Lazarus Continues to Evolve Tactics with Shift to Linux Malware

North Korean threat group Lazarus targets Linux users in Operation DreamJob, responsible for 3CX attack confirmed by ESET and Mandiant.
North Korean threat group Lazarus, notorious for its high-profile cyber attacks, has expanded its Operation DreamJob campaign to target Linux users with malware for the first time. ESET researchers discovered this new targeting method, confirming with high confidence that Lazarus was responsible for the recent supply-chain attack on VoIP provider 3CX. The attack was discovered in March 2023 and compromised multiple companies using the trojanized version of the 3CX client, resulting in the installation of information-stealing trojans.
According to Mandiant, the 3CX breach was linked to North Korean threat actors after an employee installed trojanized trading software from Trading Technologies, which had also been compromised in another North Korean supply-chain attack. Mandiant’s investigation further confirms the findings of multiple cybersecurity companies, who previously suspected Lazarus to be responsible for the 3CX attack.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Operation DreamJob
As part of Operation DreamJob, Lazarus targets individuals who work in software or DeFi platforms with fake job offers on social media platforms, such as LinkedIn. ESET discovered that Lazarus distributes a ZIP archive named “HSBC job offer.pdf.zip” through spearphishing or direct messages on LinkedIn. The archive contains a Go-written Linux binary, which uses a Unicode character on its name to make it appear like a PDF. The malware, known as “OdicLoader,” displays a decoy PDF while simultaneously downloading a second-stage malware payload called “SimplexTea” from a private repository hosted on the OpenDrive cloud service.
 The decoy PDF displayed to the target (ESET)
The decoy PDF displayed to the target (ESET)
ESET found that SimplexTea is very similar in functionality, encryption techniques, and hardcoded infrastructure used with Lazarus’ Windows malware, “BadCall,” and the macOS variant, “SimpleSea.” ESET also discovered an earlier variant of SimplexTea, called “sysnetd,” on VirusTotal. This earlier variant is similar to the mentioned backdoors but written in C, and it loads its configuration from a file named /tmp/vgauthsvclog, used by the VMware Guest Authentication service. This suggests that the targeted system may be a Linux VMware virtual machine.
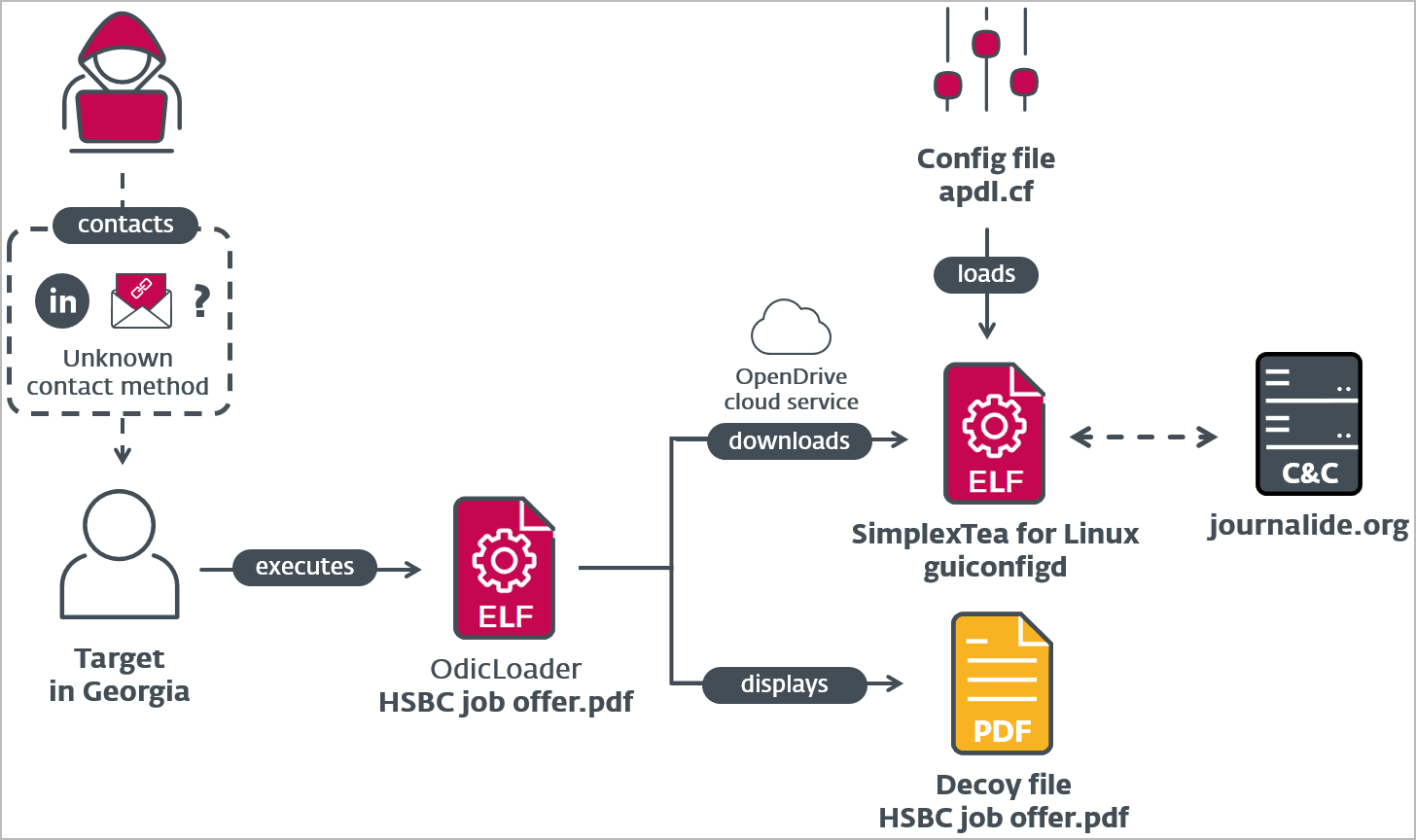 Lazarus’ latest attack chain against Linux targets (ESET)
Lazarus’ latest attack chain against Linux targets (ESET)
Trending: Offensive Security Tool: Mythic
Lazarus’ shift
Lazarus’ shift to Linux malware and the 3CX attack demonstrate their ever-evolving tactics, now supporting all major operating systems, including Windows and macOS. Similar Lazarus Operation DreamJob attacks have led to enormous success for the threat actors, allowing them to steal $620 million from Axie Infinity, and the FBI confirmed Lazarus was behind the $100 million cryptocurrency theft from the Harmony Bridge.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












