MGM Resorts Hit by BlackCat Ransomware Affiliate: Data Stolen, Operations Halted

An affiliate associated with the BlackCat ransomware group, also known as APLHV, is responsible for the cyberattack that disrupted the operations of MGM Resorts, compelling the company to shut down its IT systems.
In an official statement, the BlackCat ransomware group asserted that they had infiltrated MGM’s infrastructure since Friday and subsequently encrypted more than 100 ESXi hypervisors after MGM took its internal infrastructure offline.
The group claims to have exfiltrated data from MGM’s network and asserts continued access to some of the company’s infrastructure. They have threatened to launch further attacks unless an agreement to pay a ransom is reached.
Reports first emerged that the ALPHV ransomware operation, associated with the BlackCat group, had breached MGM through a social engineering attack. While these reports could not be independently verified, an administrator from BlackCat confirmed to BleepingComputer that one of their affiliates was indeed responsible for the MGM attack. They clarified that this actor was not the same one responsible for hacking Western Digital in March.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
This threat actor, known as Scattered Spider by cybersecurity companies such as Crowdstrike, 0ktapus by Group-IB, UNC3944 by Mandiant, and Scatter Swine by Okta, is reported to have breached the networks of other organizations, including Caesars Entertainment. Caesars Entertainment, in a recent filing with the U.S. Securities and Exchange Commission, hinted at paying a $30 million ransom to avoid the leakage of customer data stolen in the attack.
BlackCat claims that MGM Resorts has remained unresponsive through the provided communication channel, suggesting that the company is not willing to engage in ransom negotiations. The threat actors revealed that MGM disconnected all of its Okta Sync servers after learning of their presence on Okta Agent servers.
However, even after this action, the hackers maintained their presence on MGM’s network. They claim to still possess super administrator privileges in MGM’s Okta environment and Global Administrator permissions for the company’s Azure tenant.
With no response from MGM and after waiting a day, the attackers initiated the ransomware attack by targeting over 100 ESXi hypervisors on September 11th. The threat actors asserted that they do not currently know the extent of the data they have stolen from MGM but warned that they would extract pertinent information and release it unless an agreement is reached.
To exert further pressure on the company, BlackCat threatened to leverage their existing access to MGM’s infrastructure for additional attacks. BleepingComputer has not independently verified BlackCat’s claims, and MGM Resorts has not responded to inquiries.
Trending: OSINT Tool: Photon
Scattered Spider
Scattered Spider is known for employing various social engineering tactics to breach corporate networks, including impersonating help desk personnel, SIM swap attacks, and phishing campaigns targeting multi-factor authentication codes. Researchers believe this group comprises English-speaking individuals, primarily teenagers and young adults aged 16 to 22. They are also thought to overlap with the Lapsus$ hacking group due to similar tactics.
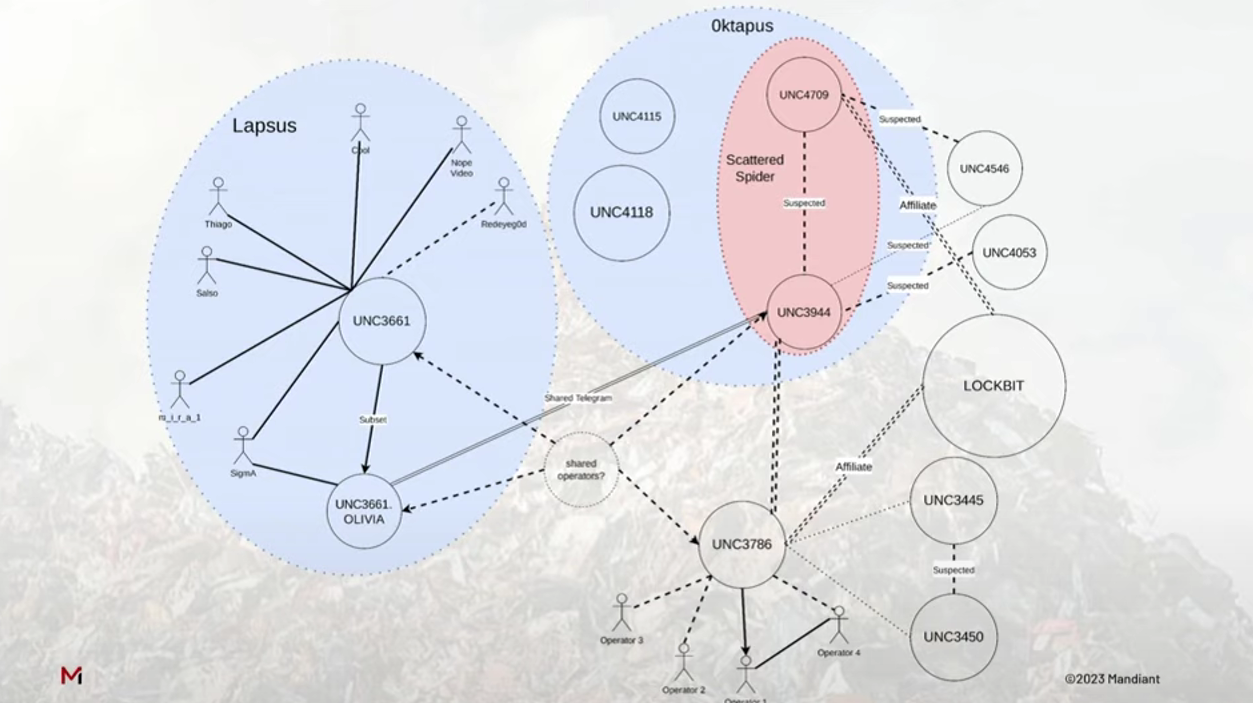 Link between Lapsus$ and UNC3944
Link between Lapsus$ and UNC3944
source: Mandiant
Scattered Spider’s campaign, ‘0ktapus,’ targeted over 130 organizations to steal Okta identity credentials and 2FA codes. Some of their targets included major companies and platforms like T-Mobile, MetroPCS, Verizon Wireless, AT&T, Slack, Twitter, Binance, KuCoin, CoinBase, Microsoft, Epic Games, Riot Games, Evernote, AT&T, HubSpot, TTEC, and Best Buy.
While their ransomware activities are relatively recent, most of their attacks have involved extortion, with demands reaching millions of dollars in exchange for not leaking data or providing an encryption solution.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












