In-Browser Windows Update Simulation Used as a Vehicle for Aurora Malware

Sophisticated Malverising Campaign Spreads Aurora Malware with Fake Windows Update Simulation
A sophisticated malvertising campaign has recently been uncovered, employing an in-browser Windows update simulation to distribute the notorious Aurora information-stealing malware. Known for its advanced capabilities and low detection rates, Aurora has been advertised on hacker forums for over a year. Researchers at Malwarebytes have revealed that this malvertising operation strategically utilizes popunder ads on adult content websites with high traffic, redirecting unsuspecting users to locations hosting the malware.
 Fake Windows update (Malwarebytes)
Fake Windows update (Malwarebytes)
Popunder ads are a type of inexpensive advertisement that opens behind the active browser window, remaining hidden until the user closes or moves the main window. In a similar vein, Google had reported a popunder-based ad fraud campaign in December of last year, which generated hundreds of thousands of visitors and tens of millions of fraudulent ad impressions.
While the impact of the recent malvertising campaign was relatively lower, redirecting around 30,000 users and resulting in the download and installation of the data-stealing malware on nearly 600 systems, it employed a deceptive tactic. The threat actor devised a clever strategy where the popunder displays a full-screen browser window, simulating a Windows system update screen.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Unraveling the Malicious Tactics of a Sophisticated Malvertising Campaign
The researchers at Malwarebytes tracked multiple domains involved in the campaign, with several of them mimicking adult websites while simulating the fake Windows update. These domains included names such as activessd[.]ru, xhamster-18[.]ru, and click7adilla[.]ru, among others. Despite the deceptive nature of the full-screen browser window, some users fell victim to the ruse and unknowingly executed the malicious executable file named “ChromeUpdate.exe” that was offered for download.
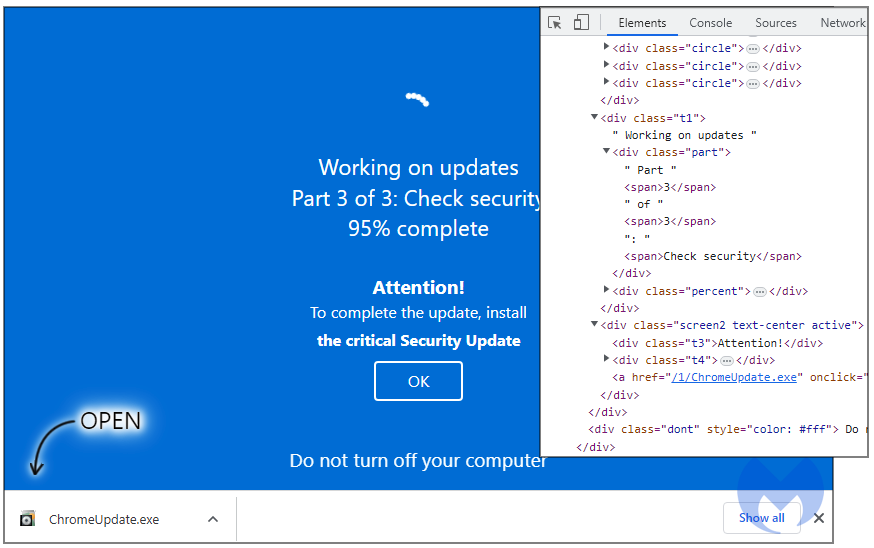 Downloaded file (Malwarebytes)
Downloaded file (Malwarebytes)
Upon closer examination, it was discovered that the alleged Chrome updater was, in fact, a “fully undetectable” (FUD) malware loader known as ‘Invalid Printer,’ exclusively used by this particular threat actor. Interestingly, when Malwarebytes analysts first encountered ‘Invalid Printer,’ no antivirus engines on Virus Total classified it as malicious. However, a few weeks later, detection started to increase following the release of a relevant report from Morphisec.
