Meet Rorschach: The Fastest Ransomware Strain Yet Discovered

Check Point researchers have identified a new ransomware strain, which they have named Rorschach, that they say comes with technically unique features. The malware was discovered following a cyberattack on a US-based company, and researchers found that Rorschach would be the fastest ransomware threat on the market based on their tests.
Rorschach details
Rorschach’s encryption process, which includes the curve25519 and eSTREAM cipher hc-128 algorithms, is intermittent, meaning that it encrypts files only partially, leading to increased processing speed. In addition, the ransomware’s encryption routine indicates “a highly effective implementation of thread scheduling via I/O completion ports.”
Rorschach was deployed on the victim network using the DLL side-loading technique via a signed component in Cortex XDR, the extended detection and response product from Palo Alto Networks. The malware then used the Cortex XDR Dump Service Tool to sideload the Rorschach loader and injector. The loader file features UPX-style anti-analysis protection, while the main payload is protected against reverse engineering and detection by virtualizing parts of the code using VMProtect software.
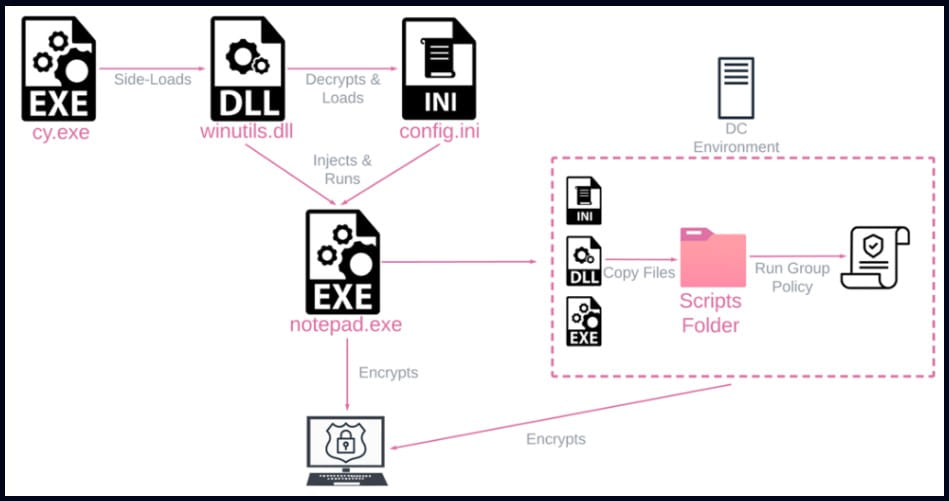 Attack chain (Check Point)
Attack chain (Check Point)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Rorschach’s Advanced Propagation and Record-Wiping Abilities Revealed
Check Point reports that Rorschach creates a Group Policy when executed on a Windows Domain Controller to propagate to other hosts on the domain. After compromising a machine, the malware erases four event logs to wipe its trace. While it comes with hardcoded configuration, Rorschach supports command-line arguments that expand functionality. The options are hidden and can’t be accessed without reverse engineering the malware.
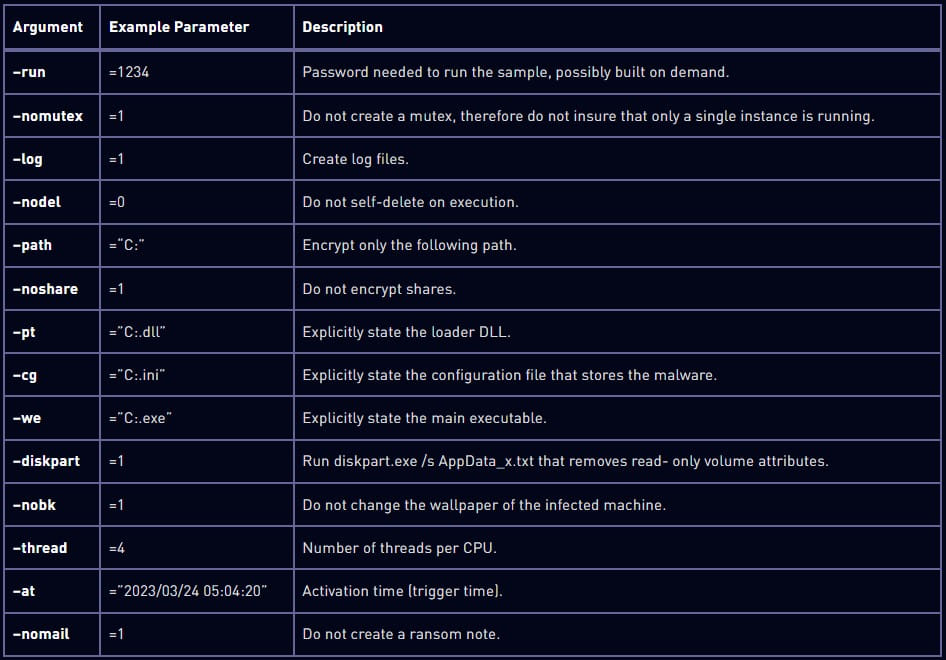 Arguments decoded by Check Point
Arguments decoded by Check Point
Trending: Offensive Security Tool: Nginxpwner
Rorschach’s encryption process
During testing, Check Point set up a test with 220,000 files on a 6-core CPU machine and found that it took Rorschach 4.5 minutes to encrypt the data, whereas LockBit v3.0, considered the fastest ransomware strain, finished in 7 minutes.
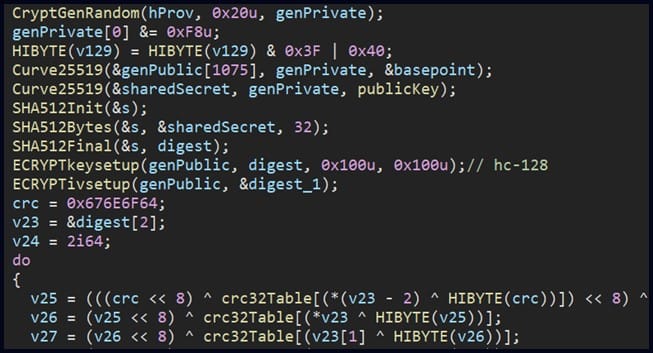 Rorschach encryption scheme (Check Point)
Rorschach encryption scheme (Check Point)
After locking the system, Rorschach drops a ransom note similar to the format used by the Yanlowang ransomware. According to the researchers, a previous version of malware used a ransom note similar to what DarkSide used. Check Point assesses that Rorschach has implemented the better features from some of the leading ransomware strains leaked online, including Babuk, LockBit v2.0, and DarkSide. The malware “raises the bar for ransom attacks” and comes with self-propagating capabilities.
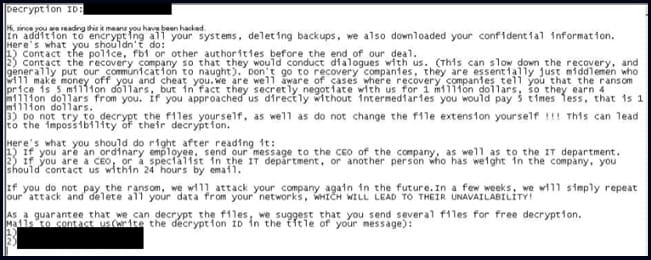 Latest ransom note dropped by Rorschach (Check Point)
Latest ransom note dropped by Rorschach (Check Point)
At present, the operators of the Rorschach ransomware remain unknown, and there is no branding, something that is rarely seen in the ransomware scene.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












