Meet ‘Legion’: The New Python-Based Credential Harvester and SMTP Hijacking Tool

A new tool called ‘Legion’ has emerged in the world of cybercrime, offering a range of modules for credential harvesting and SMTP hijacking. Cybercriminals operating under the “Forza Tools” name sell this Python-based tool on Telegram, attracting over a thousand members on their channel.
 Forza Tools tutorials on YouTube (Cado)
Forza Tools tutorials on YouTube (Cado)
Harvesting credentials
Legion is modular malware likely based on AndroxGhOst, allowing cybercriminals to perform SMTP server enumeration, exploit vulnerable Apache versions, brute-force cPanel and WebHost Manager accounts, interact with Shodan’s API, and abuse AWS services. This tool targets many online services, including Twilio, Nexmo, Stripe/Paypal, AWS console credentials, AWS SNS, S3 and SES specific, Mailgun, and database/CMS platforms. Additionally, Legion can create administrator users, implant webshells, and send out spam SMS to customers of U.S. carriers.
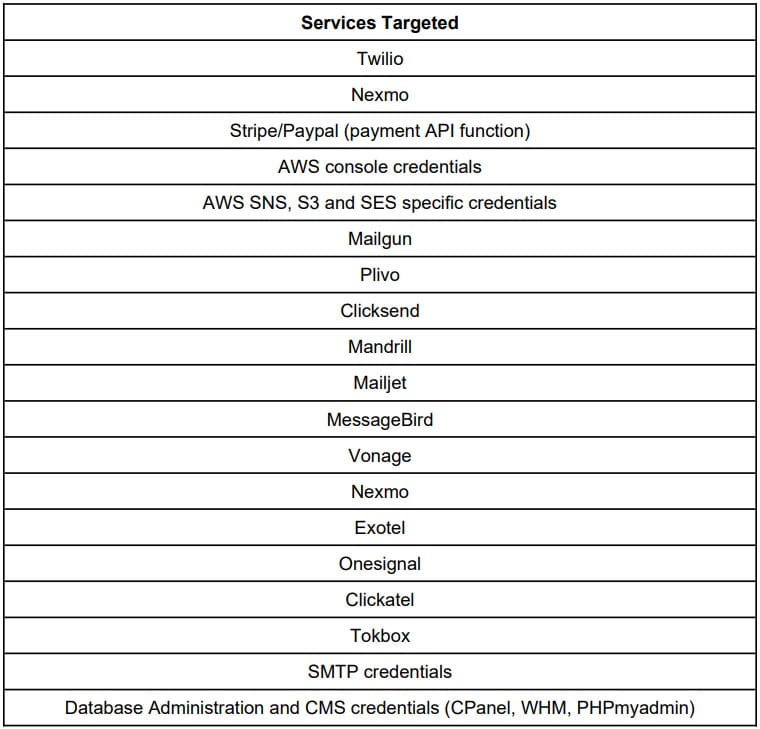
All services targeted by Legion (Cado)
Legion mainly targets unsecured web servers running content management systems and PHP-based frameworks like Laravel, using RegEx patterns to search for files commonly known to hold secrets, authentication tokens, and API keys. Cybercriminals use an array of methods to retrieve credentials, such as targeting environment variable files (.env) and configuration files containing SMTP, AWS console, Mailgun, Twilio, and Nexmo credentials.
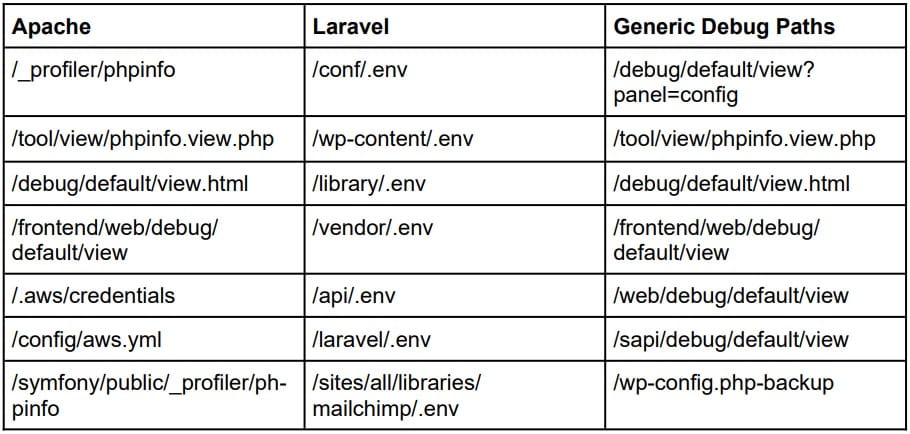 Paths parsed by Legion for stored secrets (Cado)
Paths parsed by Legion for stored secrets (Cado)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
How Legion Extracts Credentials and Performs Spam and Phishing Attacks
Furthermore, Legion includes brute-forcing systems for AWS and SendGrid credentials, although Cado indicates that the former’s system is unlikely to generate usable credentials in its current state. Once Legion captures valid AWS credentials, it attempts to create an IAM user named ‘ses_legion’ with administrator rights, granting full access to all AWS services and resources.
