Honda’s E-commerce Platform Exposed, Researcher Exploits API Flaws for Unrestricted Data Access

Honda, a renowned Japanese manufacturer known for automobiles, motorcycles, and power equipment, recently faced a significant security breach in its e-commerce platform for power equipment, marine, and lawn & garden products. The platform’s vulnerability allowed unauthorized access due to flaws in its application programming interface (API), enabling password resets for any account.
This critical security gap came to light when security researcher Eaton Zveare, who previously exposed vulnerabilities in Toyota’s supplier portal, discovered similar weaknesses in Honda’s systems. Zveare exploited a password reset API to reset passwords for valuable accounts, granting unrestricted access to admin-level data on the company’s network.
The researcher explained that broken or missing access controls made it possible to access all data on the platform, even when logged in as a test account. This exposed sensitive information, including 21,393 customer orders from August 2016 to March 2023, containing customer names, addresses, phone numbers, and ordered items. Additionally, 1,570 dealer websites, with 1,091 currently active, were susceptible to modification. The breach also compromised 3,588 dealer user accounts, including names and email addresses, along with 1,090 dealer email accounts and 11,034 customer email accounts. Furthermore, private keys for payment processors such as Stripe, PayPal, and Authorize.net, provided by dealers, were potentially exposed, raising concerns about financial security. Internal financial reports were also among the compromised data.
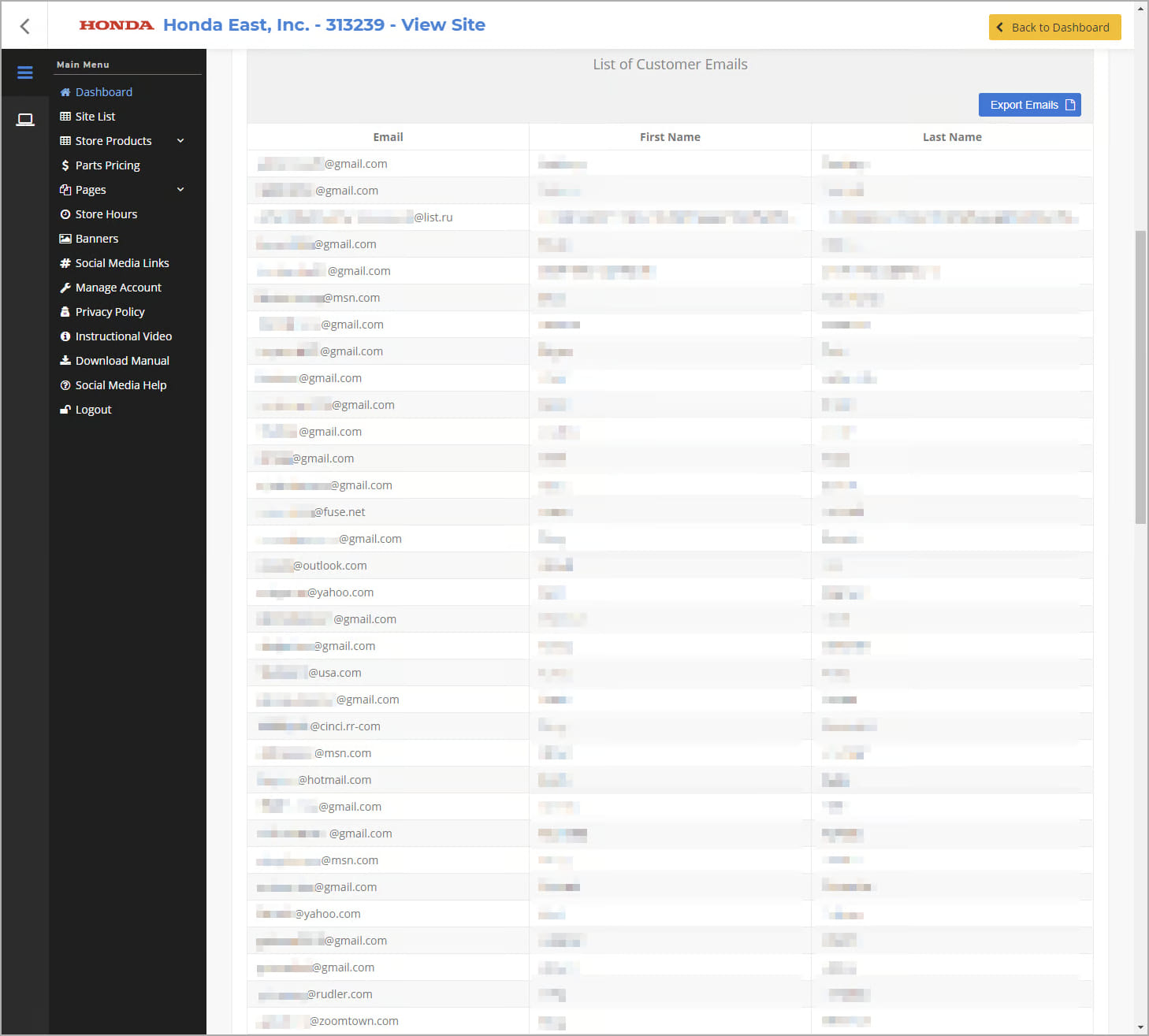 Exposed customer emails (eaton-works.com)
Exposed customer emails (eaton-works.com)
The disclosed information could be exploited for nefarious purposes, including launching phishing campaigns, executing social engineering attacks, or selling the data on hacker forums and the dark web. Moreover, the ability to access dealer sites could facilitate the injection of credit card skimmers or other malicious JavaScript snippets.
