Infostealer Malware Circumvents Chrome’s Encryption in New Attacks

Chrome’s App-Bound Encryption Under Attack
Google Chrome introduced App-Bound Encryption in version 127 to protect sensitive data like cookies and stored passwords. This feature uses a Windows service with system privileges to encrypt data, preventing malware with user-level permissions from accessing secrets stored in the browser.
Malware Developers Claim Bypass Success
Despite these protections, multiple infostealer malware developers have claimed to bypass Chrome’s encryption feature. Security researchers g0njxa and RussianPanda9xx observed developers boasting that their tools (MeduzaStealer, Whitesnake, Lumma Stealer, Lumar (PovertyStealer), Vidar Stealer, StealC) can circumvent this security measure.
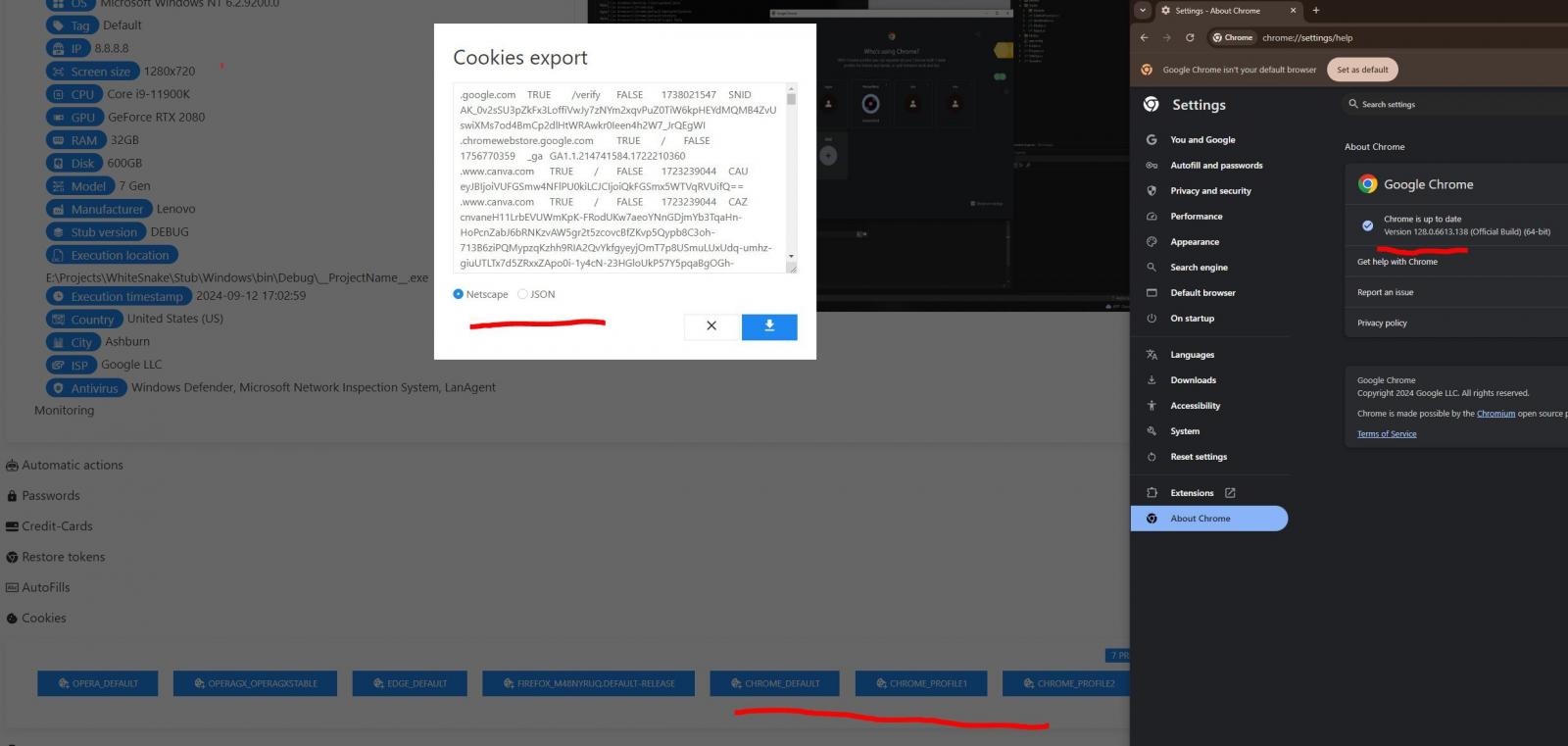 Whitesnake stealer grabbing cookies from Chrome 128
Whitesnake stealer grabbing cookies from Chrome 128
Source: @g0njxa
Real Bypass Confirmed
G0njxa confirmed for BleepingComputer that the latest variant of Lumma Stealer successfully bypassed the encryption feature in Chrome 129, the most recent browser version. The researcher tested this in a sandbox environment on a Windows 10 Pro system.
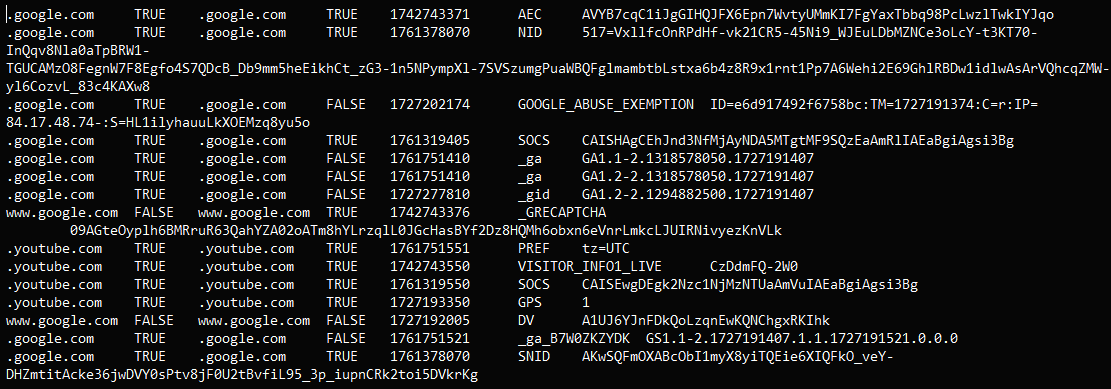 Extracted cookies from Chrome 129, using latest Lumma
Extracted cookies from Chrome 129, using latest Lumma
Source: @g0njxa
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Rapid Implementation of Bypass Mechanisms
Meduza and WhiteSnake implemented their bypass mechanisms over two weeks ago, Lumma last week, and Vidar and StealC this week. Initially, Lumar responded to App-Bound Encryption by requiring admin rights, but it has since implemented a bypass mechanism that operates with the logged-in user’s privileges.
Simplified Cookie Theft Without Admin Rights
Lumma Stealer developers assured customers that their new method of collecting Chrome cookies does not require admin privileges or a system restart, simplifying the crypt build and reducing detection chances, thereby increasing the knock rate.
Trending: Offensive Security Tool: DDoSlayer
Bypass Method Remains Unclear
The exact method used to bypass App-Bound Encryption remains undisclosed, but Rhadamanthys malware authors claimed it took them only 10 minutes to reverse the encryption.
Waiting for Google’s Response – Update 9/25
BleepingComputer has contacted Google for a comment on the malware developers’ response to App-Bound Encryption in Chrome but is still waiting for a reply.
Researcher RussianPanda9xx also confirmed to BleepingComputer that Vidar and Lumma are capable of retrieving cookies from the latest Chrome version, as validated through testing.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













