Massive GitHub Phishing Attack Targets 12,000 Repositories with Fake Security Alerts

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
GitHub’s Response and Ongoing Attack
The phishing campaign was first reported by cybersecurity researcher Luc4m. Since its detection, GitHub has been actively working to remove fraudulent issues, but the attack is still ongoing. The number of affected repositories fluctuates as GitHub takes action.
Trending: Major Cyber Attacks that shaped 2024
How to Protect Your GitHub Account
If you mistakenly granted access to the malicious OAuth app, take the following steps immediately:
Revoke the OAuth app’s access
- Go to GitHub Settings > Applications
- Look for any unfamiliar or suspicious OAuth apps (e.g., “gitsecurityapp”) and revoke their access
Review your GitHub Actions & Private Gists
- Check for unauthorized workflows in GitHub Actions
- Look for unexpected private gists that may contain stolen data
Rotate Your Credentials
- Reset your GitHub password
- Revoke and regenerate all authorization tokens
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com


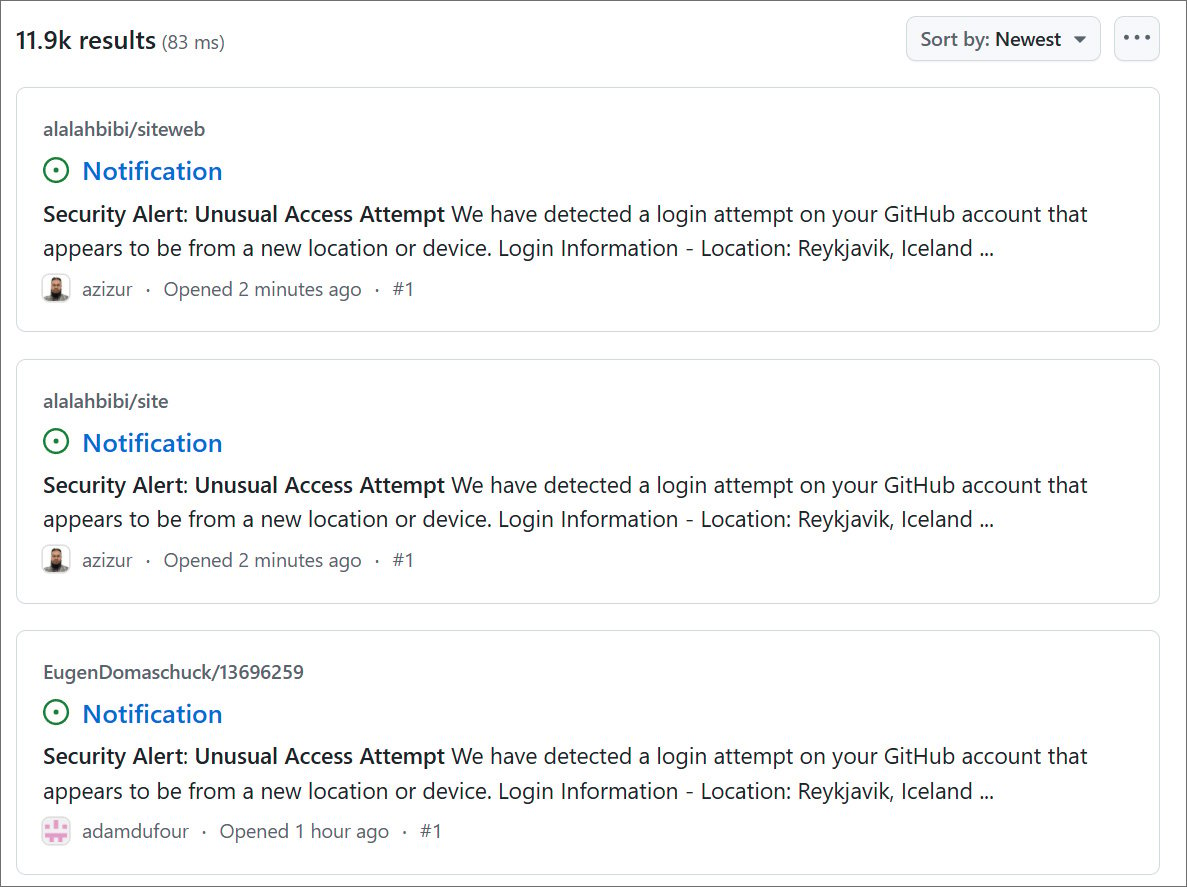 Fake security alert issues created in GitHub repositories
Fake security alert issues created in GitHub repositories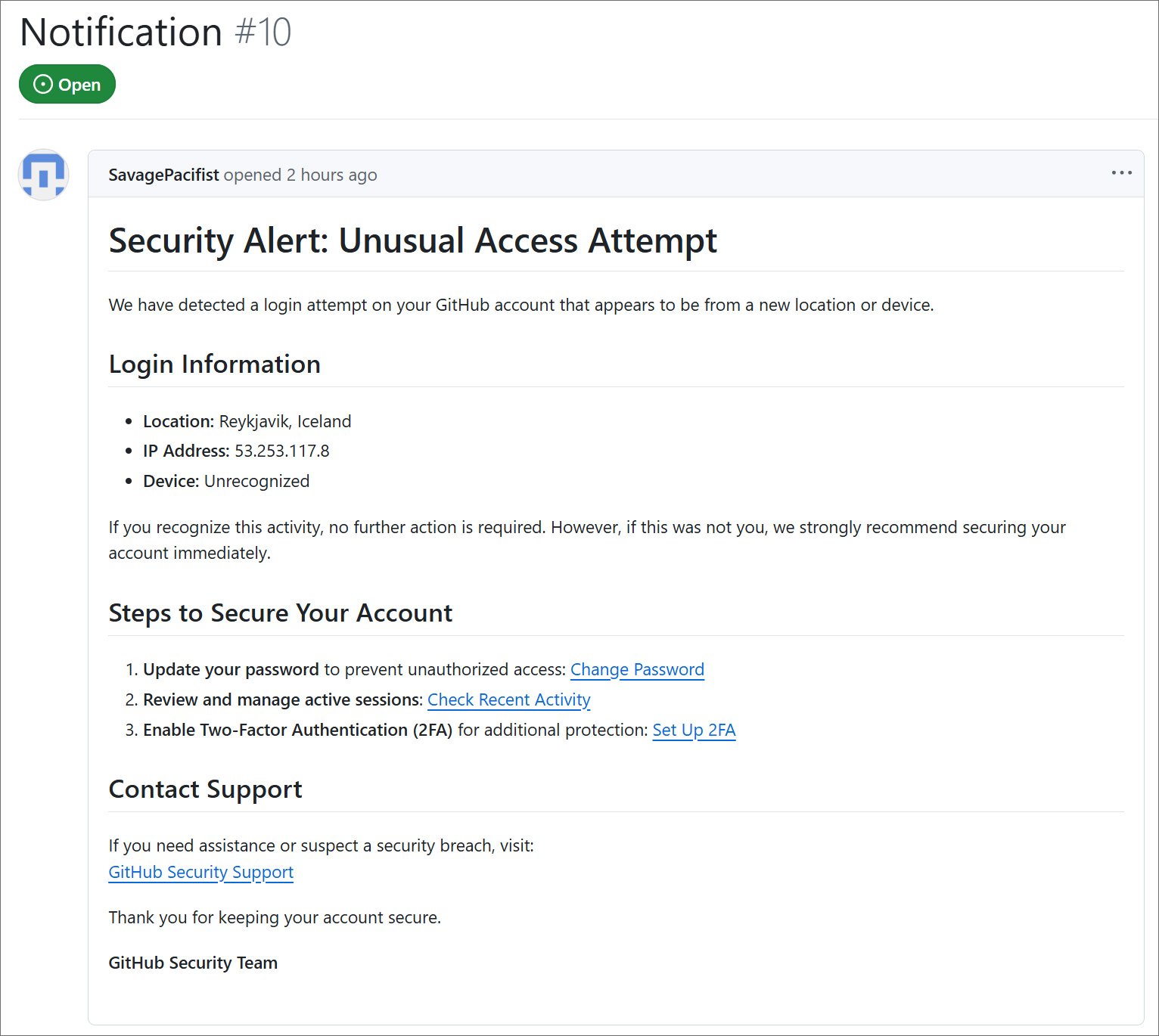 Fake “Security Alert” issue posted to GitHub repositories
Fake “Security Alert” issue posted to GitHub repositories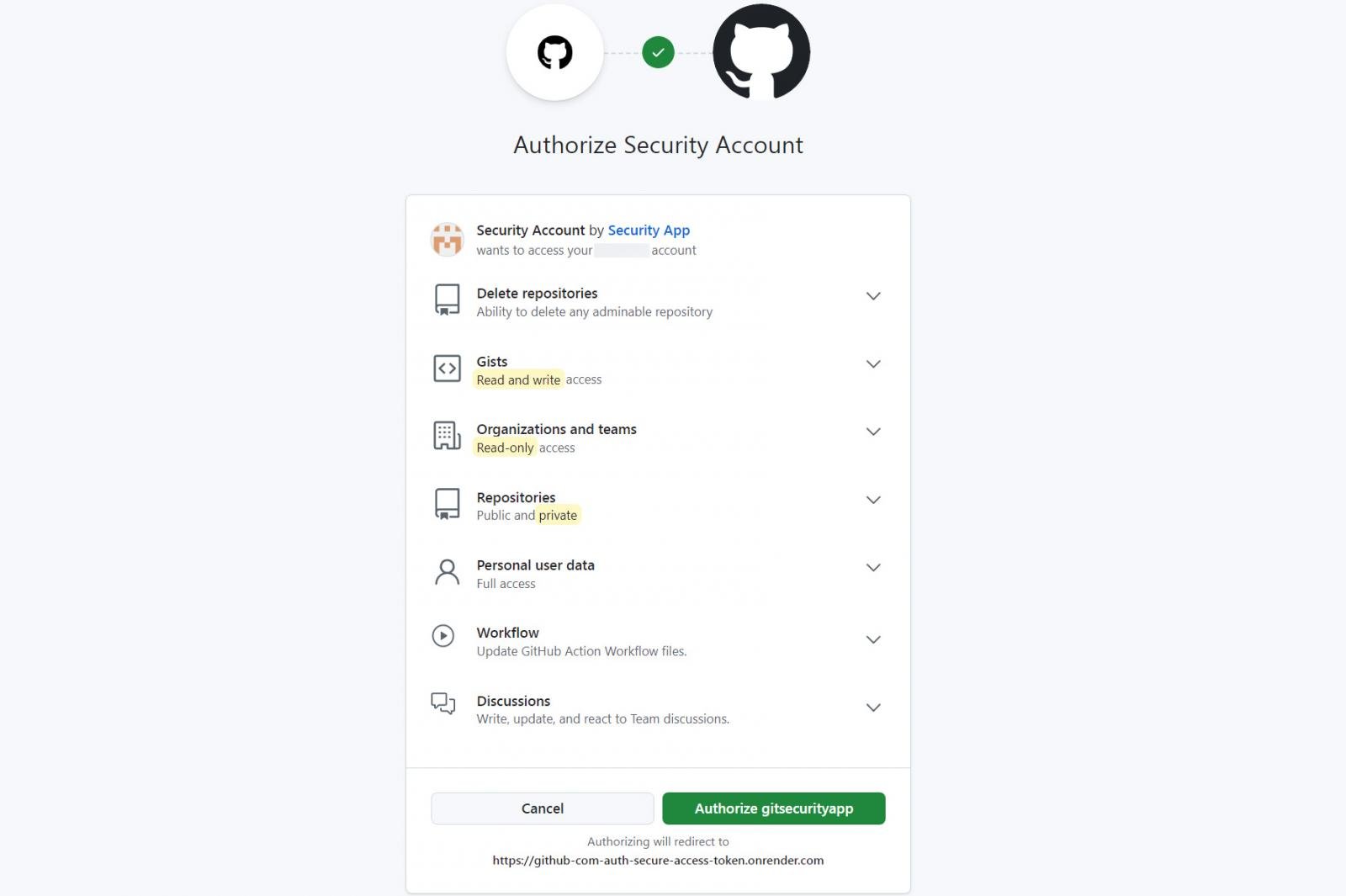 Permissions requested by malicious OAuth app
Permissions requested by malicious OAuth app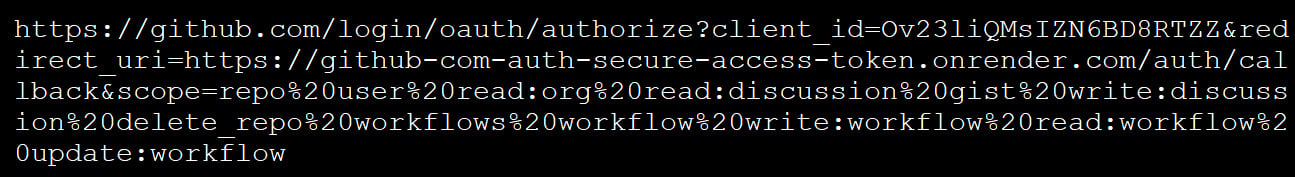 OAuth authorization link with a callback to an onrender.com page
OAuth authorization link with a callback to an onrender.com page










