HTTP/2 ‘CONTINUATION Flood’ Technique Can Be Exploited in DoS Attacks

A revelation has surfaced concerning the HTTP/2 protocol, as newly discovered vulnerabilities dubbed “CONTINUATION Flood” pose a great threat to web servers, potentially leading to debilitating denial of service (DoS) assaults.
These vulnerabilities, identified within the HTTP/2 protocol—an update to the HTTP standard introduced in 2015—have sparked concerns among cybersecurity experts regarding the integrity and stability of online infrastructure.
The discovery of the CONTINUATION Flood vulnerabilities stems from the diligent research efforts of Barket Nowotarski, shedding light on critical flaws within the HTTP/2 implementation. Nowotarski’s findings highlight inherent weaknesses related to HTTP/2 CONTINUATION frames, which, when exploited, can trigger server outages by exploiting memory resources or causing CPU exhaustion.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
HTTP/2 messages, characterized by serialized header and trailer sections, are susceptible to fragmentation across multiple frames, with CONTINUATION frames serving as the mechanism for stitching these sections together. However, the absence of adequate frame checks in various implementations enables threat actors to launch orchestrated attacks by inundating servers with an excessive volume of frames, bypassing crucial safeguards.
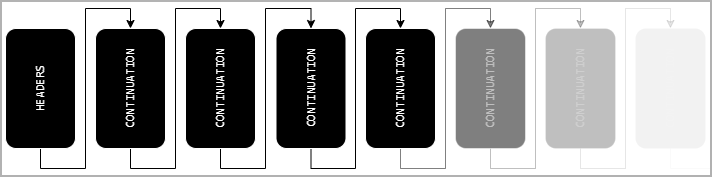 Endless stream of CONTINUATION frames causing DoS (nowotarski.info)
Endless stream of CONTINUATION frames causing DoS (nowotarski.info)
The severity of these vulnerabilities is underscored by the issuance of several CVE IDs by the CERT Coordination Center (CERT-CC), pinpointing affected HTTP/2 implementations and outlining the diverse range of denial of service tactics enabled by the flaws.
The vulnerabilities are attributed to various CVE IDs, impacting multiple HTTP/2 implementations across different platforms and libraries. From Node.js to Apache Httpd, these vulnerabilities manifest in different forms, including memory leaks, CPU exhaustion, and improper request termination.
Trending: Understanding PTaaS and SOC
Trending: Offensive Security Tool: WAF Bypass


