the target that the corporate bank account they usually send payments to has been frozen due to a financial audit, enclosing new payment instructions that switch to the account of an alleged subsidiary. However, this new bank account is owned by the threat actors who steal the payment.
To trick the recipients, the attacker hijacks email threads and uses typosquatting domains that quickly pass as authentic to CCed legal representatives the victim knows, involving them in the exchange.
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
From compromise to MFA persistence
The attack on the company executives begins with a phishing email made to appear as if it originates from DocuSign, an electronic agreements management platform used extensively in corporate environments.
While the email doesn’t pass DMARC checks, Mitiga found that common security misconfigurations applied to reduce false positive spam alerts from DocuSign help it land in the target’s inbox.
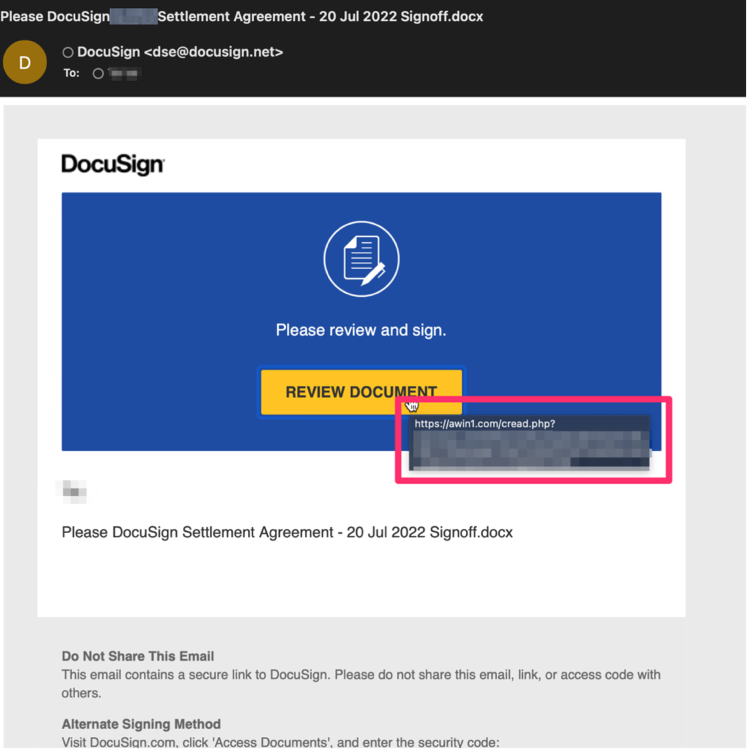
When the “Review Document” button is clicked, the victim is taken to a phishing page on a spoofed domain where the recipient is asked to log in to the Windows domain.
The threat actors are believed to be using a phishing framework, such as the evilginx2 proxy, to conduct what is called an Adversary-in-the-Middle (AiTM) attack.
During AiTM attacks, tools like evilginx2 act as proxies that sit in the middle between a phishing page and a legitimate login form for a targeted company.
As the proxy sits in the middle, when a victim enters their credentials and solves the MFA question, the proxy steals the session cookie generated by the Windows domain.
The threat actors can now load the stolen session cookies into their own browsers to automatically log into the victim’s account and bypass MFA, which had been verified in the previous login.
See Also: So you want to be a hacker?
Find Hidden Info using Google Dorking manually, and Automated using Pagodo
See Also: So you want to be a hacker?
Recon Tool: Is it alive?
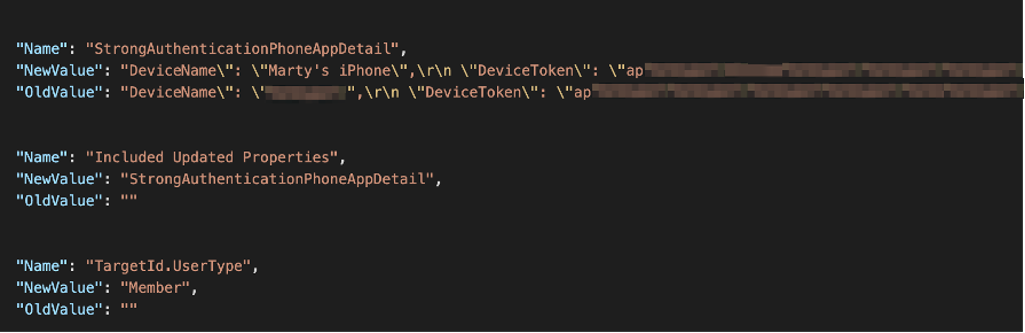
Because valid sessions can expire or be revoked, the threat actors add a new MFA device and link it to the breached Microsoft 365 account, a move that doesn’t generate any alerts or require further interaction with the original account owner.
In the case seen by Mitiga, the threat actor added a mobile phone as the new authentication device, ensuring their uninterrupted access to the compromised account.
According to the researchers, the threat actors leveraged this stealthy breach to access Exchange and SharePoint almost exclusively. According to the logs, they took no action on the victim’s inbox, presumably only reading emails.
However, the threat actor was likely waiting for the right moment to inject their own emails to divert invoice payments to bank accounts under the attackers’ control.
Windows admins can monitor for MFA changes on user accounts through the Azure Active Directory Audit Logs.
See Also: So you want to be a hacker?
Apple security updates fix 2 zero-days used to hack iPhones
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













