Linux Version of Akira Ransomware Expands Reach, Targets VMware ESXi Servers
Akira ransomware operation has recently turned its attention to Linux-based VMware ESXi virtual machines, executing double-extortion attacks on companies worldwide.First emerging in March 2023, Akira initially targeted Windows systems across sectors such as education, finance, real estate, manufacturing, and consulting.
Similar to other ransomware groups that focus on enterprises, Akira’s threat actors engage in data theft from breached networks and encrypt files, thereby leveraging double extortion to demand hefty ransom payments that often soar into the millions of dollars. This ruthless modus operandi has already claimed over 30 victims in the United States alone, with two notable activity spikes in ID Ransomware submissions occurring in late May and the present period.
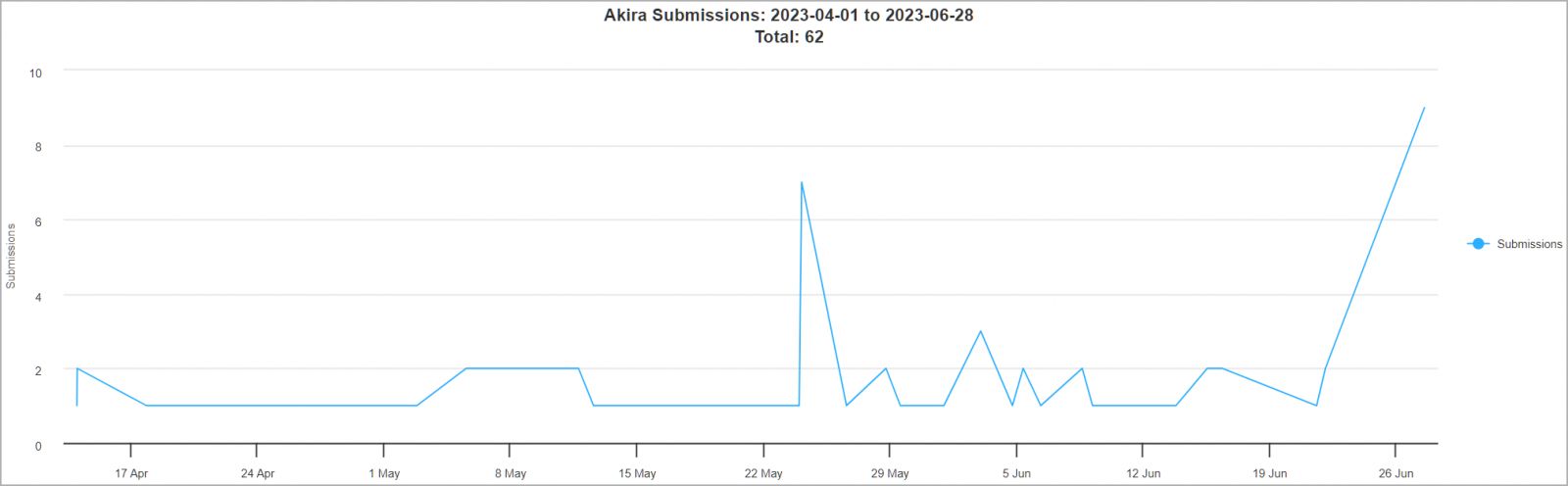 Akira activity in the past months
Akira activity in the past months
Source: BleepingComputer
Akira Ransomware Targets VMware ESXi Servers, Expands Global Reach
The latest development in Akira’s evolution came to light when malware analyst rivitna discovered a Linux version of the ransomware encryptor. Sharing a sample of this new encryptor on VirusTotal, rivitna drew attention to its project name, ‘Esxi_Build_Esxi6,’ which strongly suggests that the threat actors designed it with VMware ESXi servers as the primary target. The cyber-security experts at BleepingComputer conducted an in-depth analysis of the Linux encryptor, unearthing its distinct project files, including “/mnt/d/vcprojects/Esxi_Build_Esxi6/argh.h.”
Over the past few years, as enterprises increasingly adopted virtual machines for server deployment to enhance device management and optimize resource utilization, ransomware gangs have taken note and started developing customized Linux encryptors tailored specifically to target VMware ESXi servers. By exploiting ESXi servers, threat actors can effectively encrypt numerous servers running as virtual machines in a single operation.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
However, unlike other VMware ESXi encryptors scrutinized by BleepingComputer, Akira’s encryptors lack certain advanced features, such as the automatic shutdown of virtual machines using the esxcli command before initiating the file encryption process.
