Major Companies Hit in Ongoing 3CX VoIP Supply Chain Attack

Compromised 3CX softphone app
Hackers are using a trojanized version of the 3CX Voice Over Internet Protocol (VoIP) desktop client to target the software development company’s customers in an ongoing supply chain attack. 3CX’s customer list boasts a number of high-profile organizations, including American Express, Coca-Cola, McDonald’s, and Toyota.
Security researchers from Sophos and CrowdStrike have reported that the attackers are targeting both Windows and macOS users of the compromised 3CX softphone app. The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small number of cases, hands-on-keyboard activity.
While CrowdStrike suspects a North Korean state-backed hacking group it tracks as Labyrinth Collima is behind this attack, Sophos’ researchers say they “cannot verify this attribution with high confidence.” Labyrinth Collima activity is known to overlap with other threat actors tracked as Lazarus Group by Kaspersky, Covellite by Dragos, UNC4034 by Mandiant, Zinc by Microsoft, and Nickel Academy by Secureworks.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
SmoothOperator software supply chain attack
The trojanized 3CX desktop app is being downloaded in a supply chain attack that has been dubbed ‘SmoothOperator’ by SentinelOne. When the installer is downloaded from 3CX’s website or an update is pushed to an already installed desktop application, it extracts a malicious ffmpeg.dll and the d3dcompiler_47.dll DLL files, which are used to perform the next stage of the attack.
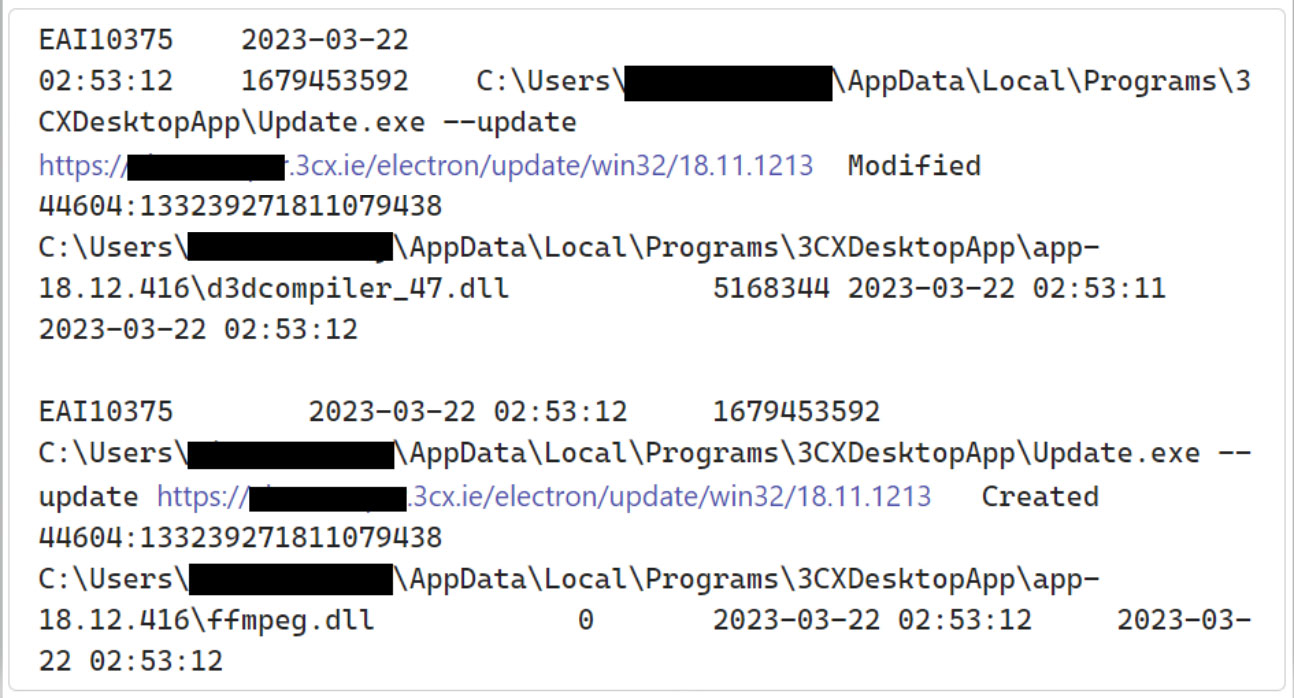
Update process installing the malicous files (Sophos)
Although Sophos states that the 3CXDesktopApp.exe executable is not malicious, the malicious ffmpeg.dll DLL will be sideloaded and used to extract an encrypted payload from d3dcompiler_47.dll and execute it. The malware then downloads icon files hosted on GitHub that contain Base64 encoded strings appended to the end of the images.
The GitHub repository where these icons are stored shows that the first icon was uploaded on December 7th, 2022. The first-stage malware uses these Base64 strings to download a final payload to the compromised devices, a previously unknown information-stealing malware downloaded as a DLL.
