LockBit Ransomware Resurfaces, Threatening Government Sector Amid Infrastructure Relaunch

The infamous LockBit gang has quickly resumed its ransomware operation on new infrastructure, less than a week after law enforcement authorities infiltrated its systems, inflicting a crushing blow. With a chilling message to government institutions, the gang threatens to escalate its attacks on the public sector.
In a message veiled under a mock FBI leak, the LockBit syndicate issued a detailed statement acknowledging their recent setback, attributing it to their own complacency and negligence. Dubbed ‘Operation Cronos,’ the disruption orchestrated by law enforcement prompted LockBit to concede to “personal negligence and irresponsibility” as the root cause of the breach.
Undeterred by the setback, LockBit has resurfaced under the same brand name, relocating its data leak site to a new .onion address, showcasing a countdown timer for the impending release of stolen information from five identified victims.
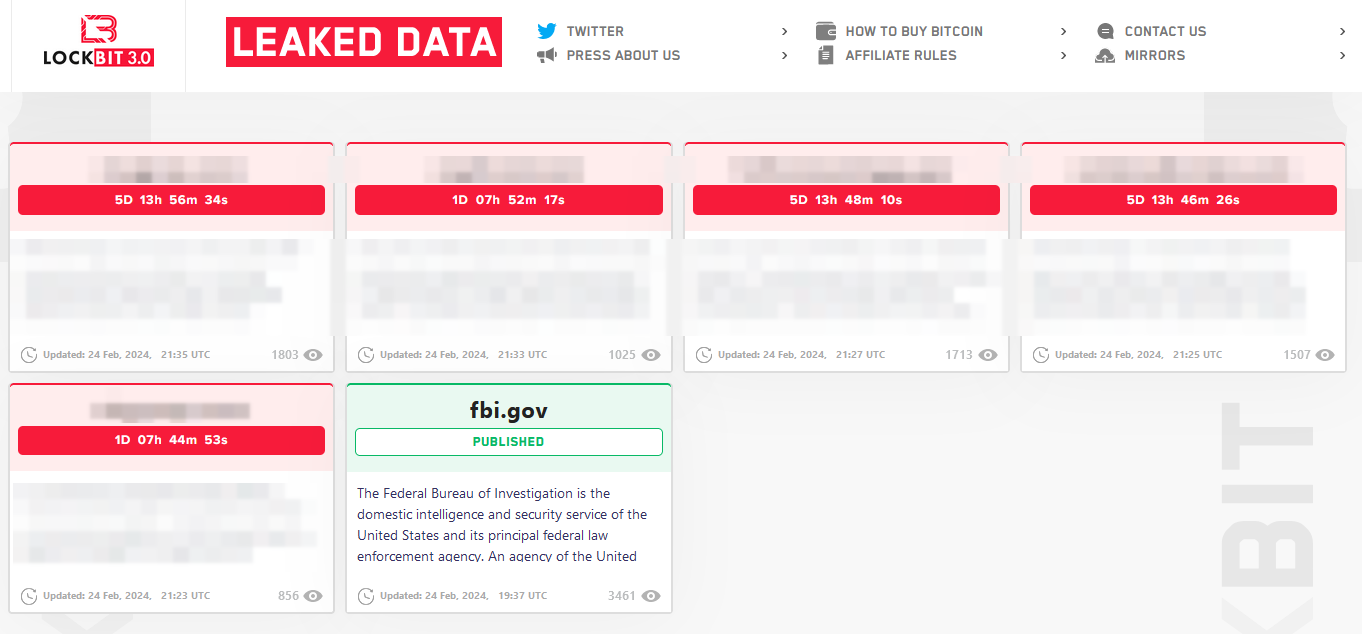 Relaunched LockBit data leak site shows five victims
Relaunched LockBit data leak site shows five victims
source: BleepingComputer
The takedown on February 19 dismantled LockBit’s infrastructure, comprising 34 servers housing critical data, cryptocurrency addresses, decryption keys, and the affiliate panel. Despite this setback, the gang swiftly regrouped, offering insights into the breach and outlining strategies to fortify their operations against future intrusions.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
LockBit attributes the breach to outdated PHP servers, highlighting their own negligence in maintaining up-to-date software. In a candid admission, the threat actor concedes to a lack of vigilance over the years, resulting in vulnerabilities that were exploited by law enforcement. The gang promptly updated their PHP servers and announced rewards for identifying vulnerabilities in the latest version.
Speculating on the motive behind the law enforcement intervention, LockBit suggests retaliation for the ransomware attack on Fulton County in January, hinting at potential leaks of sensitive information. In a bold move, LockBit threatens to escalate attacks on government entities, challenging law enforcement to demonstrate their capability in countering such assaults.
In the aftermath of ‘Operation Cronos,’ LockBit plans to bolster security measures, including decentralized affiliate panels and manual release of decryptors. By segregating the panel and enhancing decentralization, LockBit aims to mitigate the risk of future breaches and restore trust among affiliates.
Trending: Major Cyber Attacks that shaped 2023


