MetaStealer: New macOS Malware Targeting Intel-Based Computers Emerges

A new information-stealing malware called ‘MetaStealer’ has recently emerged in the wild, posing a significant threat to Intel-based macOS computers by stealing a wide range of sensitive information. This malware, distinct from the ‘META’ info-stealer that gained notoriety last year, is written in Go and has the capability to bypass Apple’s built-in antivirus technology, XProtect, primarily targeting business users.
The cybersecurity firm SentinelOne has been actively monitoring MetaStealer for the past few months and has noticed an unusual level of social engineering involved in its distribution.
While MetaStealer shares some similarities with Atomic Stealer, another Go-based macOS info-stealer, the extent of code overlap is limited, and the delivery methods differ significantly. Therefore, SentinelOne has concluded that MetaStealer is an entirely separate operation.
How MetaStealer Arrives on macOS Systems
SentinelOne identified a malware sample on VirusTotal accompanied by a comment indicating that MetaStealer threat actors are engaging with businesses, often impersonating the company’s clients to distribute the malware.
One comment on VirusTotal reads, “I was targeted by someone posing as a design client, and didn’t realize anything was out of the ordinary. The man I’d been negotiating with on the job this past week sent me a password-protected zip file containing this DMG file, which I thought was a bit odd. Against my better judgment, I mounted the image to my computer to see its contents. It contained an app that was disguised as a PDF, which I did not open, and that’s when I realized he was a scammer.”
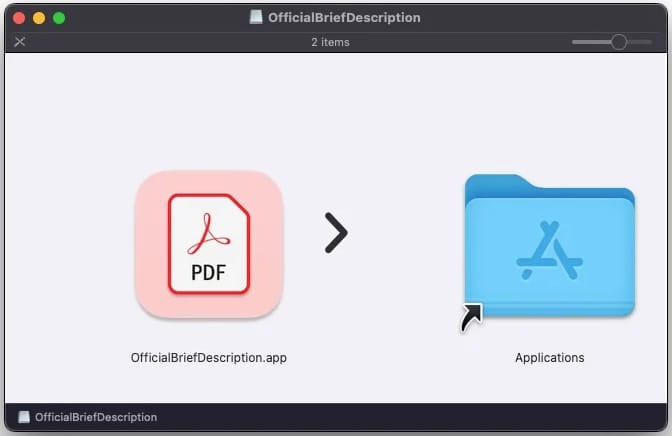
These phishing emails include disk image files that, when mounted on the filesystem, contain executables with deceptive names, made to appear as PDF files, with the aim of tricking the victim into opening them.
 Disk image file (SentinelOne)
Disk image file (SentinelOne)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The DMG files have deceptive names, often related to Adobe software or client work, further increasing the chances of users falling for the scam. Examples include filenames like “AdobeOfficialBriefDescription.dmg” or “Adobe Photoshop 2023 (with AI) installer.dmg.”
