Mass Exploitation of Ivanti’s Newest Zero-Day Vulnerability Threatens Thousands of Devices

A critical vulnerability in Ivanti Connect Secure and Ivanti Policy Secure servers, known as CVE-2024-21893, has triggered a wave of mass exploitation by multiple attackers, posing a significant threat to affected devices. Initially flagged by Ivanti on January 31, 2024, the flaw gained zero-day status due to limited active exploitation, impacting a small subset of customers.
Exploiting CVE-2024-21893 enables attackers to circumvent authentication measures, granting unauthorized access to restricted resources on vulnerable devices running versions 9.x and 22.x.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
The threat monitoring service Shadowserver has reported a surge in attack activity, with 170 distinct IP addresses attempting to exploit the SSRF bug.
We observed CVE-2024-21893 exploitation using '/dana-na/auth/saml-logout.cgi' on Feb 2nd hours before @Rapid7 posting & unsurprisingly lots to '/dana-ws/saml20.ws' after publication. This includes reverse shell attempts & other checks. To date, over 170 attacking IPs involved https://t.co/yUy4y2xCCz
— Shadowserver (@Shadowserver) February 4, 2024
Notably, the exploitation volume of this vulnerability surpasses that of recent Ivanti flaws, indicating a notable shift in attackers’ strategies.
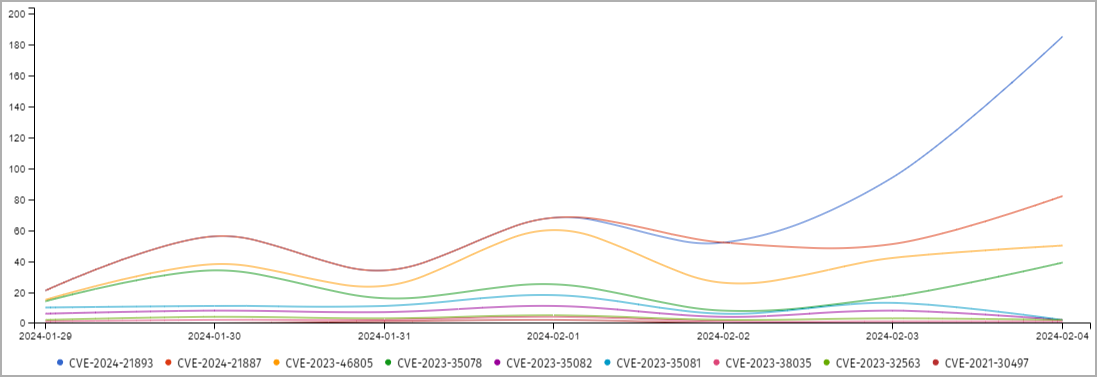 Exploitation volume for latest Ivanti flaws (Shadowserver)
Exploitation volume for latest Ivanti flaws (Shadowserver)
Although a proof-of-concept (PoC) exploit was released by Rapid7 researchers on February 2, 2024, attackers had already devised similar methods prior to the report’s publication.
Presently, nearly 22,500 Ivanti Connect Secure devices are exposed on the Internet, with the actual number vulnerable to CVE-2024-21893 remaining unclear. In conjunction with the disclosure of this vulnerability, Ivanti released security updates addressing two additional zero-days (CVE-2023-46805 and CVE-2024-21887) detected on January 10, 2024.
Trending: Recon Tool: go-dork