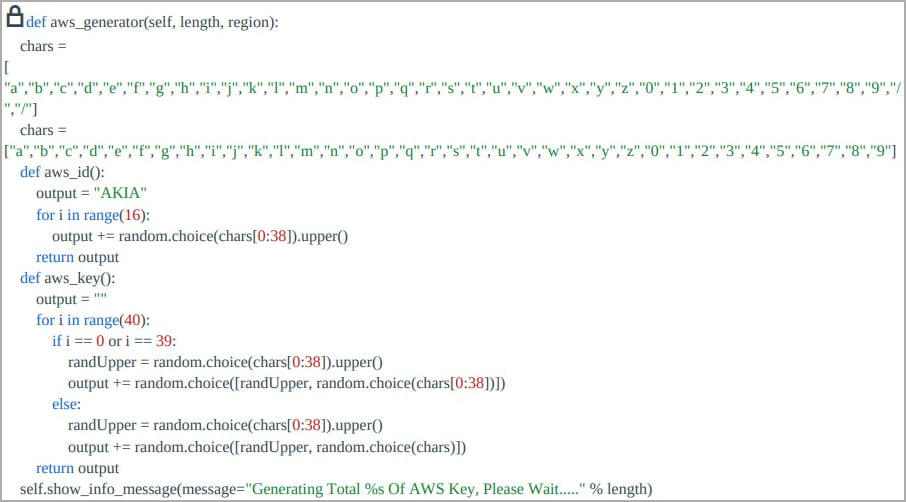 Code to brute-force AWS credentials (Cado)
Code to brute-force AWS credentials (Cado)
In addition to stealing credentials, Legion can send out spam or phishing emails by gaining access to email services. It can also send SMS spam by leveraging stolen SMTP credentials after generating a list of phone numbers with area codes retrieved from online services. The carriers supported by the malware include AT&T, Sprint, US Cellular, T-Mobile, Cricket, Verizon, Virgin, SunCom, Alltel, Cingular, and VoiceStream.
Lastly, Legion can exploit known PHP vulnerabilities to register a webshell on the targeted endpoint or perform remote code execution to give the attacker full access to the server.
Trending: Offensive Security Tool: Mythic
AWS users – signs of compromise
As an all-purpose credential harvester and hacking tool, Legion increases the risk for poorly managed and misconfigured web servers. AWS users should look for signs of compromise, such as changing the IAM user registration code to include an “Owner” tag with the value “ms.boharas.” The emergence of Legion underscores the importance of strengthening online security measures to prevent cyberattacks.
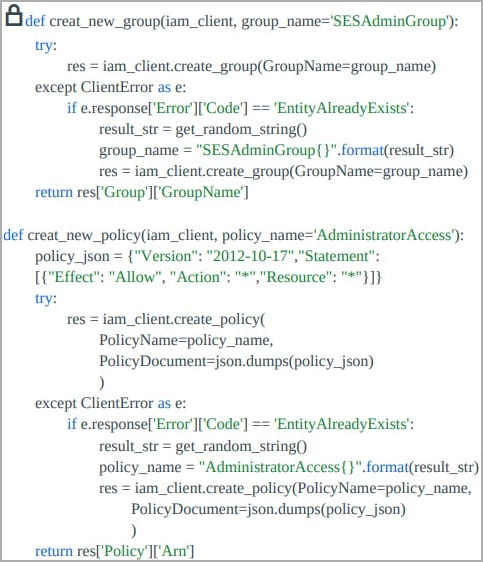 IAM policy creation (Cado)
IAM policy creation (Cado)
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












