Malicious Mozilla Firefox Extension Allows Gmail Takeover

Reading Time: 1 Minute
A newly uncovered cyberattack is taking control of victims’ Gmail accounts, by using a customized, malicious Mozilla Firefox browser extension called FriarFox.
Researchers say the threat campaign, observed in January and February, targeted Tibetan organizations and was tied to TA413, a known advanced persistent threat (APT) group that researchers believe to be aligned with the Chinese state.
The group behind this attack aims to gather information on victims by snooping in on their Firefox browser data and Gmail messages, said researchers.
After installation, FriarFox gives cybercriminals various types of access to users’ Gmail accounts and Firefox browser data.
For instance, cybercriminals have the ability to search, read, label, delete, forward and archive emails, receive Gmail notifications and send mail from the compromised account. And, given their Firefox browser access, they could access user data for all websites, display notifications, read and modify privacy settings, and access browser tabs.
“The introduction of the FriarFox browser extension in TA413’s arsenal further diversifies a varied, albeit technically limited repertoire of tooling,” said Proofpoint on Thursday. “The use of browser extensions to target the private Gmail accounts of users, combined with the delivery of Scanbox malware, demonstrates the malleability of TA413 when targeting dissident communities.”
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
The Cyberattack: Stemming From Malicious Emails
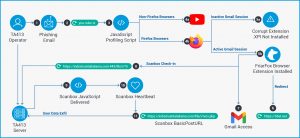
The attack stemmed from phishing emails (first detected in late January), targeting several Tibetan organizations. One of the emails uncovered by researchers purported to be from the “Tibetan Women’s Association,” which is a legitimate group based in India. The subject of the email was: “Inside Tibet and from the Tibetan exile community.”
Researchers noted that the emails were delivered from a known TA413 Gmail account, which has been in use for several years. The email impersonates the Bureau of His Holiness the Dalai Lama in India, said researchers.
The email contained a malicious URL, which impersonated a YouTube page (hxxps://you-tube[.]tv/). In reality, this link took recipients to a fake Adobe Flash Player update-themed landing page, where the process of downloading the malicious browser extension begins.
Fake Adobe Flash Player Page and FriarFox Download
The malicious “update” page then executes several JavaScript files, which profile the user’s system and determine whether or not to deliver the malicious FriarFox extension; the installation of FriarFox depends on several conditions.
“Threat actors appear to be targeting users that are utilizing a Firefox Browser and are utilizing Gmail in that browser,” the researchers said. “The user must access the URL from a Firefox browser to receive the browser extension. Additionally, it appeared that the user must be actively logged in to a Gmail account with that browser to successfully install the malicious XPI [FriarFox] file.”
See Also: Offensive Security Tool: ScareCrow
Firefox users with an active Gmail session are immediately served the FriarFox extension (from hxxps://you-tube[.]tv/download.php) with a prompt that enables the download of software from the site.
They are prompted to add the browser extension (by approving the extension’s permissions), which claims to be “Flash update components.”
But the threat actors also utilize various tricks against users who are either not using a Firefox browser and/or who do not have an active Gmail session.
For instance, one user who did not have an active Gmail session and wasn’t using Firefox was redirected to the legitimate YouTube login page, after visiting the fake Adobe Flash Player landing page. The attackers then attempted to access an active domain cookie in use on the site.
In this situation, “actors may be attempting to leverage this domain cookie to access the user’s Gmail account in the instance that a GSuite federated login session is used to log in to the user’s YouTube account,” said researchers. However, “this user is not served the FriarFox browser extension.”
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
See Also: Hacking Stories: Albert Gonzalez & the ‘Get Rich or Die Trying’ Crew who stole 130 million credit-card numbers
FriarFox Browser Extension: Malicious Capabilities
Researchers said that FriarFox appears to be based on an open-source tool called “Gmail Notifier (restartless).” This is a free tool that’s available from various locations, including GitHub, the Mozilla Firefox Browser Add-Ons store and the QQ App store. The malicious extension also comes in the form of an XPI file, noted researchers – these files are compressed installation archives used by various Mozilla applications, and contain the contents of a Firefox browser extension.
“TA413 threat actors altered several sections of the open-source browser extension Gmail Notifier to enhance its malicious functionality, conceal browser alerts to victims and disguise the extension as an Adobe Flash-related tool,” said researchers.
After FriarFox is installed, one of the Javascript files (tabletView.js) also contacts an actor-controlled server to retrieve the Scanbox framework. Scanbox is a PHP and JavaScript-based reconnaissance framework that can collect information about victim systems, which dates to 2014.
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
TA413 Threat Group: Continually Evolving
TA413 has been associated with Chinese state interests and is known for targeting the Tibetan community. As recently as September, the China-based APT was sending organizations spear-phishing emails that distribute a never-before-seen intelligence-collecting RAT dubbed Sepulcher.
“While not conventionally sophisticated when compared to other active APT groups, TA413 combines modified open-source tools, dated shared reconnaissance frameworks, a variety of delivery vectors and very targeted social-engineering tactics,” said researchers.
Researchers said this latest campaign shows that TA413 appears to be pivoting to using more modified open-source tooling to compromise victims.
“Unlike many APT groups, the public disclosure of campaigns, tools and infrastructure has not led to significant TA413 operational changes,” they said. “Accordingly, we anticipate continued use of a similar modus operandi targeting members of the Tibetan diaspora in the future.”
Source: threatpost.com
(Click Link)