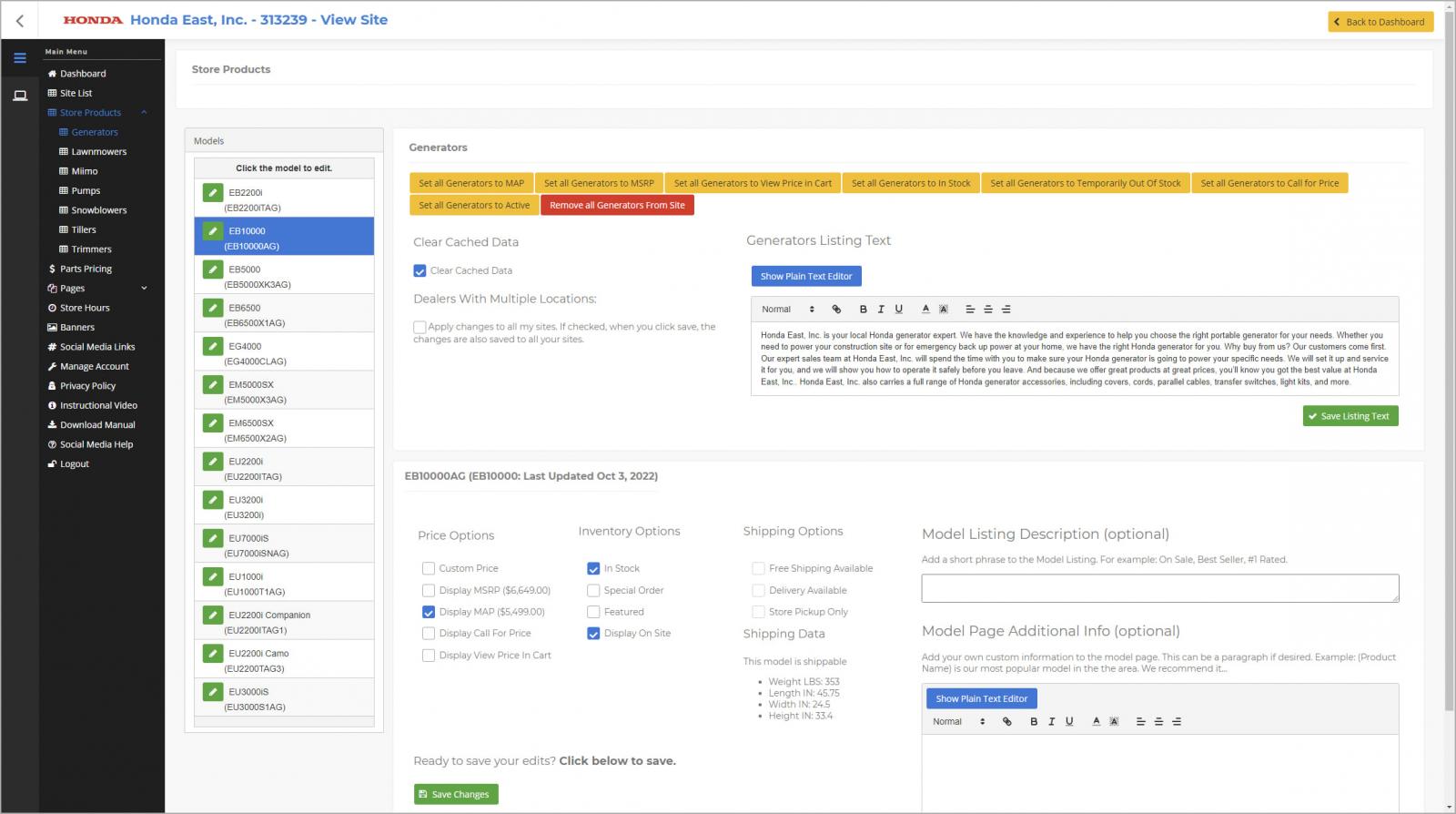 Ability to edit page content (eaton-works.com)
Ability to edit page content (eaton-works.com)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Admin Panels
The vulnerability lay within Honda’s e-commerce platform, specifically in the assignment of “powerdealer.honda.com” subdomains to registered dealers. Although the API flaw was not present in the e-commerce subdomains’ login portal, credentials obtained through the Power Equipment Tech Express (PETE) site allowed access to internal dealership data. By exploiting the vulnerability, an attacker could traverse the platform’s dealer sites with ease.
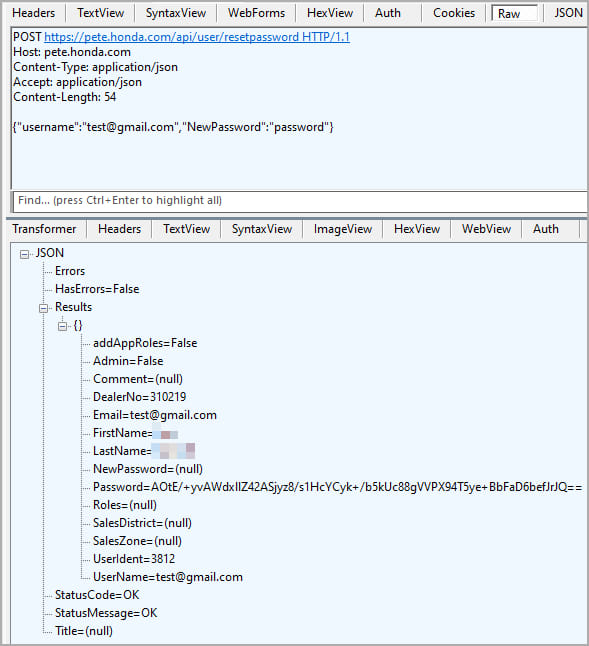 Password reset API request sent to PETE (eaton-works.com)
Password reset API request sent to PETE (eaton-works.com)
To gain a valid email address belonging to a dealer, Zveare obtained it from a YouTube video that demonstrated the dealer dashboard using a test account.
