Intel confirms leaked Alder Lake BIOS Source Code is authentic

Reading Time: 3 Minutes
Intel has confirmed that a source code leak for the UEFI BIOS of Alder Lake CPUs is authentic, raising cybersecurity concerns with researchers.
Alder Lake is the name of Intel’s 12th generation Intel Core processors, released in November 2021.
On Friday, a Twitter user named ‘freak’ posted links to what was said to be the source code for Intel Alder Lake’s UEFI firmware, which they claim was released by 4chan.
The link led to a GitHub repository named ‘ICE_TEA_BIOS’ that was uploaded by a user named ‘LCFCASD.’ This repository contained what was described as the ‘BIOS Code from project C970.’
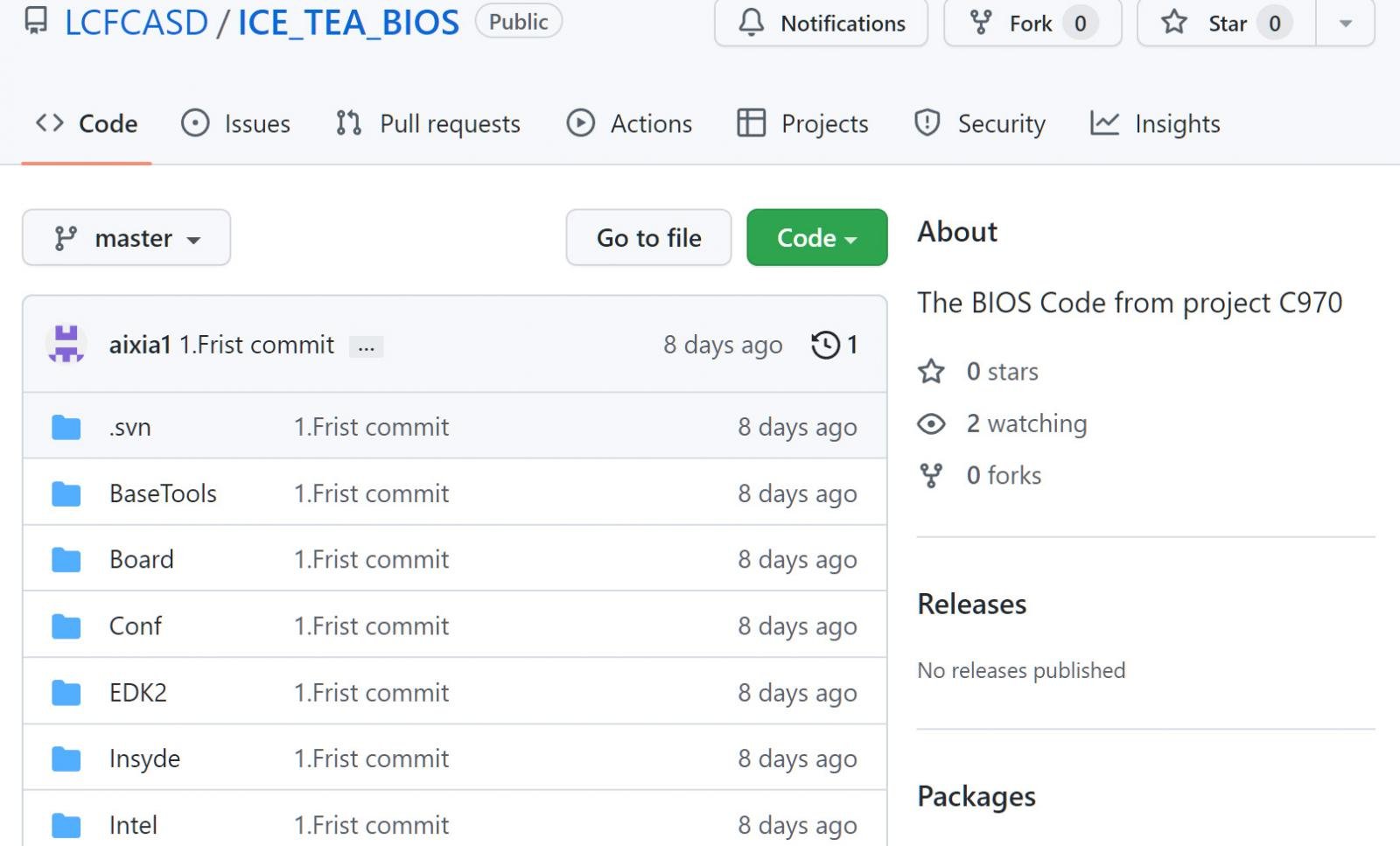
Source: BleepingComputer
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
The leak contains 5.97 GB of files, source code, private keys, change logs, and compilation tools, with the latest timestamp on the files being 9/30/22, likely when a hacker or insider copied the data.
BleepingComputer has been told that all the source code was developed by Insyde Software Corp, a UEFI system firmware development company.
The leaked source code also contains numerous references to Lenovo, including code for integrations with ‘Lenovo String Service’, ‘Lenovo Secure Suite’, and ‘Lenovo Cloud Service.’
At this time, it is unclear whether the source code was stolen during a cyberattack or leaked by an insider.
However, Intel has confirmed to Tom’s Hardware that the source code is authentic and is its “proprietary UEFI code.”
“Our proprietary UEFI code appears to have been leaked by a third party. We do not believe this exposes any new security vulnerabilities as we do not rely on obfuscation of information as a security measure. This code is covered under our bug bounty program within the Project Circuit Breaker campaign, and we encourage any researchers who may identify potential vulnerabilities to bring them our attention through this program. We are reaching out to both customers and the security research community to keep them informed of this situation.” – Intel spokesperson.
Trending: A primer on OS Command Injection Attacks
Trending: OSINT Tool: ProtOSINT
Security researchers concerned
While Intel has downplayed the security risks of the source code leak, security researchers warn that the contents could make it easier to find vulnerabilities in the code.
“The attacker/bug hunter can hugely benefit from the leaks even if leaked OEM implementation is only partially used in the production,” explains hardware security firm Hardened Vault.
“The Insyde’s solution can help the security researchers, bug hunters (and the attackers) find the vulnerablity and understand the result of reverse engineering easily, which adds up to the long-term high risk to the users.”
Positive Technologies hardware researcher Mark Ermolov also warned that the leak included a KeyManifest private encryption key, a private key used to secure Intel’s Boot Guard platform.
A very bad thing happened: now, the Intel Boot Guard on the vendor's platforms can no longer be trusted… ☹️ pic.twitter.com/K5mXcp5ipW
— Mark Ermolov (@_markel___) October 8, 2022
While it is not clear if the leaked private key is used in production, if it is, hackers could potentially use it to modify the boot policy in Intel firmware and bypass hardware security.
BleepingComputer has contacted Intel, Insyde, and Lenovo with questions about the leak and whether the private keys were used in production.
We will update this article with any responses as we learn more.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com