HotRat Malware -The Sneaky Trojan Lurking in Cracked Software
A new variant of the notorious AsyncRAT malware, dubbed HotRat, has emerged, spreading through free, pirated versions of popular software and utilities, including video games, image and sound editing software, and Microsoft Office.
HotRat poses a serious threat, arming attackers with an array of capabilities, such as stealing login credentials, cryptocurrency wallets, screen capturing, keylogging, installing additional malware, and gaining access to or altering clipboard data, according to Avast security researcher Martin a Milánek.
The Czech cybersecurity firm reports that this trojan has been rampant in the wild since at least October 2022, with a significant number of infections concentrated in countries such as Thailand, Guyana, Libya, Suriname, Mali, Pakistan, Cambodia, South Africa, and India.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
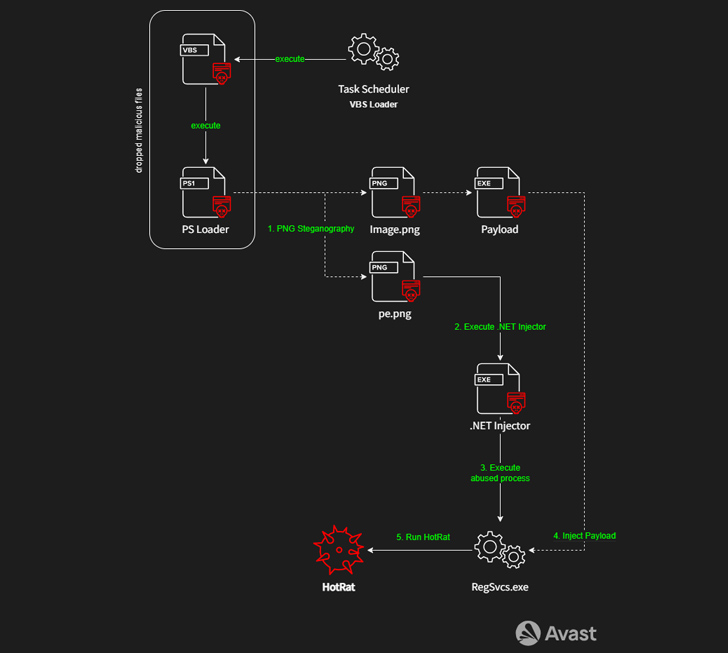
The attack method involves bundling cracked software, readily available online through torrent sites, with a malicious AutoHotkey (AHK) script. This script initiates an infection chain specifically designed to deactivate antivirus solutions on the compromised host and ultimately deploys the HotRat payload using a Visual Basic Script loader.
Described as a comprehensive RAT malware, HotRat boasts nearly 20 commands, each capable of executing a .NET module retrieved from a remote server. This flexibility allows the threat actors behind the campaign to enhance its features as needed.
Trending: Digital Forensics Tool: ScrapPy
However, it’s essential to note that this attack requires administrative privileges to succeed in realizing its objectives.
“Despite the substantial risks involved, the irresistible temptation to acquire high-quality software at no cost persists, leading many people to download illegal software,” warned Milánek. “Therefore, distributing such software remains an effective method for widely spreading malware.”
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












