LockBit Ransomware Gang Testing First-Ever Ransomware for macOS

LockBit Ransomware Gang Targets Macs with New Encryptors
The notorious LockBit ransomware gang has recently developed a new set of encryptors designed to target macOS devices for the first time, marking a significant milestone in the history of ransomware attacks. The new ransomware encryptors were discovered by cybersecurity researcher MalwareHunterTeam, who found them in a ZIP archive on VirusTotal that contained most of the available LockBit encryptors.
Historically, the LockBit operation had only used encryptors designed for attacks on Windows, Linux, and VMware ESXi servers. However, the archive also contained previously unknown encryptors for macOS, ARM, FreeBSD, MIPS, and SPARC CPUs, including one named ‘locker_Apple_M1_64’ that targets the newer Macs running on Apple Silicon, and lockers for PowerPC CPUs used by older Macs.
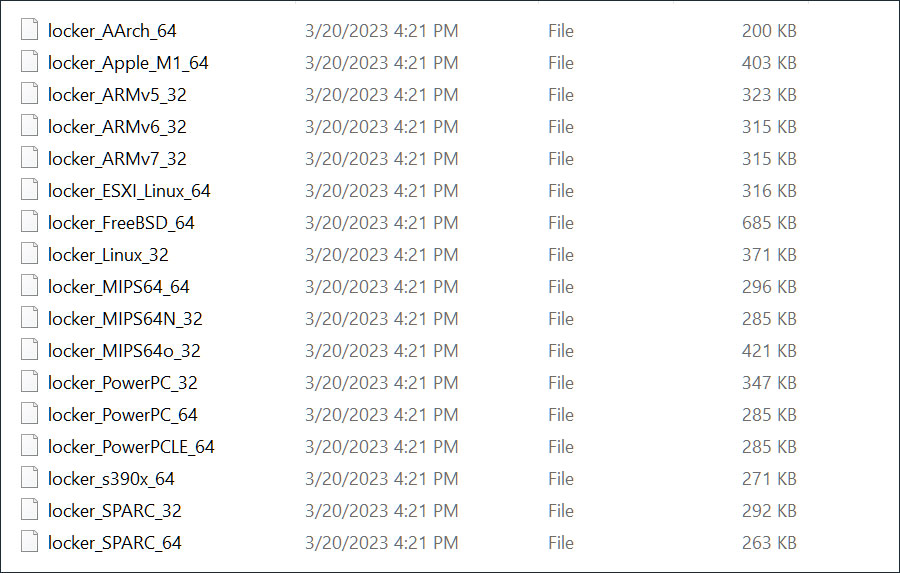
Archive of available LockBit encryptors
Source: BleepingComputer
Discovery of LockBit’s New Mac Encryptors on VirusTotal
Further research by cybersecurity researcher Florian Roth found an Apple M1 encryptor uploaded to VirusTotal in December 2022, indicating that these samples have been floating around for some time.
BleepingComputer analyzed the strings in the LockBit encryptor for Apple M1 and found strings that are out of place in a macOS encryptor, indicating that these were likely test builds. This includes numerous references to VMware ESXi, which is out of place in an Apple M1 encryptor, as VMware has announced they would not be supporting the CPU architecture.
_check_esxi
esxi_
_Esxi
_kill_esxi_1
_kill_esxi_2
_kill_esxi_3
_kill_processes
_kill_processes_Esxi
_killed_force_vm_id
_listvms
_esxcfg_scsidevs1
_esxcfg_scsidevs2
_esxcfg_scsidevs3
_esxi_disable
_esxi_enableAdditionally, the encryptor contains a list of sixty-five file extensions and filenames that will be excluded from encryption, all of them being Windows file extensions and folders.
A small snippet of the Windows files the Apple M1 encryptor will not encrypt is listed below, all out of place on a macOS device.
.exe
.bat
.dll
msstyles
gadget
winmd
ntldr
ntuser.dat.log
bootsect.bak
autorun.inf
thumbs.db
iconcache.dbSee Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The New Mac Encryptor Likely a Test Build
Despite the alarming nature of this discovery, cybersecurity experts remain optimistic that these encryptors are not yet ready for deployment in actual attacks against macOS devices. Cisco Talos researcher Azim Khodjibaev stated that the encryptors were meant as a test and were never intended for deployment in live cyberattacks.
MacOS cybersecurity expert Patrick Wardle further confirmed this theory, stating that the encryptor is far from complete as it is missing the required functionality to encrypt Macs properly. Wardle believes the macOS encryptor is based on the Linux version and compiled for macOS with some basic configuration settings, and that when launched, it crashes due to a buffer overflow bug in its code.
Worth stressing, as LockBit macOS sample though *compiled* for macOS really isn't (yet) designed for macOS.
1. Unsigned (won't easily run on macOS)
2. Doesn't appear to take into account TCC/SIP, so won't be able to encrypt much of anythingSo (in current form) macOS impact: ~0 https://t.co/zYVNhfYLRo
— Patrick Wardle (@patrickwardle) April 16, 2023
LockBit’s Plans for Developing Mac Encryptor
While LockBit’s development of a macOS encryptor is concerning, it’s important to remember that all computer users, including Mac owners, should practice good online safety habits, including keeping the operating system updated, avoiding opening unknown attachments and executables, generating offline backups, and using strong and unique passwords at every site they visit.
As LockBit is known for pushing the envelope in ransomware development, it would not be surprising to see more advanced and optimized encryptors for these CPU architectures released in the future.
Trending: Offensive Security Tool: Mythic
In response to questions from BleepingComputer, the public-facing representative of LockBit, known as LockBitSupp, said that the Mac encryptor is “actively being developed.” While LockBit has a history of toying with security researchers and the media, if true, we will likely see more production-quality versions in the future.
Additionally, while it’s not clear how useful a macOS encryptor would be in the enterprise, some LockBit affiliates target consumers and small businesses, where an encryptor like this could be more useful.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: info@blackhatethicalhacking.com
Source: bleepingcomputer.com












