Microsoft, Adobe Exploits Top List of Crooks’ Wish List

Reading Time: 2 Minutes
A year-long study into the underground market for exploits in cybercriminal forums shows that crooks are salivating for Microsoft bugs, which are far and away the most requested and most sold exploits.
According to researchers (see chart below) Microsoft products made up a whopping 47 percent of the requests, compared with, say, internet of things (IoT) exploits, which only accounted for 5 percent.
The exploit market is accommodating cybercrooks’ hunger for puncturing Microsoft products, according to Trend Micro. A second data point (see chart below) shows that 61 percent of sold exploits targeted Microsoft products, including Office, Windows, Internet Explorer and Microsoft Remote Desktop Protocol (RDP).
No surprise there. Flashpoint researchers also reported in December, prices for RDP server access has been surging.
The research was presented on Monday at the all-virtual RSA Conference 2021, by Trend Micro Senior Researcher Mayra Rosario Fuentes. In her session, titled Tales from the Underground: The Vulnerability Weaponization Lifecycle, Fuentes said that the study tracked the exploits that were sold and requested on more than 600 underground forums over a year.
What gets sold on the exploits market. Source: Trend Micro
Researchers found that the average price for exploits that threat actors were willing to pay was $2,000. The crooks are going after fresh, tender new vulnerabilities, with 52 percent of exploits on their wish list being less than 2 years old: an age bracket that also accounts for 54 percent of exploits being sold.
Most-requested exploits. Source: Trend Micro
See Also: Bizarro Banking Trojan Sports Sophisticated Backdoor
Oldies But Goodies Are Still Hot-Hot-Hot
Older vulnerabilities are still in demand, though: 22 percent of the exploits sold in the underground were 3+ years old, according to Fuentes. The oldest vulnerability was downright arthritic, dating back to 1999.
Of the “outdated” exploits being sold, 45 percent were Microsoft-flavored, with the second crook crowd-pleaser being Adobe exploits. Fuentes pointed out that the average time to patch an internet-facing system is 71 days: a whole lot of time for attackers to do some damage.
Outdated exploits being sold on underground forums. Source: Trend Micro
You can see one example of an exploit request below, where the potential purchaser was looking for an exploit of CVE-2019-1151 – a remote code execution (RCE) of a Microsoft Graphics vulnerability.
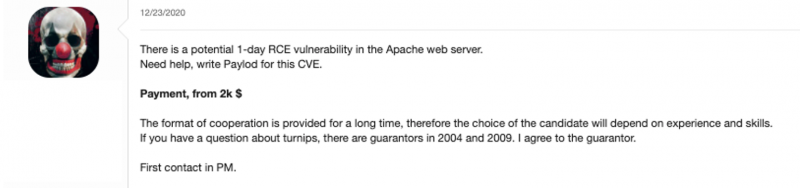
Another request, posted on Dec. 23, 2020, was looking for “a potential 1-day RCE vulnerability” in Apache Web Server: not a surprising find, given that the RiskSense Spotlight Report found that the WordPress and Apache Struts web frameworks were the most-targeted by cybercriminals in 2019.
See Also: Offensive Security Tool: EyeWitness
Trend Micro researchers found that Office and Adobe exploits were most common in English-speaking forums. As of last week, Adobe Acrobat, the world’s leading PDF reader, was under active attack after a vulnerability that could lead to RCE was exploited. That one affected both Windows – one of attackers’ preferred sweet spots – and macOS systems.
Lifecycle of an Exploit
Like most markets, the exploit market has listings for both buyers and sellers. In one such “for sale” pitch, the seller offered two CVEs with a severity rating of 7.5, for the price of $1,000. Another ad offered four CVEs for $30,000 USD, including a loader script, with the added “benefit” of rechecking antivirus detection to make sure that the executable malware hasn’t yet been detected and won’t be blocked, among other services.
After criminals develop an exploit, the next step is to sell it. After it’s in the wild, a vulnerability moves into the stage of public disclosure. Next, the vendor patches the vulnerability. Finally, that vulnerability goes down two paths: if it’s patched that’s it, end of life. If not, the exploit’s still there, waiting to be purchased and set free on whatever unlucky victims haven’t yet patched.
Fuentes gave a few case studies that illustrate the lifecycle. Below is a timeline depicting one of them: the eight-month lifecycle of CVE-2020-9054: an exploit sold on the XSS cybercriminal forum for $20,000 in February 2020, got written about by cybersecurity journalist Brian Krebs, was publicly disclosed and patched by Microsoft in March 2020, and wound up being exploited by a botnet a month later. That botnet, a variant of the Mirai botnet named Mukashi that targeted Zyxel network-attached storage (NAS) devices, allowed threat actors to remotely compromise and control devices.

The lifecycle of CVE-2020-9054, the vulnerability that got exploited by the Mukashi botnet. Source: Trend Micro
See Also: Hacking Stories: Xbox Underground
Five months after it was patched, in August 2020, another forum post requested an exploit, offering the bargain basement payment of $2,000: a tenth of the original exploit.
Where to Start When You Can’t Patch ‘Em All
“You can’t possibly patch all the CVEs each year,” Fuentes said. So how do you prioritize?
She recommended factoring in the desirability of an exploit when making patching plans. Don’t just pick your battles based on vulnerability severity. Rather, factor in what crooks want to use and what they can buy. Keep in mind that Microsoft and Adobe exploits are hot-ticket items: “It’s simply unrealistic to think you can patch everything,” Fuentes noted. “Focus on what hackers like to focus on: Microsoft and Adobe.”
Also bear in mind that virtual patching – a security policy enforcement layer that prevents the exploitation of a known vulnerability by analyzing transactions and by intercepting attacks in transit to keep malicious traffic from reaching the web application, all without having to take the time to modify the actual source code of an app itself – can buy additional time, she recommended.
Another factor in the “what to patch first” equation is the fact that vulnerability prices drop over time, but valuable exploits still stay valuable “longer than most expect,” Fuentes pointed out. “Patching yesterday’s popular vulnerability can be more important than today’s critical one,” she said.
Source: threatpost.com