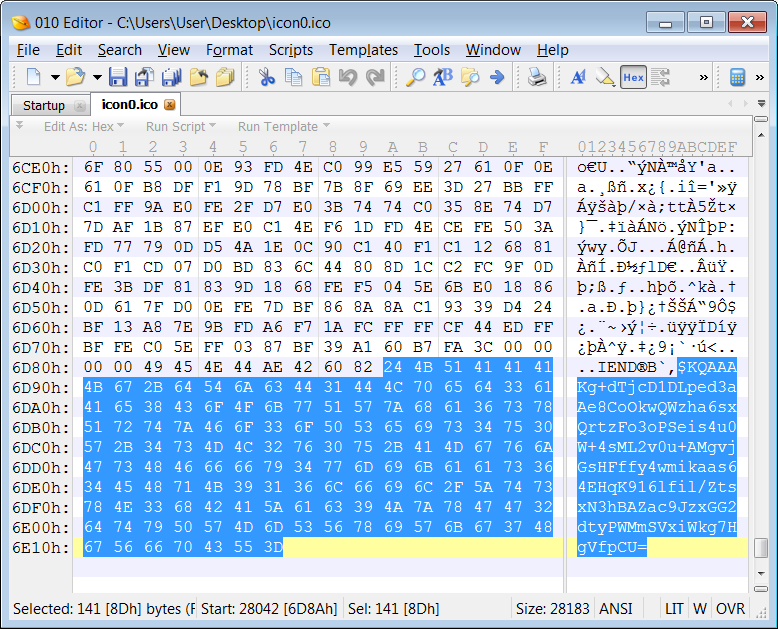 Base64 strings embedded in ICO files (BleepingComputer)
Base64 strings embedded in ICO files (BleepingComputer)
This new malware is capable of harvesting system info and stealing data and stored credentials from Chrome, Edge, Brave, and Firefox user profiles. SentinelOne has stated that they cannot confirm that the Mac installer is similarly trojanized, but their ongoing investigation includes additional applications like the Chrome extension that could also be used to stage attacks.
Multiple customers in 3CX’s forums have reported that they have been receiving alerts from SentinelOne, CrowdStrike, ESET, Palo Alto Networks, and SonicWall security software, saying that the VoIP client app was marked as malicious. Customers report that the security alerts are triggered after installing specific versions of the software on Windows and Macs.
Trending: Offensive Security Tool: OpenRediWrecked
Multiple cybersecurity firms detect trojanized 3CX softphone client signed with legitimate certificate
One of the trojanized 3CX softphone client samples shared by CrowdStrike was digitally signed with a legitimate 3CX Ltd certificate issued by DigiCert over three weeks ago. This same certificate was used in older versions of 3CX software.
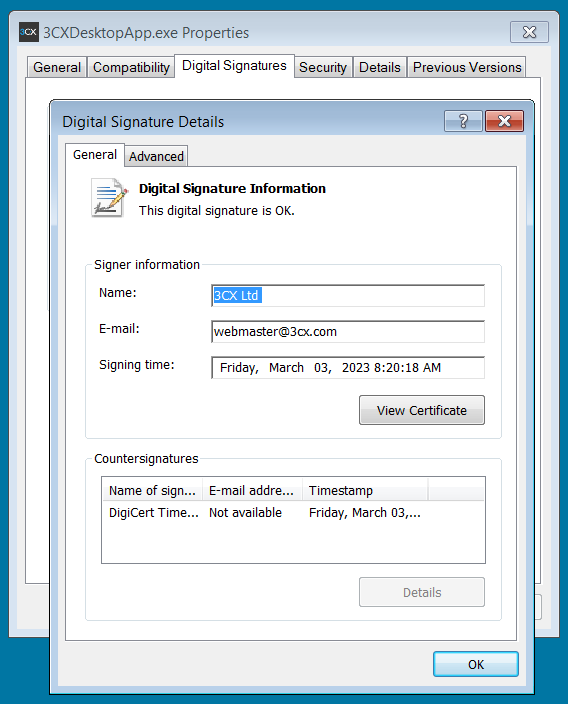 Signed 3CX VoIP client app (BleepingComputer)
Signed 3CX VoIP client app (BleepingComputer)
SentinelOne detects “penetration framework or shellcode” while analyzing the 3CXDesktopApp.exe binary, ESET tags it as a “Win64/Agent.CFM” trojan, Sophos as “Troj/Loader-AF”, and CrowdStrike’s Falcon OverWatch managed threat hunting service warns users to investigate their systems for malicious activity “urgently.”
While 3CX’s support team members tagged it as a potential SentinelOne false positive in one of the forum threads filled with customer reports on Wednesday, the company is yet to provide a formal statement or issue a security advisory to its customers.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












