Malicious WinRAR SFX Files Slipping Past Traditional AV Solutions

Cybersecurity Researchers at CrowdStrike Uncover New Technique for Evading Detection
Researchers from cybersecurity firm CrowdStrike have discovered that hackers are adding malicious functionality to self-extracting archives (SFX) created with compression software like WinRAR or 7-Zip. By including harmless decoy files in the SFX files, attackers can plant backdoors without triggering the security agent on the target system.
SFX files are essentially executables that contain archived data along with a built-in decompression stub, which is the code used for unpacking the data. These files can be password-protected to prevent unauthorized access and simplify distribution of archived data to users who do not have a utility to extract the package.
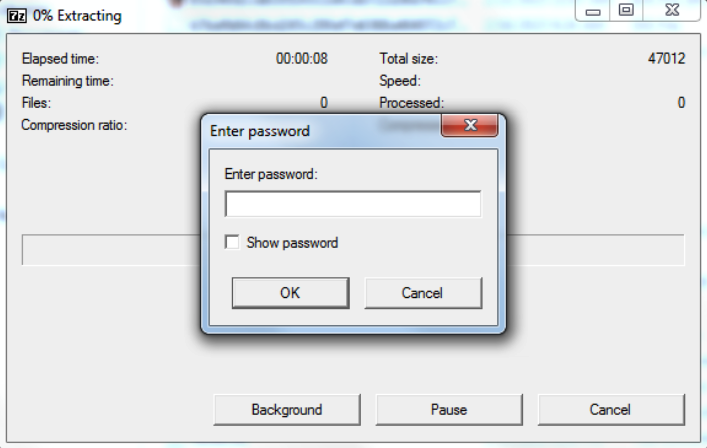 Password-protected SFX created with 7-Zip
Password-protected SFX created with 7-Zip
source: CrowdStrike
CrowdStrike’s analysis discovered an adversary that used stolen credentials to abuse ‘utilman.exe’ and launch a password-protected SFX file that had been planted on the system previously. Utilman is an accessibility application that can be executed before user login, often abused by hackers to bypass system authentication.
 The utilman tool on login screen
The utilman tool on login screen
source: CrowdStrike
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Attackers Exploit WinRAR’s Advanced Options to Run Malicious Scripts with System Privileges
The SFX file triggered by utilman.exe is password-protected and contains an empty text file that serves as a decoy. The real function of the SFX file is to abuse WinRAR’s setup options to run PowerShell, Windows command prompt (cmd.exe), and task manager with system privileges.
The attacker customized the SFX archive so that no dialog or window was displayed during the extraction process. The threat actor also added instructions to run PowerShell, command prompt, and task manager. WinRAR offers a set of advanced SFX options that allow adding a list of executables to run automatically before or after the process, as well as overwrite existing files in the destination folder if entries with the same name exist.
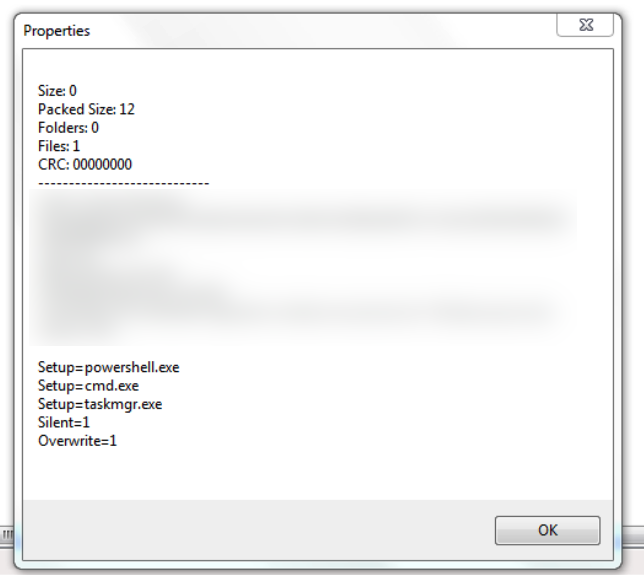 Commands in WinRAR SFX setup that allow backdoor access
Commands in WinRAR SFX setup that allow backdoor access
source: CrowdStrike
Trending: Offensive Security Tool: Nginxpwner
Unlikely to be flagged by AV
As this type of attack is unlikely to be caught by traditional antivirus software that is looking for malware inside of an archive, CrowdStrike advises users to pay particular attention to SFX archives and use appropriate software to check the content of the archive and look for potential scripts or commands scheduled to run upon extraction.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












