LummaC2 Strikes Again: Cybercriminals Now Claim to Revive Expired Google Cookies for Account Hijacking

The Lumma information-stealer malware, also known as ‘LummaC2,’ has introduced a chilling new capability, allowing cybercriminals to allegedly restore expired Google cookies. These session cookies, critical for seamless logins, typically have a limited lifespan to prevent unauthorized access. However, Lumma operators claim to offer a feature that can bring these expired cookies back to life, potentially granting unauthorized access to Google accounts even after the legitimate owner has logged out.
The update, announced on November 14, boasts the “ability to restore dead cookies using a key from restore files,” specifically targeting Google cookies. Strikingly, this feature is exclusively available to subscribers of Lumma’s highest-tier “Corporate” plan, costing cybercriminals $1,000 per month.
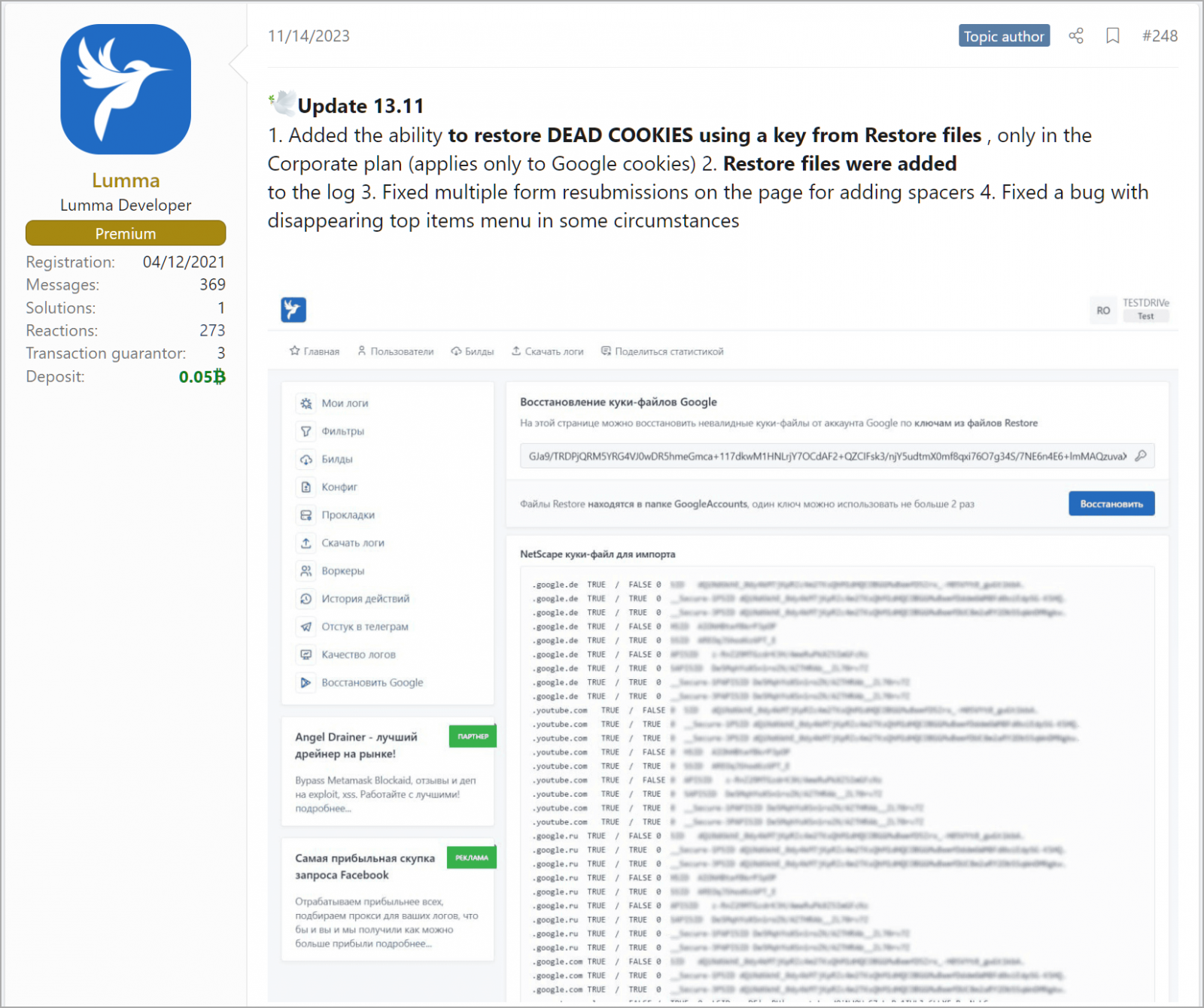 Lumma announcing new, powerful feature
Lumma announcing new, powerful feature
Source: BleepingComputer
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The forum post detailing this feature is the first public mention of such a capability, raising concerns within the cybersecurity community. The announcement suggests that each key can be used twice, allowing for a single instance of cookie restoration. While the legitimacy of this claim is yet to be verified by security researchers or Google, its potential implications for account security are significant.
