Massive DDoS Attacks Exploiting HTTP/2 Rapid Reset Zero-Day Vulnerability

In a collaborative effort to tackle record-breaking distributed denial-of-service (DDoS) attacks employing an innovative technique known as HTTP/2 Rapid Reset, tech giants Amazon Web Services (AWS), Cloudflare, and Google have taken swift action. These layer 7 attacks, which were initially detected in late August 2023, exploited a susceptibility tracked under CVE-2023-44487, with a CVSS score of 7.5 out of 10.
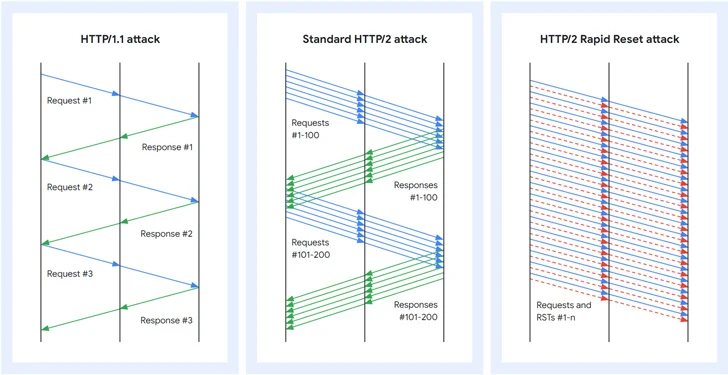
The essence of these attacks revolves around a zero-day flaw found in the HTTP/2 protocol, a fundamental component of modern web communications. Notably, HTTP/2 enhances efficiency through the multiplexing of requests over a single TCP connection, resulting in concurrent streams.
However, the Rapid Reset attack capitalizes on a specific feature of HTTP/2. In the event a client wants to abort a request, it can issue an RST_STREAM frame to terminate the data exchange. Threat actors leverage this method to send and cancel requests in rapid succession. This ingeniously sidesteps the server’s concurrent stream limit, effectively overwhelming the target without reaching its configured threshold.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Mark Ryland and Tom Scholl at AWS clarify this technique: “HTTP/2 rapid reset attacks consist of multiple HTTP/2 connections with requests and resets in rapid succession. For example, a series of requests for multiple streams will be transmitted followed up by a reset for each of those requests. The targeted system will parse and act upon each request, generating logs for a request that is then reset, or canceled, by a client.”
What’s most concerning is the ability to reset streams instantly, essentially enabling each connection to accommodate an indefinite number of requests in flight. This loophole allows threat actors to unleash a barrage of HTTP/2 requests that can overwhelm a website’s capacity to respond to new incoming requests, effectively causing it to go offline.
Crucially, such attacks can be executed with a relatively small botnet, consisting of as few as 20,000 machines, as observed by Cloudflare.
Grant Bourzikas, Chief Security Officer at Cloudflare, points out the magnitude of this vulnerability: “This zero-day provided threat actors with a critical new tool in their Swiss Army knife of vulnerabilities to exploit and attack their victims at a magnitude that has never been seen before.”
Trending: Offensive Security Tool: Noir
HTTP/2 is widely adopted, used by 35.6% of all websites according to W3Techs, and 77% of requests use HTTP/2 as per data from Web Almanac.
Google Cloud has reported encountering multiple variants of the Rapid Reset attacks, some not as effective as the initial version but more efficient than standard HTTP/2 DDoS attacks. F5, in an independent advisory, recommends limiting the number of concurrent streams and persisting HTTP connections as protective measures.
Organizations are urged to proactively address this vulnerability, as Bourzikas emphasizes, “After today, threat actors will be largely aware of the HTTP/2 vulnerability; and it will inevitably become trivial to exploit and kick off the race between defenders and attacks — first to patch vs. first to exploit. Organizations should assume that systems will be tested and take proactive measures to ensure protection.”
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












