HardBit 4.0 Ransomware Introduces Obfuscation Techniques and Passphrase Protection

Overview of HardBit Ransomware
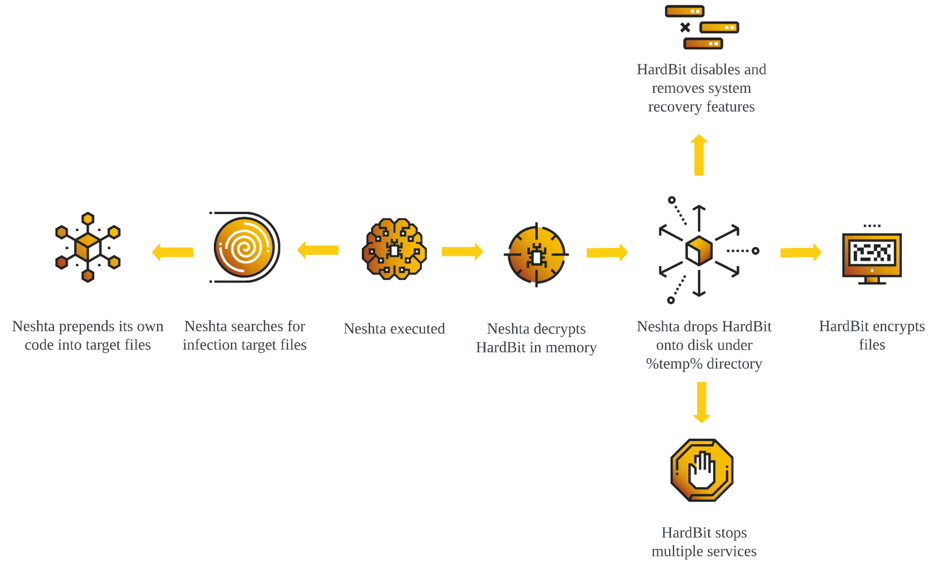
The HardBit ransomware group has released version 4.0 of their malicious software, featuring new obfuscation techniques and passphrase protection to make analysis more challenging for cybersecurity researchers. Initially identified in October 2022, HardBit is known for its financially motivated double extortion tactics, pressuring victims to pay ransoms without operating a data leak site.
New Security Features in HardBit 4.0
According to researchers Kotaro Ogino and Koshi Oyama from Cybereason, HardBit 4.0 includes significant enhancements:
- Passphrase Protection: The ransomware now requires a passphrase during runtime, adding an extra layer of security and hindering analysis efforts.
- Obfuscation Techniques: Enhanced obfuscation techniques are employed to deter reverse engineering and analysis by security experts.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Operational Tactics
Despite these new features, the HardBit group continues to use similar operational tactics as before. Their primary communication method remains the Tox instant messaging service, and their extortion strategy involves threats of future attacks rather than data leaks. The exact initial access vector is unclear, but it’s suspected to involve brute-forcing RDP and SMB services.
Post-Compromise Activities
Once inside a network, the attackers employ tools like Mimikatz and NLBrute for credential theft and Advanced Port Scanner for network discovery. These tools allow the attackers to move laterally within the network via RDP. HardBit ransomware then executes a series of steps to weaken the host’s security before encrypting data, including:
- Disabling Microsoft Defender Antivirus
- Terminating processes and services to evade detection and inhibit recovery
- Encrypting files and updating their icons
- Changing desktop wallpaper and altering the system’s volume label to “Locked by HardBit”

Trending: Offensive Security Tool: DDoSlayer
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com