Interestingly, another information-stealer, Rhadamanthys, has also announced a similar capability in a recent update, suggesting a possible security gap discovered by malware authors.
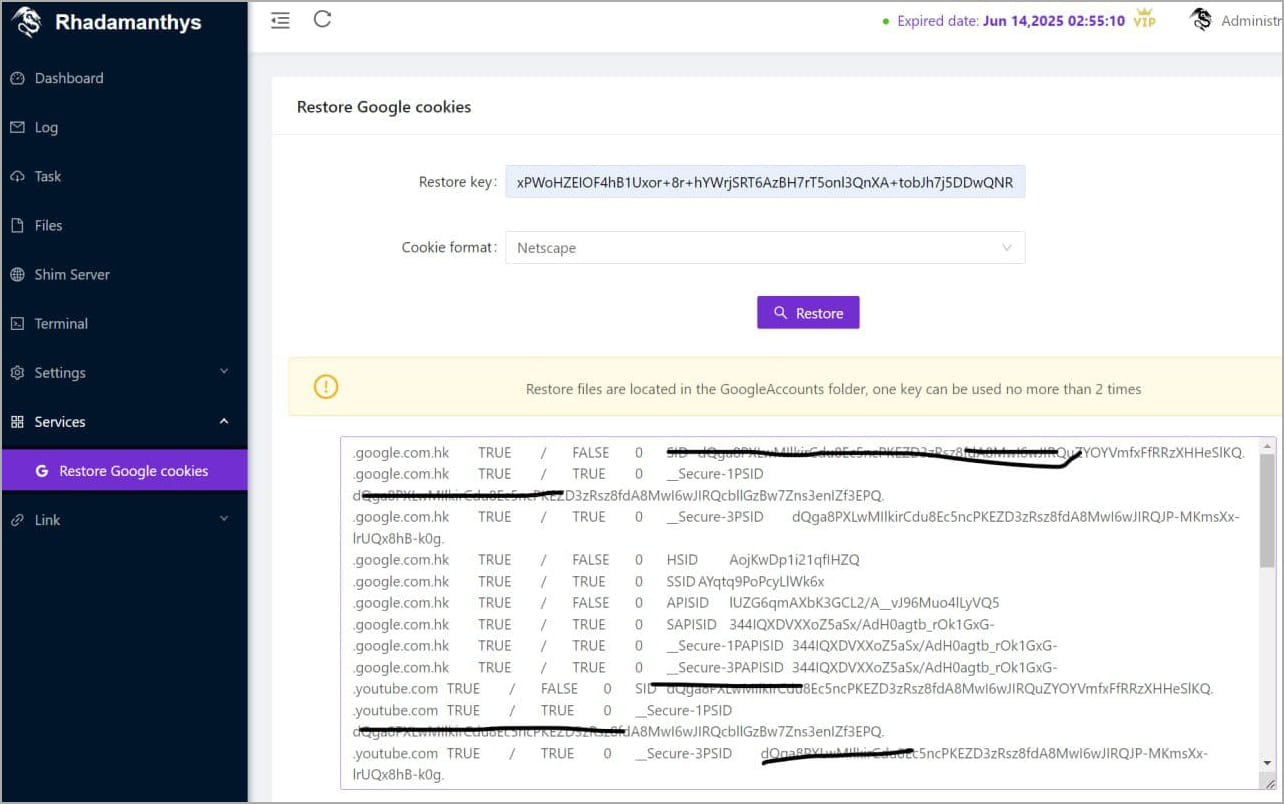 Rhadamanthys Stealer also claiming to offer Google cookie restoration
Rhadamanthys Stealer also claiming to offer Google cookie restoration
Source: @g0njxa
BleepingComputer has reached out to Google for comments on the potential vulnerability in session cookies, but as of now, there has been no response. Lumma’s developers released an update in response to newly introduced restrictions by Google, reinforcing the urgency and severity of the situation.
