Malware Delivery Exploit Found in Microsoft Teams Allows Attacks from External Sources

Security researchers from UK-based security services company Jumpsec have identified a method to deliver malware through Microsoft Teams, bypassing the application’s restrictions on files from external sources.
Attack Method
The attack method leverages Microsoft Teams’ default configuration, which allows communication with external tenant accounts. While this communication bridge alone could be used for social engineering and phishing attacks, the researchers discovered a more powerful approach that involves sending a malicious payload directly to a target inbox.
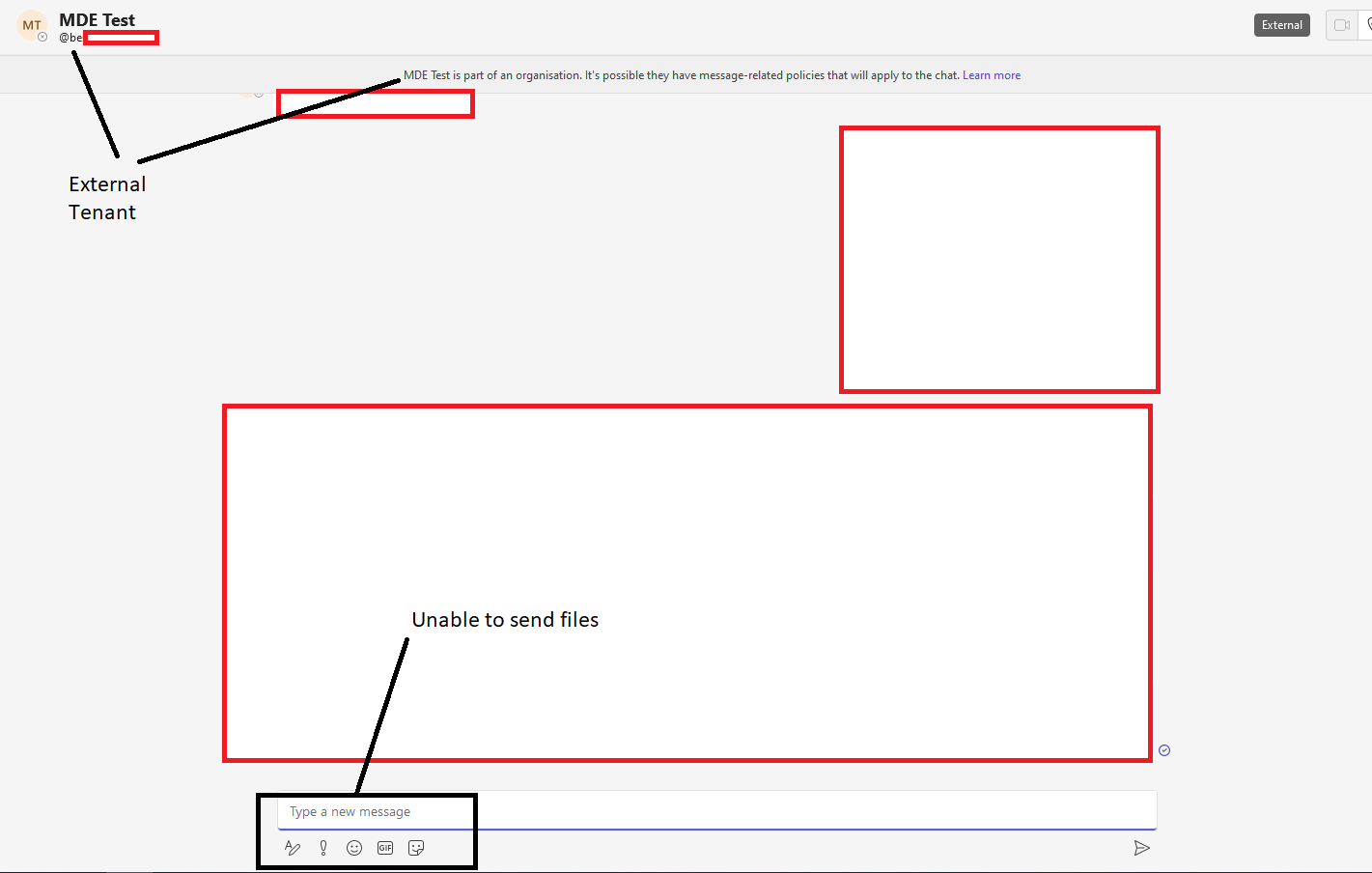 Client restrictions preventing external users from sending a file (Jumpsec)
Client restrictions preventing external users from sending a file (Jumpsec)
Although Microsoft Teams has client-side protections in place to block file delivery from external tenants, the researchers found a way to circumvent these restrictions by manipulating the internal and external recipient IDs in a POST request, tricking the system into treating an external user as an internal one.
By employing this technique, the payload is hosted on a Sharepoint domain, but it appears in the target’s inbox as a file rather than a link. The researchers successfully tested this attack in a covert red team engagement, highlighting its ability to bypass existing security measures and anti-phishing training.