Nevertheless, the binary does support several command-line arguments that enable attackers to personalize their attacks. Of particular significance is the “-n” parameter, which allows threat actors to determine the extent of data encryption per file. Lower encryption settings result in faster encryption, but they also increase the likelihood of victims recovering their original files without resorting to paying the ransom.
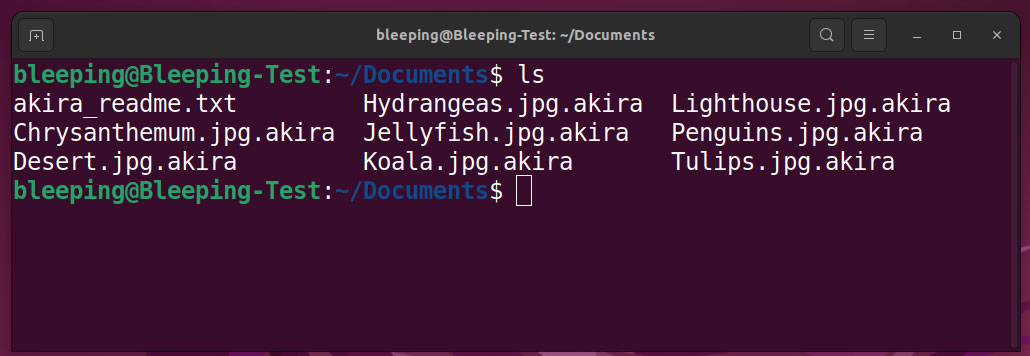 Files encrypted by Akira on a Linux server
Files encrypted by Akira on a Linux server
Source: BleepingComputer
The Linux variant of Akira employs a specific list of file extensions when encrypting data on targeted devices. Moreover, it intriguingly bypasses certain folders and files associated with Windows, suggesting that the Linux version might have been adapted from the Windows variant.
winnt, temp, thumb, $Recycle.Bin, $RECYCLE.BIN, System Volume Information, Boot, Windows, Trend Micro, .exe, .dll, .lnk, .sys, .msiAccording to analysts at Cyble, who released a report on the Linux version of Akira, the encryptor utilizes a public RSA encryption key and employs multiple symmetric key algorithms (such as AES, CAMELLIA, IDEA-CB, and DES) for file encryption. The victims’ files are encrypted using the symmetric key, which is subsequently encrypted with the RSA public key. This effectively prevents access to the decryption key unless the attackers’ RSA private decryption key is obtained.
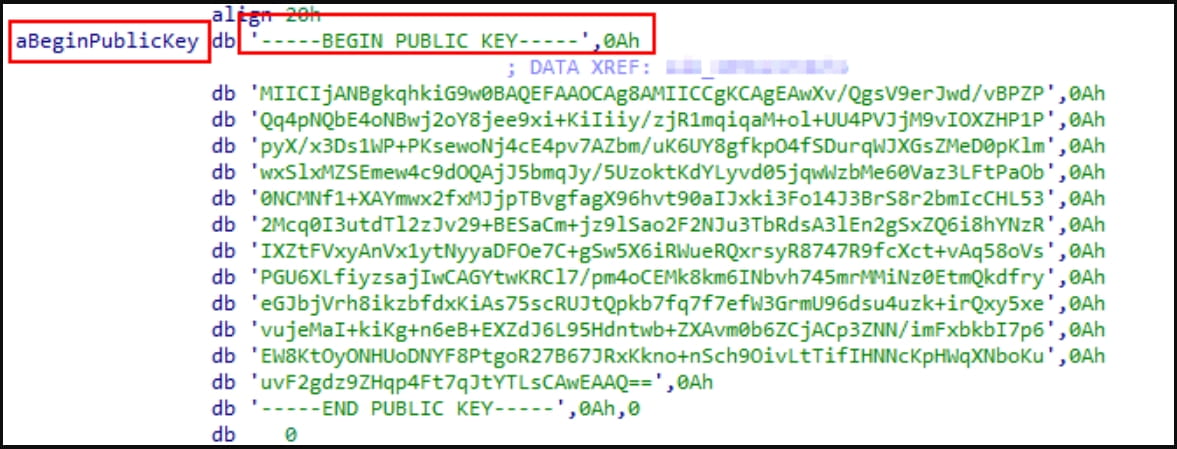 The public RSA key used by Akira (Cyble)
The public RSA key used by Akira (Cyble)
Trending: Exploiting LFI Vulnerabilities
Trending: Offensive Security Tool: SSRFPwned
As part of its signature, the Linux Akira encryptor appends the “.akira” extension to encrypted files and generates a ransom note named “akira_readme.txt” in each affected folder on the encrypted device.
