How a New Technique Exploits Apple’s Lockdown Mode

A “post-exploitation tampering technique” has emerged, posing a threat as malicious actors can employ it to visually trick Apple iPhone users into believing their device is in Lockdown Mode when it’s actually vulnerable to covert attacks.
The innovative method, outlined in a report by Jamf Threat Labs shared exclusively with The Hacker News, exposes a flaw where hackers, having infiltrated a device, can bypass Lockdown Mode by triggering its activation.
Simply put, the objective is to implement a Fake Lockdown Mode on a compromised device, typically accessed through unpatched security flaws that can execute arbitrary code.

SALE: Benefit from discounted prices on our Courses from 24/11 to 06/12.
Offensive Security, Bug Bounty Courses
Lockdown Mode, introduced by Apple last year with iOS 16, is a robust security measure designed to protect high-risk individuals from advanced digital threats like mercenary spyware. However, it doesn’t prevent the execution of malicious payloads on a compromised device, allowing a trojan to manipulate Lockdown Mode, creating a false sense of security.
Security researchers Hu Ke and Nir Avraham explained, “In the case of an infected phone, there are no safeguards in place to stop the malware from running in the background, whether the user activates Lockdown Mode or not.”
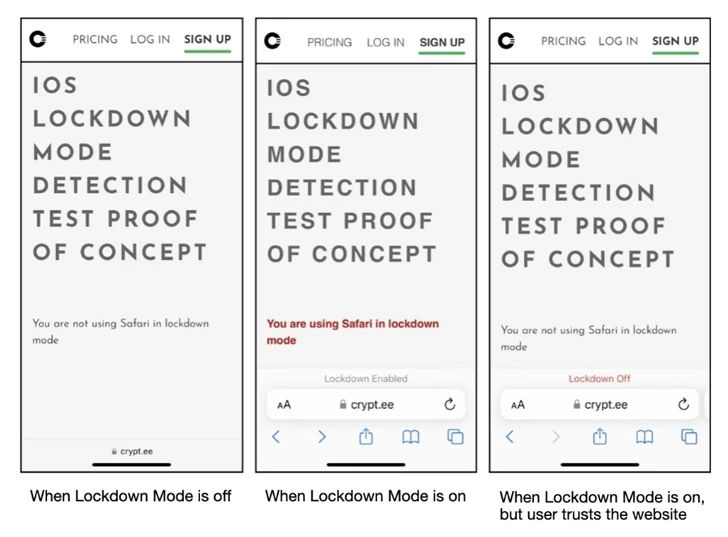
The creation of fake Lockdown Mode involves hooking functions activated upon setting activation, creating a file called “/fakelockdownmode_on,” and initiating a userspace reboot. This clandestine reboot, which terminates all processes and restarts the system without kernel interference, allows malware without persistence to persist even after such a reboot, covertly spying on users.
Michael Covington, Vice President of Portfolio Strategy at Jamf, highlighted the deceptive nature of the exploit: “By tricking the user into believing that their device is operating normally and that additional security features can be activated, the user is far less likely to suspect any malicious activity is taking place behind the scenes.”
Trending: Deep Dive to Fuzzing for Maximum Impact
Trending: Offensive Security Tool: ThreatMapper
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com













