iShutdown Scripts Expose Spyware on Compromised Apple Devices

Security researchers have identified a method to detect high-profile spyware infections, including Pegasus, Reign, and Predator, on compromised Apple mobile devices. Kaspersky has introduced 3 Python scripts, collectively known as iShutdown, to automate the analysis of the Shutdown.log system log file, where digital forensic artifacts of malware infections can be found.
The Shutdown.log file, which records reboot events, becomes a crucial source for identifying infections that impact device reboot due to process injection and manipulation performed by the malware. This method offers a more accessible analysis compared to traditional techniques like examining encrypted iOS backups or network traffic.
Kaspersky’s iShutdown scripts consist of three components:
- iShutdown_detect.py: Analyzes the Sysdiagnose archive containing the log file.
- iShutdown_parse.py: Extracts Shutdown.log artifacts from the tar archive.
- iShutdown_stats.py: Extracts reboot statistics from the log file.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
To utilize these scripts, Kaspersky recommends restarting the infected device frequently, as the Shutdown.log file can only register data with signs of infection after a reboot following compromise.
While the GitHub repository provides instructions and example outputs, users are advised to have some familiarity with Python, iOS, terminal output, and malware indicators to properly evaluate the results.
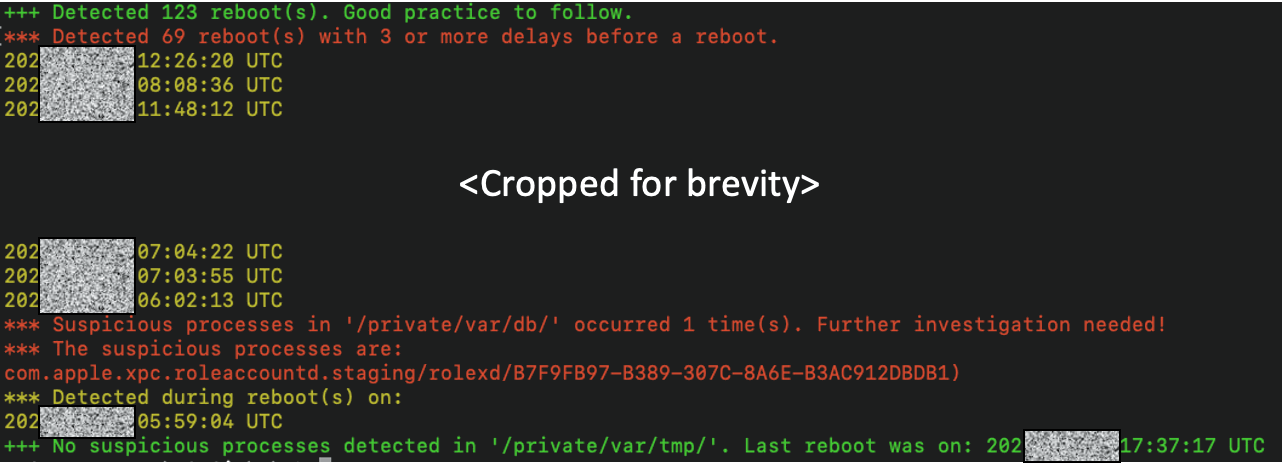 Output highlighting processes delaying the reboot process (Kaspersky)
Output highlighting processes delaying the reboot process (Kaspersky)
The method, initially used to analyze iPhones infected with Pegasus spyware, has shown consistency in behavior across other Pegasus infections, confirming its reliability as a forensic artifact. However, the researchers note that the method may fail if the user doesn’t reboot the device on the day of infection.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