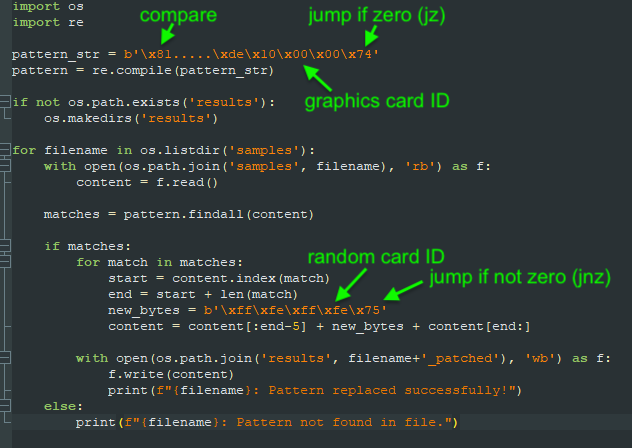 Malware loader code snippet (Malwarebytes)
Malware loader code snippet (Malwarebytes)
The ‘Invalid Printer’ malware loader is designed to check the host’s graphics card to determine if it is running on a virtual machine or in a sandbox environment. If not, it proceeds to unpack and launch the Aurora information-stealer, as revealed by the researchers. Malwarebytes commented that the threat actor behind this campaign appears to have a strong interest in creating tools that are difficult to detect, constantly uploading new samples on Virus Total to gauge their detection rates.
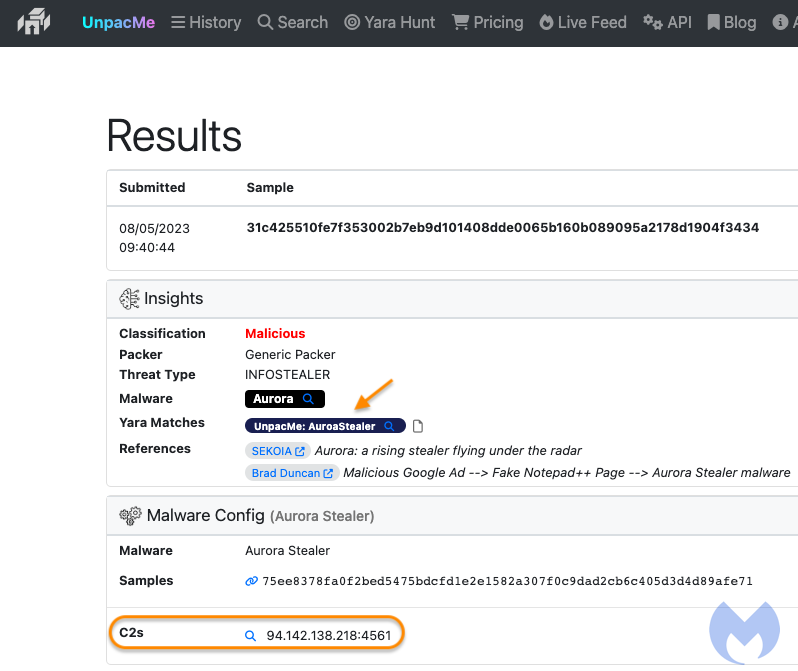 Payload carried by ‘Invalid Printer’ (Malwarebytes)
Payload carried by ‘Invalid Printer’ (Malwarebytes)
Trending: Malware Analysis Tool: retoolkit
Jérôme Segura, the director of threat intelligence at Malwarebytes, noticed a notable pattern during their investigation. Each time a new sample was initially submitted to Virus Total, it originated from a user in Turkey, with file names that appeared freshly compiled (e.g., build1_enc_s.exe). Further investigation revealed that the threat actor also utilizes an Amadey panel, suggesting the potential use of a well-documented reconnaissance and malware loading tool, alongside running tech support scams that target Ukrainian victims.
Malwarebytes has provided a comprehensive technical analysis of the malware’s installation and behavior, along with a set of indicators of compromise (IoCs) that companies and security vendors can leverage to protect their users.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












