Mallox Ransomware Targets Linux Systems with Modified Kryptina Code

An affiliate of the Mallox ransomware operation, also known as TargetCompany, has been observed using a slightly modified version of the Kryptina ransomware to launch attacks on Linux systems. The findings, revealed by SentinelLabs, mark a significant evolution in the tactics of Mallox, which previously focused exclusively on Windows targets.
This shift highlights the growing trend of ransomware groups expanding their scope to include Linux and VMware ESXi environments, which are prevalent in enterprise and cloud infrastructure. SentinelLabs’ discovery points to the increasing adoption of cross-platform capabilities within the ransomware ecosystem.
From Kryptina to Mallox: A Cross-Platform Expansion
Kryptina was initially launched in late 2023 as a low-cost Ransomware-as-a-Service (RaaS) platform, designed specifically to target Linux systems. The service was offered to cybercriminals for prices ranging between $500 and $800, but it failed to gain significant traction in the underground cybercrime community.
In February 2024, Kryptina’s administrator, operating under the alias “Corlys,” leaked its source code for free on several hacking forums. This leak made the ransomware accessible to a wider range of cybercriminal actors, leading to its adoption by random groups interested in Linux-targeting malware.
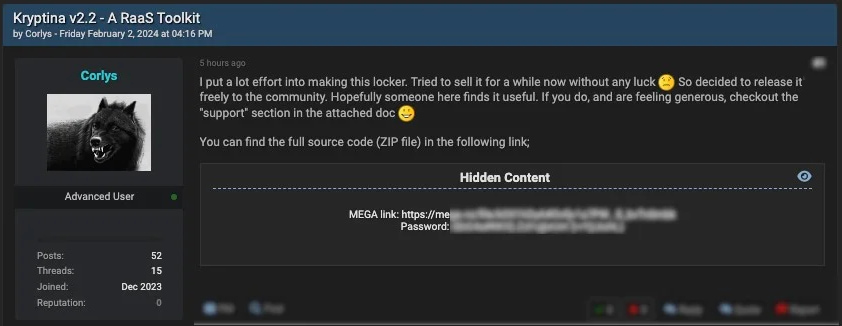 Threat actor leaking the source code
Threat actor leaking the source code
Source: SentinelLabs
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
The Mallox affiliate discovered by SentinelLabs exploited this leak, using Kryptina’s source code to develop a rebranded payload called Mallox Linux 1.0. This new variant utilizes Kryptina’s original AES-256-CBC encryption scheme, decryption routines, and command-line builder, with only minor modifications. Essentially, the affiliate rebranded the ransomware while keeping its core functionalities intact, removing references to Kryptina from the ransom notes, scripts, and files.
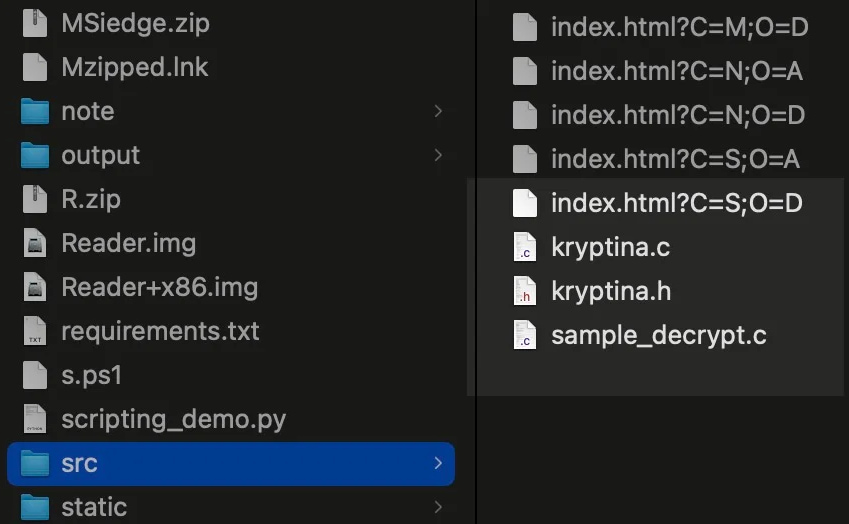 Kryptina source code on the exposed server
Kryptina source code on the exposed server
Source: SentinelLabs
Evolution of Mallox Ransomware Operations
Historically, Mallox has been a Windows-targeting ransomware operation. However, this latest discovery underscores the group’s pivot towards Linux environments, aligning with broader ransomware trends that target critical infrastructure such as VMware ESXi systems.
Mallox Linux 1.0 retains the simplicity of its predecessor, Kryptina, but with a new name and slightly tweaked documentation. This suggests that the affiliate focused primarily on rebranding while leveraging Kryptina’s functional and efficient encryption code.
