Meet BunnyLoader: The Rapidly Evolving Malware-as-a-Service

In a digital landscape where cyber threats evolve at an alarming pace, security researchers have unveiled a new malware-as-a-service (MaaS) dubbed ‘BunnyLoader.’ This insidious malware has been making waves across the dark corners of the internet, enticing cybercriminals with its fileless loader capabilities and a host of malicious functions, including clipboard theft.
BunnyLoader, a constantly evolving threat, is rapidly gaining notoriety among malicious actors. Since its initial appearance on September 4, this malicious software has seen multiple updates, each introducing new features and addressing bugs. Presently, BunnyLoader can perform a slew of malicious activities, from downloading and executing payloads to keylogging, data theft (including sensitive information and cryptocurrencies), and remote command execution.
Researchers from cloud security company Zscaler have been closely monitoring BunnyLoader’s ascent in the cyber underworld. They note that this malware is becoming increasingly popular among cybercriminals due to its robust feature set, all available at a surprisingly low cost.
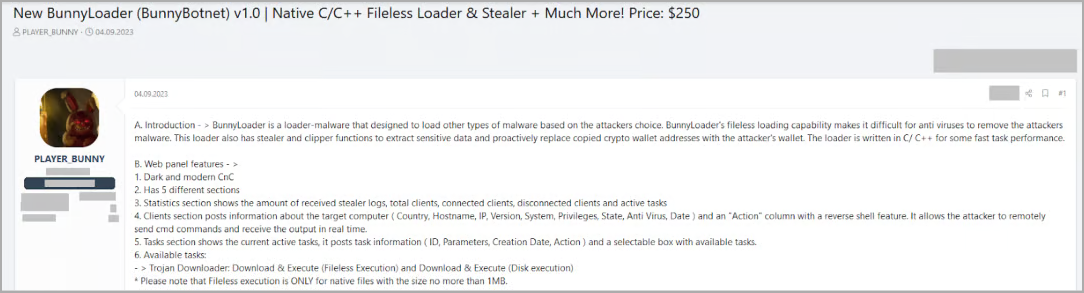 BunnyLoader promoted on hacker forum (Zscaler)
BunnyLoader promoted on hacker forum (Zscaler)
Offensive Security, Bug Bounty Courses
BunnyLoader Overview
BunnyLoader’s command and control panel empower even the most amateur cybercriminals to deploy second-stage payloads, engage in keylogging, steal credentials, manipulate clipboards for cryptocurrency theft, and execute remote commands on compromised devices.
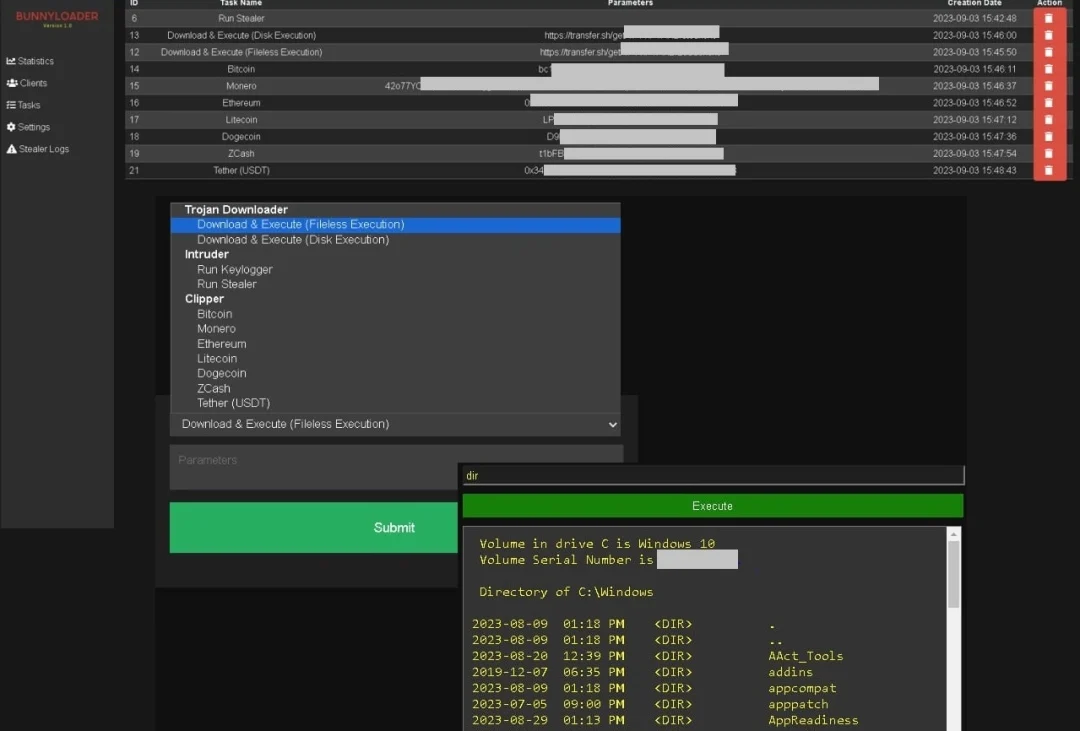 Main malware functions directly available through the panel (Zscaler)
Main malware functions directly available through the panel (Zscaler)
Recent research reveals that, upon execution on a compromised system, BunnyLoader establishes persistence by creating a new value in the Windows Registry. It then operates discreetly, conceals its presence, sets a mutex to prevent multiple instances, and registers the victim within the control panel.