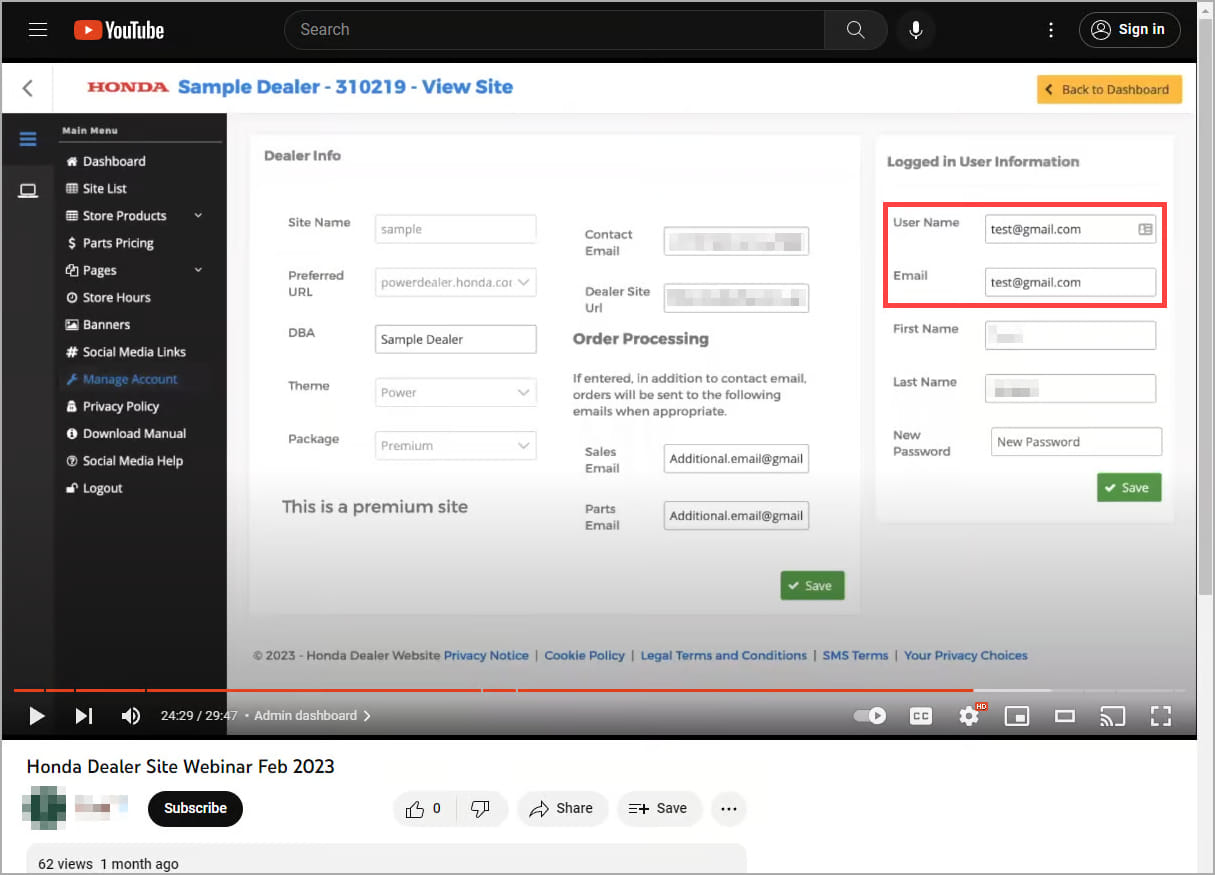 Test account email exposed on YouTube video (eaton-works.com)
Test account email exposed on YouTube video (eaton-works.com)
With this information, the researcher sought to access data from real dealers without resetting numerous passwords or causing disruptions. Leveraging a second vulnerability, which involved the sequential assignment of user IDs and a lack of access protections, Zveare successfully accessed the data panels of all Honda dealers by incrementing the user ID.
