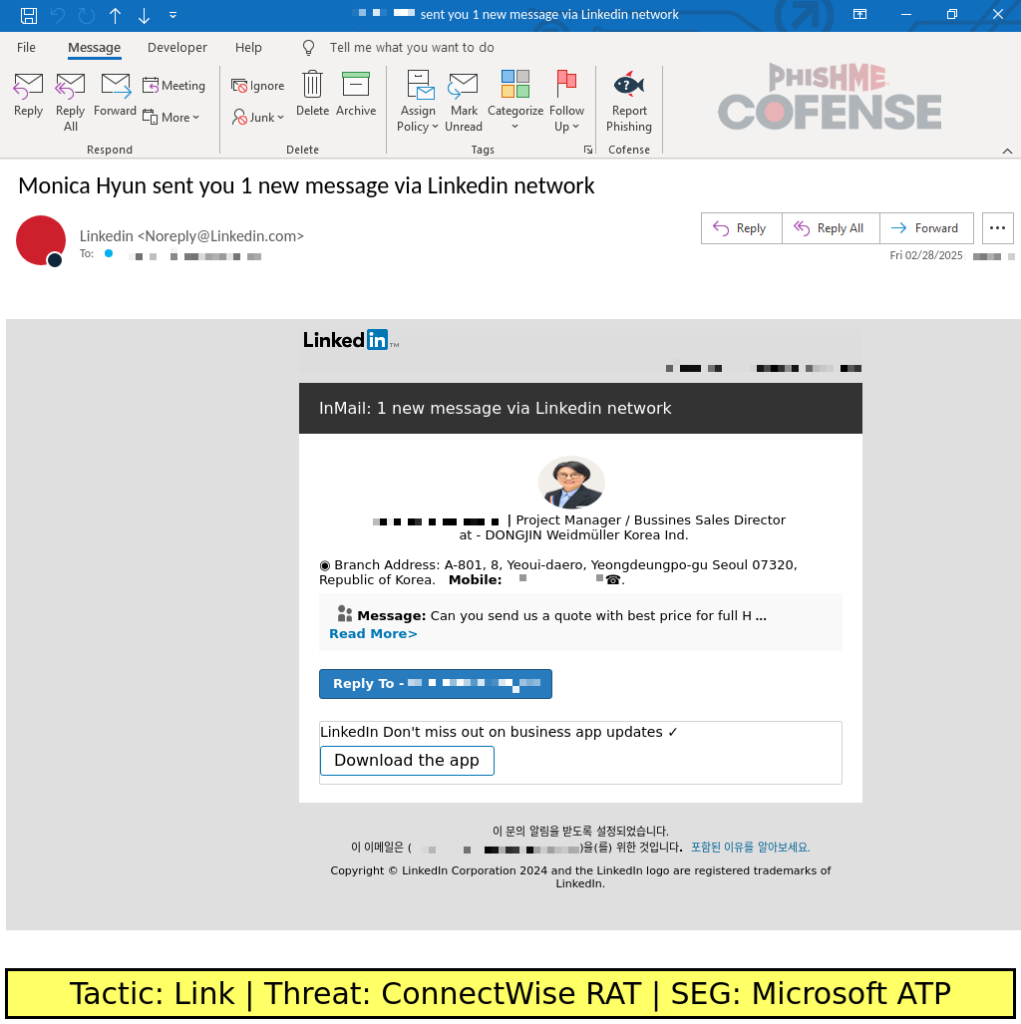
LinkedIn Phishing Scam Uses Fake InMail to Deliver ConnectWise RAT

Reading Time: 3 Minutes
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Why This Attack Is Dangerous
- Highly convincing LinkedIn branding increases trust.
- No direct download prompts to avoid suspicion.
- Bypasses email security due to weak SPF, DKIM, and DMARC settings.
- Deploys ConnectWise RAT, allowing remote control, data theft, and lateral movement.
Trending: Recon Tool: getJS
How to Protect Against This LinkedIn Phishing Attack
- Verify LinkedIn InMail Messages – Always check LinkedIn directly instead of clicking email links.
- Check SPF, DKIM & DMARC Policies – Configure DMARC to reject unauthenticated emails.
- Train Employees on Phishing Tactics – Educate teams on fake InMail scams & social engineering.
- Secure Email Gateway (SEG) Enhancements – Block emails with failed SPF/DKIM checks.
- Endpoint Protection & Network Monitoring – Detect suspicious RAT activity & prevent infections.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: hackread.com