Hackers Use New PowerExchange Malware to Target Microsoft Exchange Servers

FortiGuard Labs Threat Research team has recently uncovered a highly sophisticated and alarming cyber threat: a new PowerShell-based malware named PowerExchange. This malware has been utilized by the notorious Iranian state-backed hacking group known as APT34 or Oilrig. Their primary target? On-premise Microsoft Exchange servers, which are widely used by organizations for email communication.
The attack vector employed by APT34 involves luring unsuspecting victims through phishing emails. These emails contain an archived malicious executable that, when executed, allows the threat actors to gain unauthorized access to the targeted mail server. Once inside, they deploy a web shell called ExchangeLeech, which was first identified by the Digital14 Incident Response team back in 2020. This web shell operates stealthily in the background, enabling the hackers to steal crucial user credentials.
What sets PowerExchange apart from other malware is its unique communication method with a command-and-control (C2) server. Unlike traditional malware that relies on direct network connections, PowerExchange communicates via emails using the Exchange Web Services (EWS) API. The malware sends stolen information and receives base64-encoded commands through text attachments within emails that have the subject line “Update Microsoft Edge.” By utilizing the victim’s Exchange server as the C2 channel, the backdoor can effectively blend in with benign network traffic, making it extremely difficult to detect and remediate by network-based security measures.
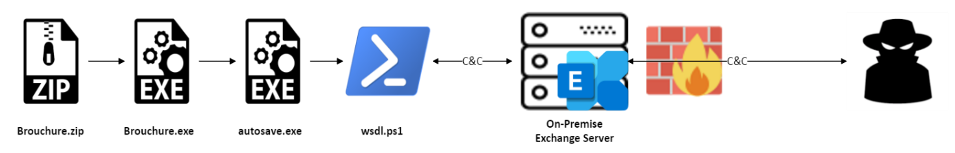 PowerExchange infection chain (FortiGuard Labs)
PowerExchange infection chain (FortiGuard Labs)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
PowerExchange Malware – Advanced Tool for Remote Control and Data Theft
Once the hackers have established control over the compromised servers, they have a wide range of capabilities at their disposal. PowerExchange allows them to execute commands remotely, delivering additional malicious payloads to the hacked servers and exfiltrating sensitive files from the victim’s network. Furthermore, during the forensic investigation conducted by FortiGuard Labs, additional backdoored endpoints with various other malicious implants were discovered, indicating a more extensive compromise.
FortiGuard Labs has drawn connections between the PowerExchange malware and APT34’s previous activities, specifically their use of TriFive malware to backdoor the servers of Kuwaiti government organizations. Both backdoors share significant similarities, such as being written in PowerShell, activation through a periodic scheduled task, and leveraging the organization’s Exchange server with the EWS API for C2 communication. While there are notable differences in the code, the researchers speculate that PowerExchange represents an evolved and improved form of TriFive.
Trending: Recon Tool: Dome
It’s worth noting that APT34 has a history of utilizing phishing emails as an initial infection vector and has previously breached various entities in the United Arab Emirates. The discovery of PowerExchange reinforces the group’s relentless pursuit of sophisticated cyberattacks and highlights the increasing need for robust security measures to protect critical infrastructure.
The cybersecurity community and organizations utilizing Microsoft Exchange servers are urged to remain vigilant, implement strong security practices, and promptly apply relevant patches and updates to safeguard against evolving threats like PowerExchange.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












