Legitimate Tool Turned Malicious: Freeze[.]rs Injector Used to Spread XWorm Malware
![Legitimate Tool Turned Malicious: Freeze[.]rs Injector Used to Spread XWorm Malware Legitimate Tool Turned Malicious: Freeze[.]rs Injector Used to Spread XWorm Malware](https://www.blackhatethicalhacking.com/wp-content/uploads/2023/08/Images-for-the-News-posts-9.png)
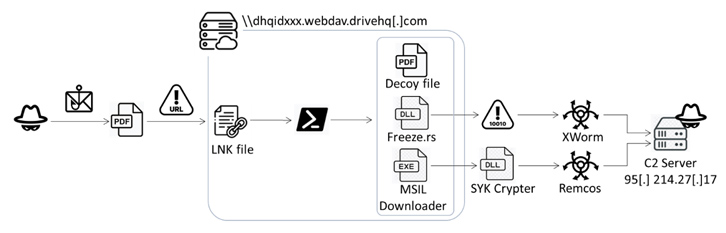
Malicious actors have seized upon the legitimate Rust-based injector “Freeze[.]rs” to deploy the XWorm commodity malware within victim environments. This innovative attack chain, detected by Fortinet FortiGuard Labs on July 13, 2023, is initiated through a phishing email containing a booby-trapped PDF file. The attack also showcases the use of Remcos RAT, facilitated by the SYK Crypter, which was first observed by Morphisec in May 2022.
Upon engagement with the malicious PDF file, it redirects to an HTML file, employing the ‘search-ms’ protocol to access an LNK file on a remote server. Clicking on this LNK file triggers the execution of a PowerShell script, which subsequently activates the Freeze[.]rs injector and SYK Crypter, enabling further malicious actions.
Freeze[.]rs, unveiled on May 4, 2023, initially served as an open-source red teaming tool by Optiv, designed for payload creation to elude security solutions and discreetly execute shellcode.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Cara Lin, a security researcher, highlights that “Freeze[.]rs employs a variety of techniques to eliminate Userland EDR hooks and execute shellcode in a manner that circumvents other endpoint monitoring controls.”
On the other hand, SYK Crypter is a utility employed to distribute an array of malware families such as AsyncRAT, NanoCore RAT, njRAT, QuasarRAT, RedLine Stealer, and Warzone RAT. It is fetched from the Discord content delivery network (CDN) via a .NET loader within emails, masquerading as innocuous purchase orders.
Morphisec researcher Hido Cohen describes the attack chain as employing a persistent crypter that incorporates multiple obfuscation layers and polymorphism, enhancing its capacity to evade detection by security solutions.
Notably, the “search-ms” URI protocol handler manipulation was recently highlighted by Trellix, exposing infection sequences involving HTML or PDF attachments, executing searches on attacker-controlled servers, and listing malicious files in Windows File Explorer to appear as local search results.
Fortinet’s findings align with this trend, revealing that files disguised as PDF files are actually LNK files. These LNK files initiate a PowerShell script, launching the Rust-based injector while concurrently displaying a decoy PDF document.
Trending: Recon Tool: RecoX
In the ultimate phase of this attack, the injected shellcode is decrypted to activate the XWorm remote access trojan, capable of harvesting sensitive data such as machine information, screenshots, and keystrokes. This enables remote control over the compromised device.
The expedited weaponization of a three-month-old program underscores the rapid assimilation of offensive tools by malicious actors to achieve their objectives. Furthermore, the PowerShell script’s actions encompass loading the injector and configuring the execution of an additional executable, which serves as a dropper, communicating with a remote server to retrieve the SYK Crypter containing the encrypted Remcos RAT malware.
Lin further elaborates, “The amalgamation of XWorm and Remcos creates a formidable trojan encompassing a spectrum of malicious functionalities.” The traffic report from the command and control (C2) server identifies Europe and North America as the primary targets of this malicious campaign.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