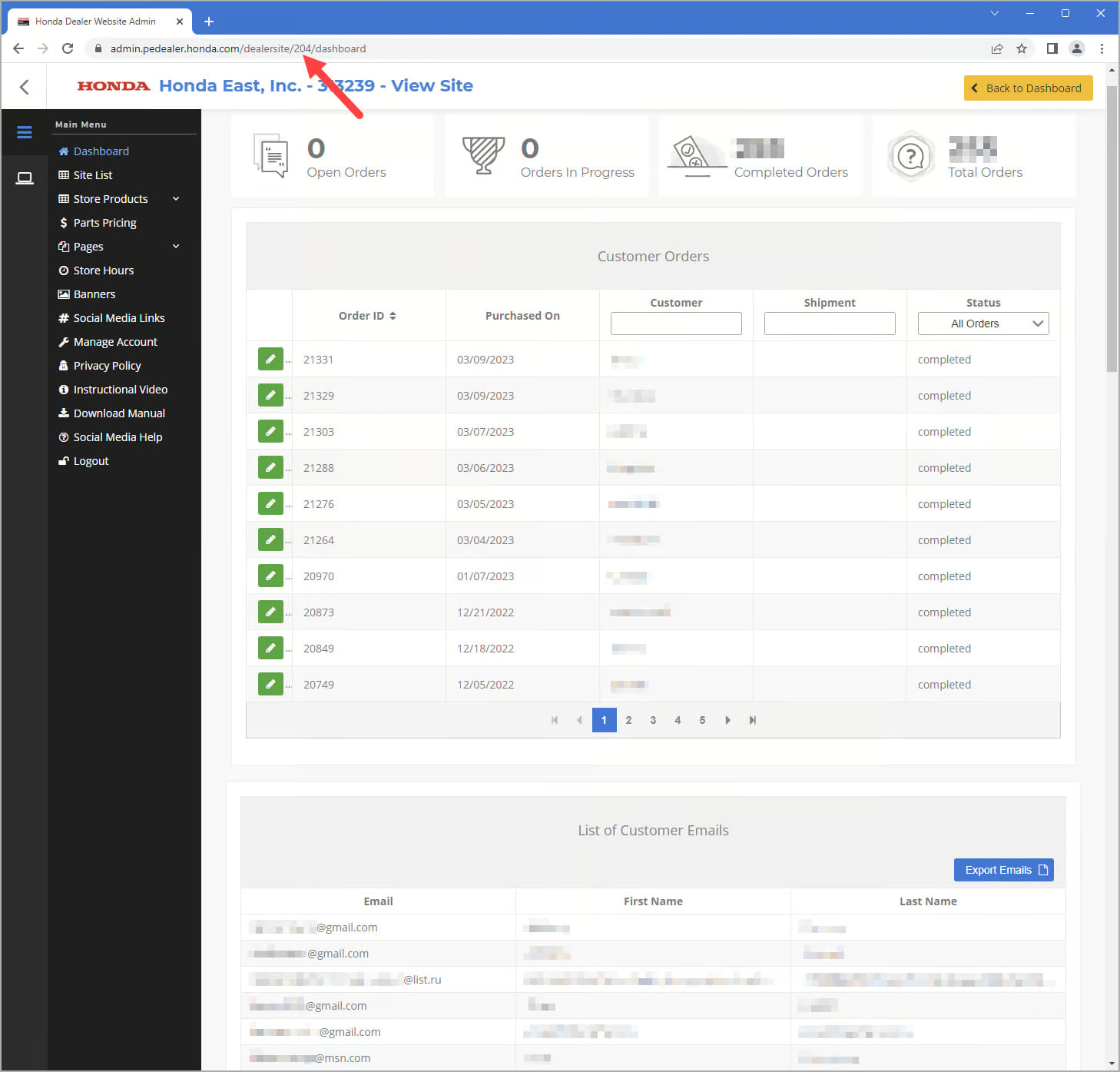 Increasing the user ID number to access all dealer panels (eaton-works.com
Increasing the user ID number to access all dealer panels (eaton-works.com
Trending: Offensive Security Tool: Pyramid
The final step in the attack involved accessing Honda’s admin panel, which serves as the central control point for the company’s e-commerce platform. By modifying an HTTP response, Zveare manipulated the system to appear as an admin, granting unrestricted access to the Honda Dealer Sites platform.