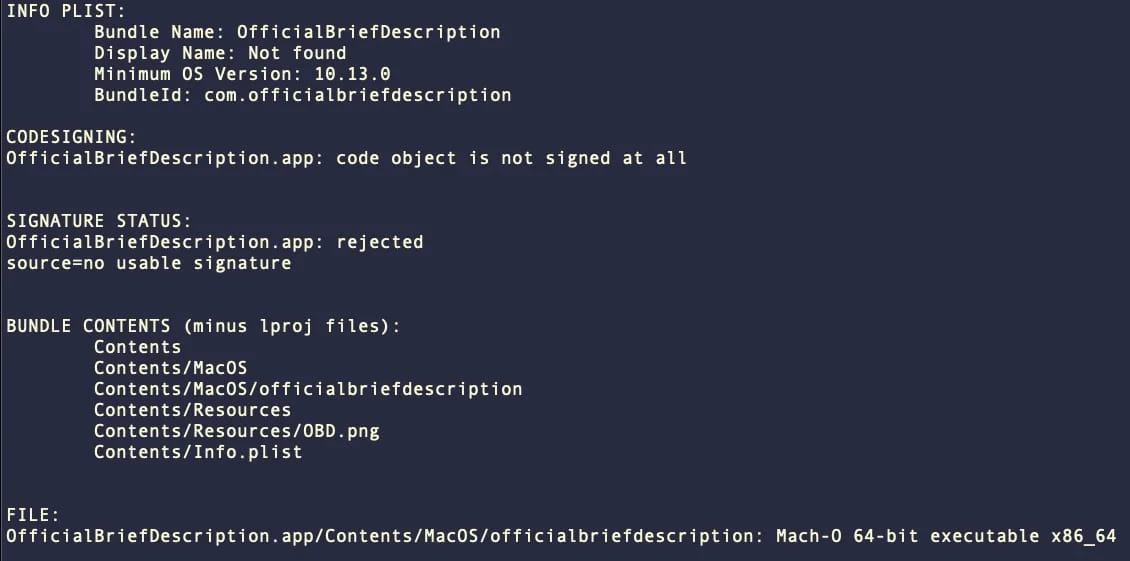 Bundle contents (SentinelOne)
Bundle contents (SentinelOne)
MetaStealer’s Capabilities
MetaStealer is designed to steal information stored on compromised systems, encompassing passwords, files, and application data. It then attempts to exfiltrate this stolen data via TCP over port 3000.
Notably, the malware is equipped to exfiltrate the keychain, a system-level password management system for macOS. The keychain stores credentials for websites, applications, WiFi networks, certificates, encryption keys, credit card information, and private notes. The theft of keychain contents is a powerful feature that could grant attackers access to a wealth of sensitive data.
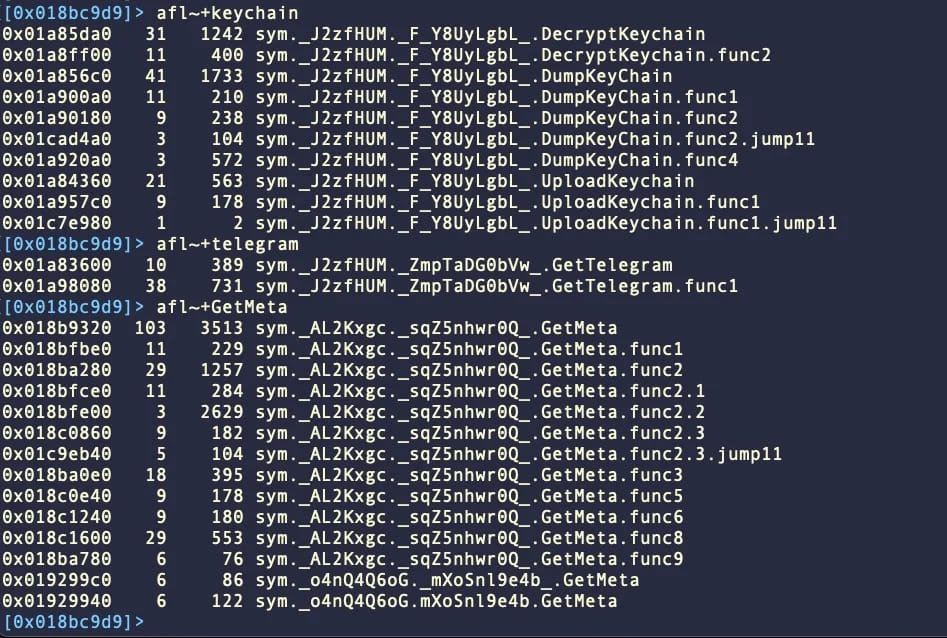 Targeting keychain, Telegram, and Meta services (SentinelOne)
Targeting keychain, Telegram, and Meta services (SentinelOne)
Trending: OSINT Tool: Photon
In its current version, MetaStealer exclusively runs on Intel x86_64 architecture, limiting its reach to macOS systems using Apple Silicon processors (M1, M2) unless the victim uses Rosetta to run the malware.
While this limitation reduces the potential pool of victims, it’s essential to remain vigilant, as attackers might develop a new version of MetaStealer with native support for Apple Silicon, making it a more widespread threat.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