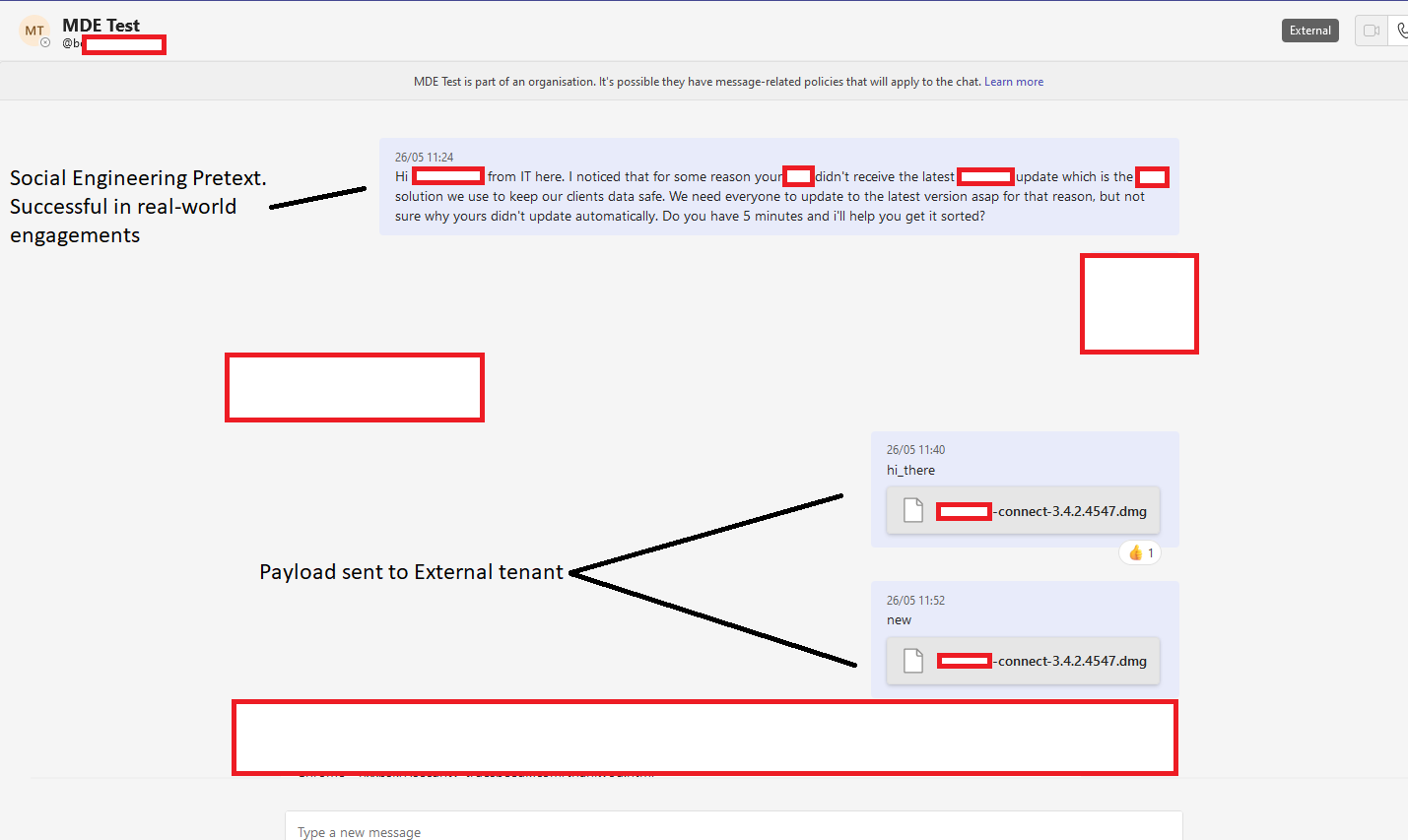 Attack example with the sender posing as a member of the IT team (Jumpsec)
Attack example with the sender posing as a member of the IT team (Jumpsec)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Furthermore, if an attacker registers a domain similar to the target organization’s on Microsoft 365, the messages can be made to appear as if they come from an internal source, increasing the likelihood of the target downloading the file.
The researchers promptly reported their findings to Microsoft, but the company responded that the issue does not meet the bar for immediate servicing, indicating that it does not consider it a high-priority vulnerability.
Trending: Offensive Security Tool: PhoneSploit Pro
Organizations using Microsoft Teams and not requiring regular communication with external tenants are advised to disable this feature from the Microsoft Teams Admin Center. If external communication channels need to be maintained, organizations can define specific domains in an allow-list to mitigate the risk of exploitation.
Additionally, the researchers have requested Microsoft to add external tenant-related events to the software’s logging, which could help prevent such attacks in real-time. Users can support this request to urge Microsoft to take action on the vulnerability.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












