JavaScript Supply Chain Attack: Polyfill.io Redirects Users to Scam Sites After Chinese Acquisition

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Sansec found that the new owners of Polyfill.io were injecting malicious code that redirected users to scam sites without the knowledge of the website owners. For example, users were redirected to fake sportsbook sites through domains like www.googie-anaiytics.com and kuurza.com/redirect?from=bitget.
The malicious script employs specific targeting measures and is resistant to reverse engineering. It activates only on certain mobile devices at specific times, avoids execution when detecting admin users, and delays execution when a web analytics service is present to avoid detection.
Currently, the domain cdn.polyfill.io has been redirected to Cloudflare’s mirror. However, as the domain’s DNS servers remain unchanged, the owners could revert it to their own domains at any time. BleepingComputer contacted Cloudflare for comment but has not received a response.
Google Issued a Warning
In light of this attack, Google has begun notifying advertisers, warning them that their landing pages may include the malicious code, potentially redirecting visitors away from the intended site without permission. Google has also flagged other services, such as Bootcss, Bootcdn, and Staticfile, as sources of similar redirects, potentially affecting thousands more sites.
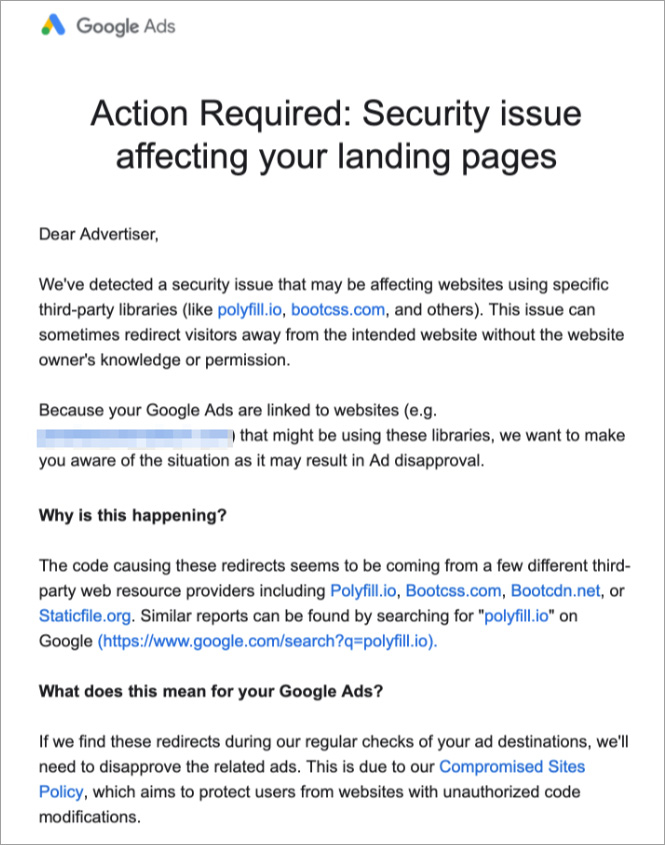 Google letter to advertisers about supply chain attack
Google letter to advertisers about supply chain attack
Source: SanSec
Trending: Offensive Security Tool: Freeway
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