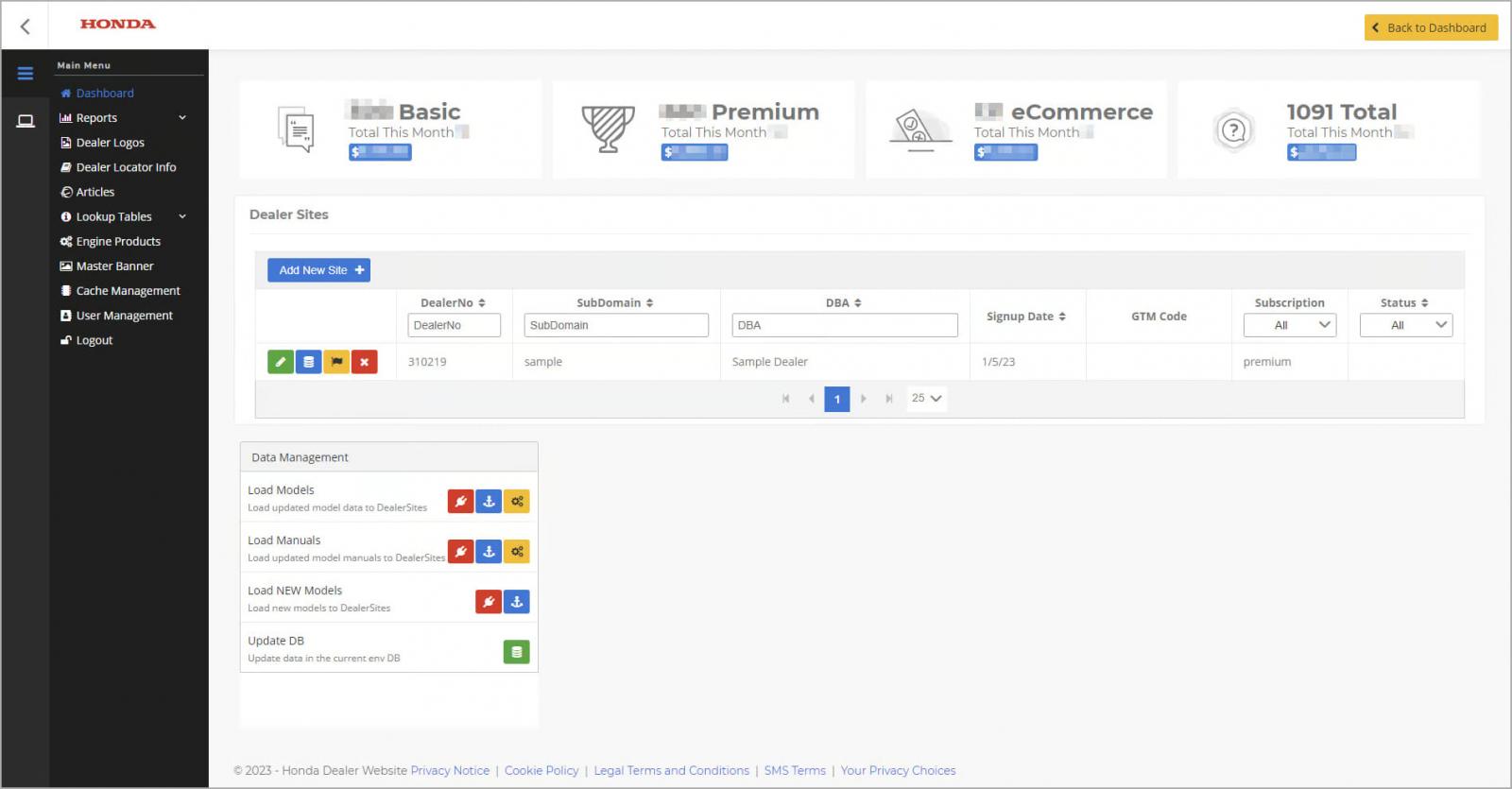 The Honda Dealer Sites admin panel (eaton-works.com)
The Honda Dealer Sites admin panel (eaton-works.com)
On March 16, 2023, the researcher reported the discovered vulnerabilities to Honda. By April 3, 2023, Honda confirmed that all issues had been resolved. It is worth noting that Honda does not have a bug bounty program in place, and as in the case with Toyota, Zveare did not receive any reward for his responsible reporting.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