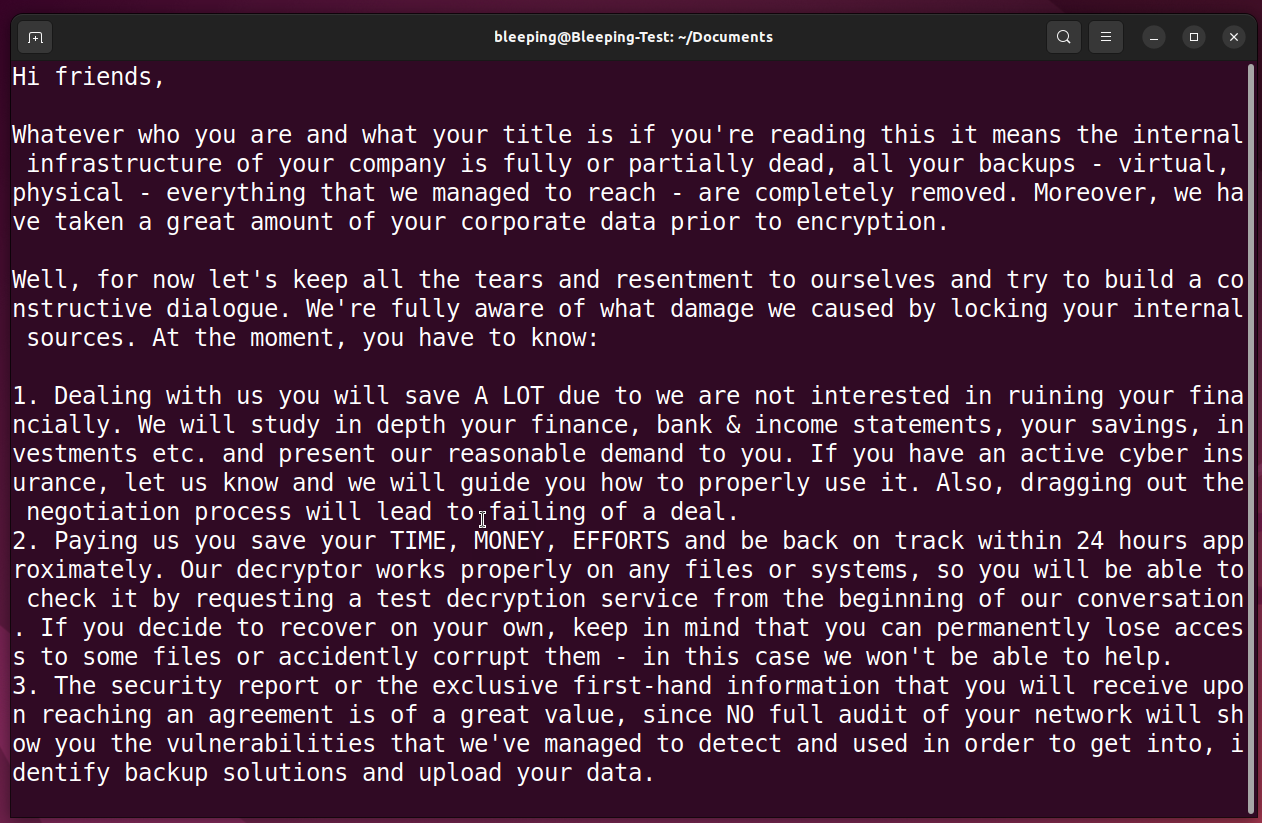 Akira ransom note dropped on Linux servers
Akira ransom note dropped on Linux servers
Source: BleepingComputer
The expanding scope of Akira’s targets underscores the escalating threat faced by organizations worldwide. Unfortunately, the trend of ransomware groups expanding their operations to include Linux platforms is on the rise, with many leveraging readily available tools to do so. This shift serves as an easy and lucrative strategy to maximize their profits. Notable ransomware operations that have adopted Linux ransomware encryptors, predominantly targeting VMware ESXi servers, include Royal, Black Basta, LockBit, BlackMatter, AvosLocker, REvil, HelloKitty, RansomEXX, and Hive.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