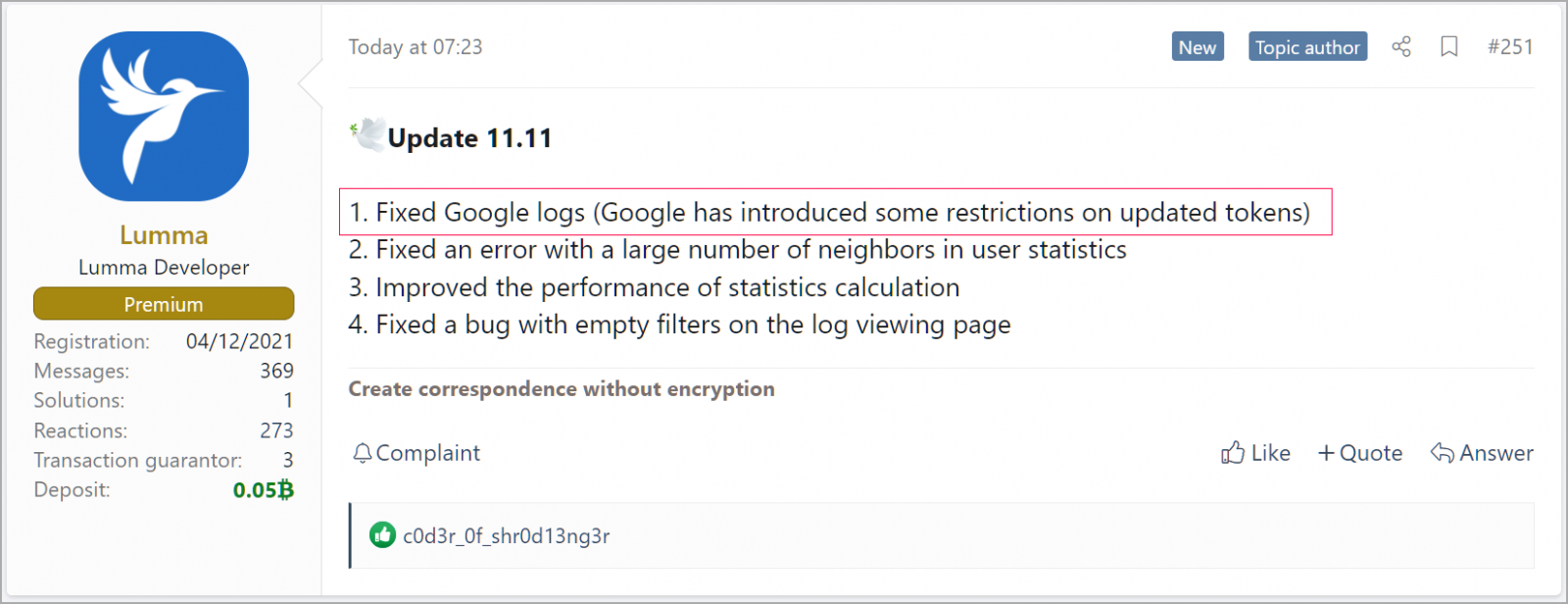 Lumma update to address restrictions
Lumma update to address restrictions
Source: BleepingComputer
Trending: Recon Tool: subby
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