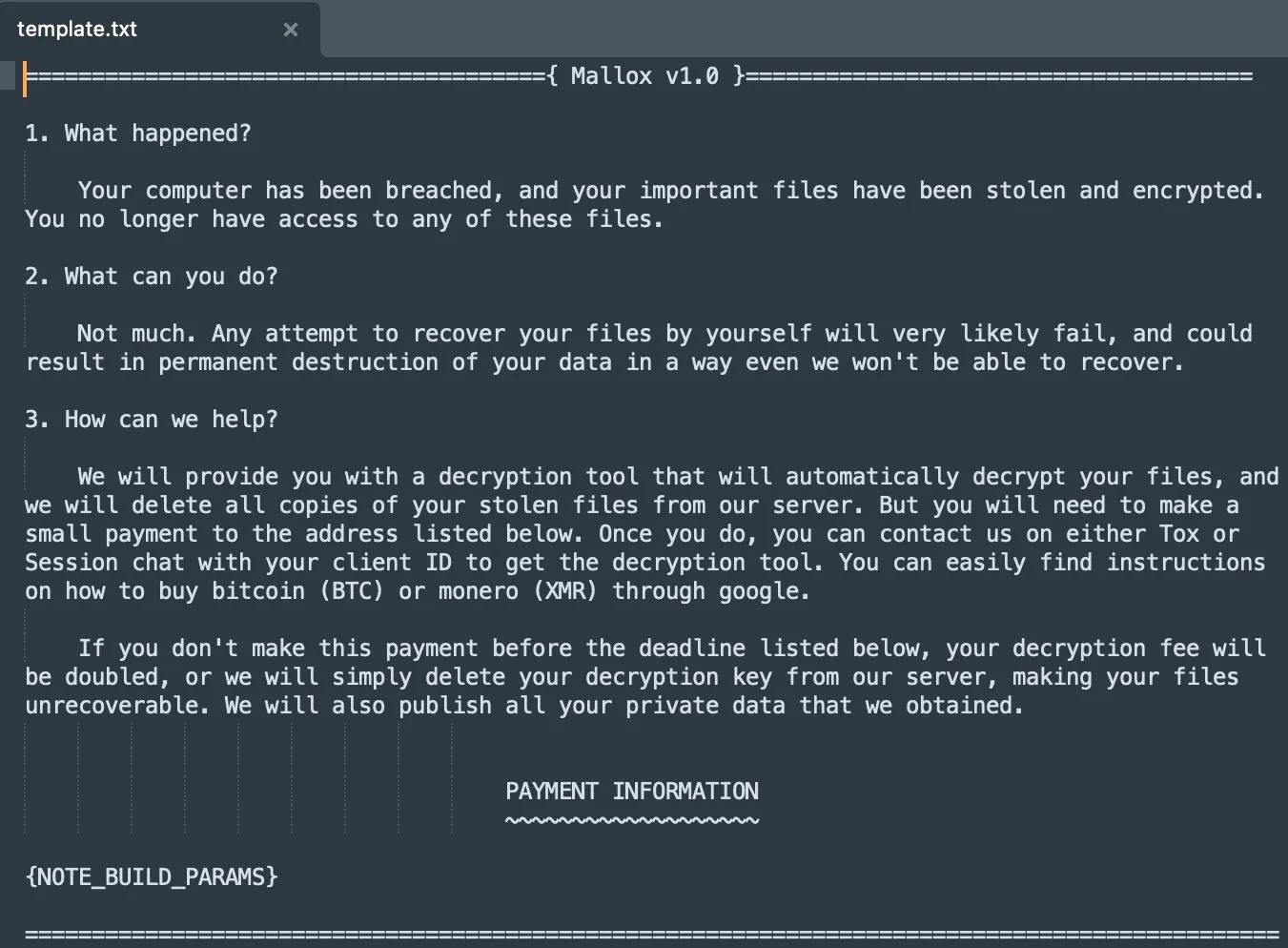 The Mallox Linux 1.0 ransom note
The Mallox Linux 1.0 ransom note
Source: SentinelLabs
In addition to the Linux-targeting variant, SentinelLabs uncovered other tools associated with the Mallox operation, including:
- A Kaspersky password reset tool (KLAPR.BAT), a legitimate utility possibly used for gaining unauthorized access to compromised systems.
- An exploit for CVE-2024-21338, a privilege escalation vulnerability affecting Windows 10 and 11.
- Privilege escalation PowerShell scripts, potentially used to elevate access rights on Windows systems.
- Java-based Mallox payload droppers, which could be employed to deliver ransomware payloads across different platforms.
- Disk image files containing pre-configured Mallox payloads, ready for deployment.
- Data folders for 14 potential victims, indicating ongoing operations targeting organizations.
Trending: Offensive Security Tool: DDoSlayer
Uncertainty Remains Regarding Mallox Affiliates
One of the most intriguing aspects of the SentinelLabs findings is the ambiguity surrounding the extent of the Mallox Linux 1.0 variant’s deployment. It is currently unclear whether this variant is exclusively used by the affiliate that adopted Kryptina’s code, or if multiple affiliates within the Mallox ransomware operation are now leveraging this new Linux-targeting ransomware.
SentinelLabs’ research highlights that other Mallox affiliates may also be using different Linux variants, as previously observed in an attack campaign analyzed by Trend Micro in June 2023. This signals that Mallox operators are diversifying their attack arsenal to increase the scope of their ransomware campaigns.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