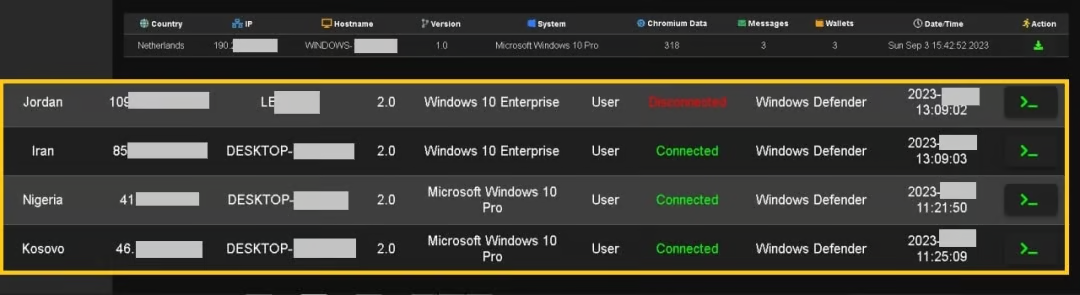 Victims listed on the panel (Zscaler)
Victims listed on the panel (Zscaler)
This malware conducts various checks to ascertain whether it’s running in a controlled environment, promptly issuing a fabricated architecture incompatibility error if it detects one.
In addition to its primary functionalities, BunnyLoader boasts modules designed to pilfer data stored in web browsers (including passwords, credit card details, and browsing history), cryptocurrency wallets, VPNs, and messaging applications. In essence, it operates as a comprehensive information-stealing tool.
All ill-gotten data is meticulously compressed into ZIP archives before being transmitted to the threat actor’s command and control (C2) server.
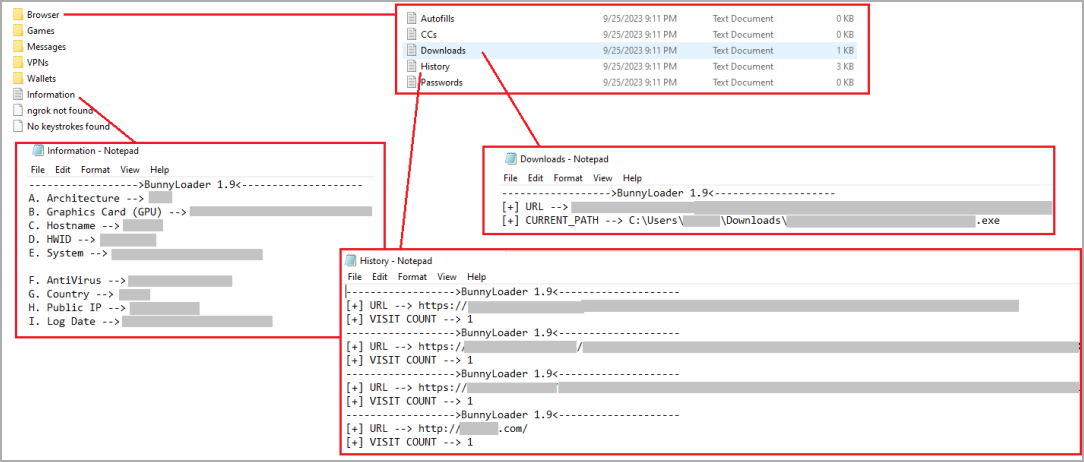 Data exfiltrated by BunnyLoader (Zscaler)
Data exfiltrated by BunnyLoader (Zscaler)
Remarkably, BunnyLoader supports the deployment of payloads either to the disk or as memory-resident (fileless) executions, utilizing the process hollowing technique.
Rapid Development
Zscaler’s continuous monitoring of BunnyLoader’s development on various hacking forums reveals a rapid succession of updates and improvements since its inception. Here’s a snapshot of BunnyLoader’s developmental journey:
- v1.0 (Sept 4): Initial release.
- v1.1 (Sept 5): Bug fixes, log compression, and introduction of the ‘pwd’ command.
- v1.2 (Sept 6): Browser history recovery, NGRok auth-token recovery, and support for additional Chromium browser paths.
- v1.3 (Sept 9): Credit card recovery and C2 bug fixes.
- v1.4 (Sept 10): Implementation of AV evasion.
- v1.5 (Sept 11): VPN recovery, fileless loader fixes, and log loading optimizations.
- v1.6 (Sept 12): Downloads history viewer and anti-sandbox techniques.
- v1.7 (Sept 15): Enhanced AV evasion.
- v1.8 (Sept 15): Keylogger functionality and bug resolutions.
- v1.9 (Sept 17): Game recovery, expanded browser paths, and desktop wallet recovery.
- v2.0 (Sept 27): Extensive updates, GUI enhancements, critical bug fixes, and exploit attempt detection.
Presently, BunnyLoader is available for purchase at $250. For those seeking even more advanced features such as stronger anti-analysis measures, in-memory injection, AV evasion, and additional persistence mechanisms, the “private stub” version is available for $350.
This combination of affordability and rapid development cycles makes BunnyLoader an attractive option for cybercriminals seeking early access to emerging malware projects, all before they gain prominence and potentially escalate their costs.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












