Microsoft confirms Azure, Outlook, OneDrive outages caused by Layer 7 DDoS Attacks
Microsoft has recently confirmed that the outages experienced by Azure, Outlook, and OneDrive web portals were the result of Layer 7 DDoS attacks targeting the company’s services. The attacks have been attributed to a threat actor known as Storm-1359, who identifies themselves as Anonymous Sudan.
These disruptive events occurred at the beginning of June, with Outlook.com’s web portal being targeted on June 7th, followed by OneDrive on June 8th, and the Microsoft Azure Portal on June 9th. Initially, Microsoft did not explicitly disclose that they were facing DDoS attacks but hinted at it by mentioning the application of load balancing processes to mitigate the issues.
In a recent preliminary root cause report, Microsoft further alluded to the DDoS attacks, noting that a significant spike in network traffic was responsible for the Azure outage. According to Microsoft, the spike impacted their ability to manage traffic to the affected sites, resulting in accessibility issues for customers.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Confirmed Attacks
In a post from the Microsoft Security Response Center, the company has now officially confirmed that the outages were indeed caused by a Layer 7 DDoS attack conducted by the threat actor known as Storm-1359. The attacks started in early June, and Microsoft promptly launched an investigation, subsequently tracking the ongoing DDoS activity associated with Storm-1359. Microsoft has stated that these attacks likely involve the use of multiple virtual private servers (VPS), rented cloud infrastructure, open proxies, and DDoS tools.
Importantly, Microsoft has reassured users that there is no evidence indicating the compromise or unauthorized access to customer data.
A Layer 7 DDoS attack targets the application level by overwhelming services with an enormous volume of requests, leading to service slowdown or unresponsiveness. In this case, Anonymous Sudan employs three types of Layer 7 DDoS attacks: HTTP(S) flood attacks, Cache bypass, and Slowloris. Each method overwhelms the targeted web service by exhausting available connections, rendering them unable to accept new requests.
Trending: Offensive Security Tool: PhoneSploit Pro
Anonymous Sudan
Anonymous Sudan, also tracked as Storm-1359 by Microsoft, emerged in January 2023, announcing their intention to conduct attacks against countries opposing Sudan. Since then, the group has targeted various organizations and government agencies globally, launching DDoS attacks and leaking stolen data.
In May, the group escalated its activities by targeting large organizations and demanding payments to cease the attacks. Scandinavian Airlines (SAS) was among the initial targets, with the threat actors demanding a payment of $3,500 to halt the DDoS attacks. Subsequently, the group focused on American companies, such as Tinder, Lyft, and several hospitals across the United States.
In June, Anonymous Sudan turned its attention to Microsoft, launching DDoS attacks on web-accessible portals for Outlook, Azure, and OneDrive. The group demanded a payment of $1 million to stop the attacks and claimed that Microsoft had failed to repel their prolonged assault.
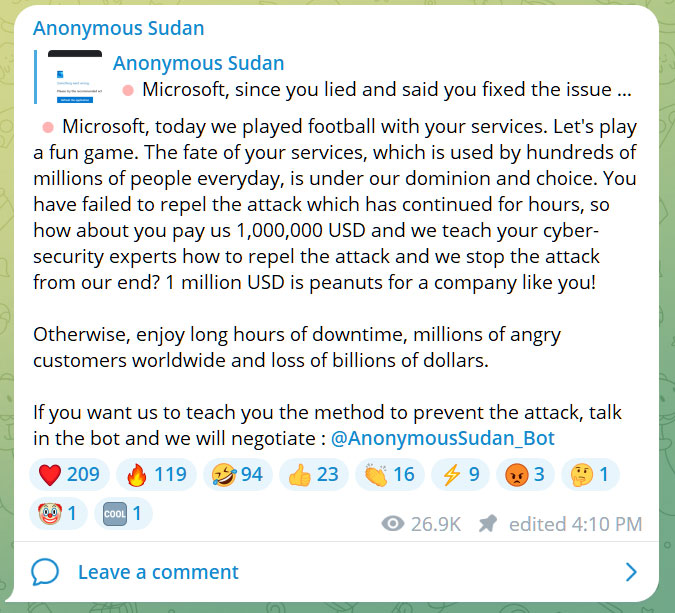 Anonymous Sudan claiming attack on Microsoft Azure
Anonymous Sudan claiming attack on Microsoft Azure
While Anonymous Sudan cited the USA’s involvement in Sudanese politics as the reason for their attacks on Outlook, cybersecurity researchers have raised suspicions of a false flag and potential links to Russia. Recent statements from Anonymous Sudan regarding the formation of a “DARKNET parliament” involving pro-Russia groups like KILLNET and “REvil” further support these concerns. The group has even threatened to impose sanctions on European banking transfer systems, although no attacks have been reported yet.
Considering the demonstrated capabilities and resources at the disposal of Anonymous Sudan, financial institutions should remain vigilant and prepared for potential disruptions in the face of this evolving threat.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












